I saw a few people have had similar issues so I read their threads over a few times and made some changes on my UTM before posting this.
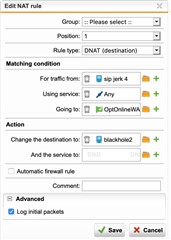
I've been watching as a particular IP tries to brute-force its way into my Asterisk sever despite firewall rules blocking it. After seeing the other posts, I created a static blackhole route to 224.0.0.5, then created a DNAT for traffic to my WAN port from the offending IP to go to 224.0.0.5, and waited. Just saw another one at the Asterisk server.
Any suggestions? My software is at 9.701-6.
thanks
Kevin
This thread was automatically locked due to age.