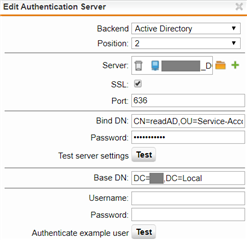
We currently use LDAP (/adirectory) over port 389 with our domain controller for the recipient verification filter in the SMTP module. Since Microsoft will start enforcing LDAP signing in March, I've created a new authentication server entry with port 636 and SSL:
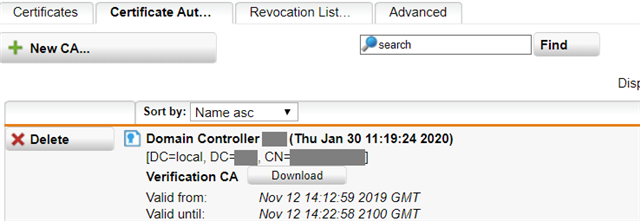
I also imported the CA certificate from our domain controller (which doubles as an internal CA):
The server test passes but when I switch to the new configuration, mails don't get rejected anymore. From this thread I've gathered that it was still a known issue in 2016:
https://community.sophos.com/products/unified-threat-management/f/mail-protection-smtp-pop3-antispam-and-antivirus/83298/ldaps-and-smtp-active-directory-recipient-verification
I was gonna check if it's still an issue but the page for LDAP (under "Sophos UTM 9 > Authentication > LDAP") is not there:
https://community.sophos.com/kb/en-us/124067
Info about MS patch:
https://support.microsoft.com/en-us/help/4520412/2020-ldap-channel-binding-and-ldap-signing-requirement-for-windows
This thread was automatically locked due to age.