Hi for all,
In first time excuse fo my bad english.
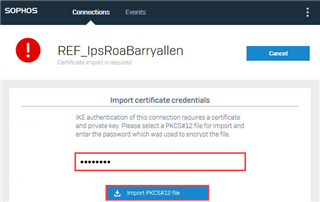
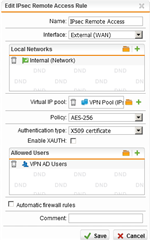
So, I've a problem to estabilish a vpn client connection, base on x509 certificate between sophos connect and utm 9.700-5.
this is the log I'm masquerate the pubblic ip with same ***:
2020:01:02-13:54:09 Firewall pluto[6363]: |
2020:01:02-13:54:09 Firewall pluto[6363]: | *received 28 bytes from ***.***.***.***.66:11201 on ppp0
2020:01:02-13:54:09 Firewall pluto[6363]: packet from ***.***.***.***:11201: length of ISAKMP Message is smaller than minimum
2020:01:02-13:54:09 Firewall pluto[6363]: packet from ***.***.***.***:11201: sending notification PAYLOAD_MALFORMED to ***.***.***.***:11201
2020:01:02-13:54:09 Firewall pluto[6363]: | **emit ISAKMP Message:
2020:01:02-13:54:09 Firewall pluto[6363]: | initiator cookie:
2020:01:02-13:54:09 Firewall pluto[6363]: | 00 01 02 03 04 05 06 07
2020:01:02-13:54:09 Firewall pluto[6363]: | responder cookie:
2020:01:02-13:54:09 Firewall pluto[6363]: | 00 00 00 00 00 00 00 00
2020:01:02-13:54:09 Firewall pluto[6363]: | next payload type: ISAKMP_NEXT_N
2020:01:02-13:54:09 Firewall pluto[6363]: | ISAKMP version: ISAKMP Version 1.0
2020:01:02-13:54:09 Firewall pluto[6363]: | exchange type: ISAKMP_XCHG_INFO
2020:01:02-13:54:09 Firewall pluto[6363]: | flags: none
2020:01:02-13:54:09 Firewall pluto[6363]: | message ID: 00 00 00 00
2020:01:02-13:54:09 Firewall pluto[6363]: | ***emit ISAKMP Notification Payload:
2020:01:02-13:54:09 Firewall pluto[6363]: | next payload type: ISAKMP_NEXT_NONE
2020:01:02-13:54:09 Firewall pluto[6363]: | DOI: ISAKMP_DOI_IPSEC
2020:01:02-13:54:09 Firewall pluto[6363]: | protocol ID: 1
2020:01:02-13:54:09 Firewall pluto[6363]: | SPI size: 0
2020:01:02-13:54:09 Firewall pluto[6363]: | Notify Message Type: PAYLOAD_MALFORMED
2020:01:02-13:54:09 Firewall pluto[6363]: | emitting 0 raw bytes of spi into ISAKMP Notification Payload
2020:01:02-13:54:09 Firewall pluto[6363]: | spi
2020:01:02-13:54:09 Firewall pluto[6363]: | emitting length of ISAKMP Notification Payload: 12
2020:01:02-13:54:09 Firewall pluto[6363]: | emitting length of ISAKMP Message: 40
2020:01:02-13:54:09 Firewall pluto[6363]: | next event EVENT_REINIT_SECRET in 528 seconds
2020:01:02-13:54:10 Firewall pluto[6363]: |
2020:01:02-13:54:10 Firewall pluto[6363]: | *received 180 bytes from ***.***.***.***:11202 on ppp0
2020:01:02-13:54:10 Firewall pluto[6363]: | **parse ISAKMP Message:
2020:01:02-13:54:10 Firewall pluto[6363]: | initiator cookie:
2020:01:02-13:54:10 Firewall pluto[6363]: | d9 2e 70 16 90 bc 69 c7
2020:01:02-13:54:10 Firewall pluto[6363]: | responder cookie:
2020:01:02-13:54:10 Firewall pluto[6363]: | 00 00 00 00 00 00 00 00
2020:01:02-13:54:10 Firewall pluto[6363]: | next payload type: ISAKMP_NEXT_SA
2020:01:02-13:54:10 Firewall pluto[6363]: | ISAKMP version: ISAKMP Version 1.0
2020:01:02-13:54:10 Firewall pluto[6363]: | exchange type: ISAKMP_XCHG_IDPROT
2020:01:02-13:54:10 Firewall pluto[6363]: | flags: none
2020:01:02-13:54:10 Firewall pluto[6363]: | message ID: 00 00 00 00
2020:01:02-13:54:10 Firewall pluto[6363]: | length: 180
2020:01:02-13:54:10 Firewall pluto[6363]: | ***parse ISAKMP Security Association Payload:
2020:01:02-13:54:10 Firewall pluto[6363]: | next payload type: ISAKMP_NEXT_VID
2020:01:02-13:54:10 Firewall pluto[6363]: | length: 56
2020:01:02-13:54:10 Firewall pluto[6363]: | DOI: ISAKMP_DOI_IPSEC
2020:01:02-13:54:10 Firewall pluto[6363]: | ***parse ISAKMP Vendor ID Payload:
2020:01:02-13:54:10 Firewall pluto[6363]: | next payload type: ISAKMP_NEXT_VID
2020:01:02-13:54:10 Firewall pluto[6363]: | length: 12
2020:01:02-13:54:10 Firewall pluto[6363]: | ***parse ISAKMP Vendor ID Payload:
2020:01:02-13:54:10 Firewall pluto[6363]: | next payload type: ISAKMP_NEXT_VID
2020:01:02-13:54:10 Firewall pluto[6363]: | length: 20
2020:01:02-13:54:10 Firewall pluto[6363]: | ***parse ISAKMP Vendor ID Payload:
2020:01:02-13:54:10 Firewall pluto[6363]: | next payload type: ISAKMP_NEXT_VID
2020:01:02-13:54:10 Firewall pluto[6363]: | length: 24
2020:01:02-13:54:10 Firewall pluto[6363]: | ***parse ISAKMP Vendor ID Payload:
2020:01:02-13:54:10 Firewall pluto[6363]: | next payload type: ISAKMP_NEXT_VID
2020:01:02-13:54:10 Firewall pluto[6363]: | length: 20
2020:01:02-13:54:10 Firewall pluto[6363]: | ***parse ISAKMP Vendor ID Payload:
2020:01:02-13:54:10 Firewall pluto[6363]: | next payload type: ISAKMP_NEXT_NONE
2020:01:02-13:54:10 Firewall pluto[6363]: | length: 20
2020:01:02-13:54:10 Firewall pluto[6363]: packet from ***.***.***.***:11202: received Vendor ID payload [XAUTH]
2020:01:02-13:54:10 Firewall pluto[6363]: packet from ***.***.***.***:11202: received Vendor ID payload [Dead Peer Detection]
2020:01:02-13:54:10 Firewall pluto[6363]: packet from ***.***.***.***:11202: ignoring Vendor ID payload [FRAGMENTATION 80000000]
2020:01:02-13:54:10 Firewall pluto[6363]: packet from ***.***.***.***:11202: received Vendor ID payload [RFC 3947]
2020:01:02-13:54:10 Firewall pluto[6363]: packet from ***.***.***.***:11202: ignoring Vendor ID payload [draft-ietf-ipsec-nat-t-ike-02_n]
2020:01:02-13:54:10 Firewall pluto[6363]: | ****parse IPsec DOI SIT:
2020:01:02-13:54:10 Firewall pluto[6363]: | IPsec DOI SIT: SIT_IDENTITY_ONLY
2020:01:02-13:54:10 Firewall pluto[6363]: | ****parse ISAKMP Proposal Payload:
2020:01:02-13:54:10 Firewall pluto[6363]: | next payload type: ISAKMP_NEXT_NONE
2020:01:02-13:54:10 Firewall pluto[6363]: | length: 44
2020:01:02-13:54:10 Firewall pluto[6363]: | proposal number: 0
2020:01:02-13:54:10 Firewall pluto[6363]: | protocol ID: PROTO_ISAKMP
2020:01:02-13:54:10 Firewall pluto[6363]: | SPI size: 0
2020:01:02-13:54:10 Firewall pluto[6363]: | number of transforms: 1
2020:01:02-13:54:10 Firewall pluto[6363]: | *****parse ISAKMP Transform Payload (ISAKMP):
2020:01:02-13:54:10 Firewall pluto[6363]: | next payload type: ISAKMP_NEXT_NONE
2020:01:02-13:54:10 Firewall pluto[6363]: | length: 36
2020:01:02-13:54:10 Firewall pluto[6363]: | transform number: 1
2020:01:02-13:54:10 Firewall pluto[6363]: | transform ID: KEY_IKE
2020:01:02-13:54:10 Firewall pluto[6363]: | ******parse ISAKMP Oakley attribute:
2020:01:02-13:54:10 Firewall pluto[6363]: | af+type: OAKLEY_ENCRYPTION_ALGORITHM
2020:01:02-13:54:10 Firewall pluto[6363]: | length/value: 7
2020:01:02-13:54:10 Firewall pluto[6363]: | ******parse ISAKMP Oakley attribute:
2020:01:02-13:54:10 Firewall pluto[6363]: | af+type: OAKLEY_KEY_LENGTH
2020:01:02-13:54:10 Firewall pluto[6363]: | length/value: 256
2020:01:02-13:54:10 Firewall pluto[6363]: | ******parse ISAKMP Oakley attribute:
2020:01:02-13:54:10 Firewall pluto[6363]: | af+type: OAKLEY_HASH_ALGORITHM
2020:01:02-13:54:10 Firewall pluto[6363]: | length/value: 1
2020:01:02-13:54:10 Firewall pluto[6363]: | ******parse ISAKMP Oakley attribute:
2020:01:02-13:54:10 Firewall pluto[6363]: | af+type: OAKLEY_GROUP_DESCRIPTION
2020:01:02-13:54:10 Firewall pluto[6363]: | length/value: 5
2020:01:02-13:54:10 Firewall pluto[6363]: | ******parse ISAKMP Oakley attribute:
2020:01:02-13:54:10 Firewall pluto[6363]: | af+type: OAKLEY_AUTHENTICATION_METHOD
2020:01:02-13:54:10 Firewall pluto[6363]: | length/value: 3
2020:01:02-13:54:10 Firewall pluto[6363]: | ******parse ISAKMP Oakley attribute:
2020:01:02-13:54:10 Firewall pluto[6363]: | af+type: OAKLEY_LIFE_TYPE
2020:01:02-13:54:10 Firewall pluto[6363]: | length/value: 1
2020:01:02-13:54:10 Firewall pluto[6363]: | ******parse ISAKMP Oakley attribute:
2020:01:02-13:54:10 Firewall pluto[6363]: | af+type: OAKLEY_LIFE_DURATION
2020:01:02-13:54:10 Firewall pluto[6363]: | length/value: 8151
2020:01:02-13:54:10 Firewall pluto[6363]: | preparse_isakmp_policy: peer requests PUBKEY authentication
2020:01:02-13:54:10 Firewall pluto[6363]: | instantiated "D_REF_IpsRoaIpsecRemotAcces_AaaUseRpaletti-0" for ***.***.***.***
2020:01:02-13:54:10 Firewall pluto[6363]: | creating state object #13 at 0x8363c18
2020:01:02-13:54:10 Firewall pluto[6363]: | ICOOKIE: d9 2e 70 16 90 bc 69 c7
2020:01:02-13:54:10 Firewall pluto[6363]: | RCOOKIE: fd 6e 9f ea c3 3d 8a f8
2020:01:02-13:54:10 Firewall pluto[6363]: | peer: b2 13 90 42
2020:01:02-13:54:10 Firewall pluto[6363]: | state hash entry 24
2020:01:02-13:54:10 Firewall pluto[6363]: | inserting event EVENT_SO_DISCARD, timeout in 0 seconds for #13
2020:01:02-13:54:10 Firewall pluto[6363]: "D_REF_IpsRoaIpsecRemotAcces_AaaUseRpaletti-0"[13] ***.***.***.***:11202 #13: responding to Main Mode from unknown peer ***.***.***.***:11202
2020:01:02-13:54:10 Firewall pluto[6363]: | **emit ISAKMP Message:
2020:01:02-13:54:10 Firewall pluto[6363]: | initiator cookie:
2020:01:02-13:54:10 Firewall pluto[6363]: | d9 2e 70 16 90 bc 69 c7
2020:01:02-13:54:10 Firewall pluto[6363]: | responder cookie:
2020:01:02-13:54:10 Firewall pluto[6363]: | fd 6e 9f ea c3 3d 8a f8
2020:01:02-13:54:10 Firewall pluto[6363]: | next payload type: ISAKMP_NEXT_SA
2020:01:02-13:54:10 Firewall pluto[6363]: | ISAKMP version: ISAKMP Version 1.0
2020:01:02-13:54:10 Firewall pluto[6363]: | exchange type: ISAKMP_XCHG_IDPROT
2020:01:02-13:54:10 Firewall pluto[6363]: | flags: none
2020:01:02-13:54:10 Firewall pluto[6363]: | message ID: 00 00 00 00
2020:01:02-13:54:10 Firewall pluto[6363]: | ***emit ISAKMP Security Association Payload:
2020:01:02-13:54:10 Firewall pluto[6363]: | next payload type: ISAKMP_NEXT_VID
2020:01:02-13:54:10 Firewall pluto[6363]: | DOI: ISAKMP_DOI_IPSEC
2020:01:02-13:54:10 Firewall pluto[6363]: | *****parse ISAKMP Transform Payload (ISAKMP):
2020:01:02-13:54:10 Firewall pluto[6363]: | next payload type: ISAKMP_NEXT_NONE
2020:01:02-13:54:10 Firewall pluto[6363]: | length: 36
2020:01:02-13:54:10 Firewall pluto[6363]: | transform number: 1
2020:01:02-13:54:10 Firewall pluto[6363]: | transform ID: KEY_IKE
2020:01:02-13:54:10 Firewall pluto[6363]: | ******parse ISAKMP Oakley attribute:
2020:01:02-13:54:10 Firewall pluto[6363]: | af+type: OAKLEY_ENCRYPTION_ALGORITHM
2020:01:02-13:54:10 Firewall pluto[6363]: | length/value: 7
2020:01:02-13:54:10 Firewall pluto[6363]: | [7 is AES_CBC]
2020:01:02-13:54:10 Firewall pluto[6363]: | ******parse ISAKMP Oakley attribute:
2020:01:02-13:54:10 Firewall pluto[6363]: | af+type: OAKLEY_KEY_LENGTH
2020:01:02-13:54:10 Firewall pluto[6363]: | length/value: 256
2020:01:02-13:54:10 Firewall pluto[6363]: | ******parse ISAKMP Oakley attribute:
2020:01:02-13:54:10 Firewall pluto[6363]: | af+type: OAKLEY_HASH_ALGORITHM
2020:01:02-13:54:10 Firewall pluto[6363]: | length/value: 1
2020:01:02-13:54:10 Firewall pluto[6363]: | [1 is HMAC_MD5]
2020:01:02-13:54:10 Firewall pluto[6363]: | ******parse ISAKMP Oakley attribute:
2020:01:02-13:54:10 Firewall pluto[6363]: | af+type: OAKLEY_GROUP_DESCRIPTION
2020:01:02-13:54:10 Firewall pluto[6363]: | length/value: 5
2020:01:02-13:54:10 Firewall pluto[6363]: | [5 is MODP_1536]
2020:01:02-13:54:10 Firewall pluto[6363]: | ******parse ISAKMP Oakley attribute:
2020:01:02-13:54:10 Firewall pluto[6363]: | af+type: OAKLEY_AUTHENTICATION_METHOD
2020:01:02-13:54:10 Firewall pluto[6363]: | length/value: 3
2020:01:02-13:54:10 Firewall pluto[6363]: | [3 is RSA signature]
2020:01:02-13:54:10 Firewall pluto[6363]: | ******parse ISAKMP Oakley attribute:
2020:01:02-13:54:10 Firewall pluto[6363]: | af+type: OAKLEY_LIFE_TYPE
2020:01:02-13:54:10 Firewall pluto[6363]: | length/value: 1
2020:01:02-13:54:10 Firewall pluto[6363]: | [1 is OAKLEY_LIFE_SECONDS]
2020:01:02-13:54:10 Firewall pluto[6363]: | ******parse ISAKMP Oakley attribute:
2020:01:02-13:54:10 Firewall pluto[6363]: | af+type: OAKLEY_LIFE_DURATION
2020:01:02-13:54:10 Firewall pluto[6363]: | length/value: 8151
2020:01:02-13:54:10 Firewall pluto[6363]: | Oakley Transform 1 accepted
2020:01:02-13:54:10 Firewall pluto[6363]: | ****emit IPsec DOI SIT:
2020:01:02-13:54:10 Firewall pluto[6363]: | IPsec DOI SIT: SIT_IDENTITY_ONLY
2020:01:02-13:54:10 Firewall pluto[6363]: | ****emit ISAKMP Proposal Payload:
2020:01:02-13:54:10 Firewall pluto[6363]: | next payload type: ISAKMP_NEXT_NONE
2020:01:02-13:54:10 Firewall pluto[6363]: | proposal number: 0
2020:01:02-13:54:10 Firewall pluto[6363]: | protocol ID: PROTO_ISAKMP
2020:01:02-13:54:10 Firewall pluto[6363]: | SPI size: 0
2020:01:02-13:54:10 Firewall pluto[6363]: | number of transforms: 1
2020:01:02-13:54:10 Firewall pluto[6363]: | *****emit ISAKMP Transform Payload (ISAKMP):
2020:01:02-13:54:10 Firewall pluto[6363]: | next payload type: ISAKMP_NEXT_NONE
2020:01:02-13:54:10 Firewall pluto[6363]: | transform number: 1
2020:01:02-13:54:10 Firewall pluto[6363]: | transform ID: KEY_IKE
2020:01:02-13:54:10 Firewall pluto[6363]: | emitting 28 raw bytes of attributes into ISAKMP Transform Payload (ISAKMP)
2020:01:02-13:54:10 Firewall pluto[6363]: | attributes 80 01 00 07 80 0e 01 00 80 02 00 01 80 04 00 05
2020:01:02-13:54:10 Firewall pluto[6363]: | 80 03 00 03 80 0b 00 01 80 0c 1f d7
2020:01:02-13:54:10 Firewall pluto[6363]: | emitting length of ISAKMP Transform Payload (ISAKMP): 36
2020:01:02-13:54:10 Firewall pluto[6363]: | emitting length of ISAKMP Proposal Payload: 44
2020:01:02-13:54:10 Firewall pluto[6363]: | emitting length of ISAKMP Security Association Payload: 56
2020:01:02-13:54:10 Firewall pluto[6363]: | out_vendorid(): sending [strongSwan]
2020:01:02-13:54:10 Firewall pluto[6363]: | ***emit ISAKMP Vendor ID Payload:
2020:01:02-13:54:10 Firewall pluto[6363]: | next payload type: ISAKMP_NEXT_VID
2020:01:02-13:54:10 Firewall pluto[6363]: | emitting 16 raw bytes of V_ID into ISAKMP Vendor ID Payload
2020:01:02-13:54:10 Firewall pluto[6363]: | V_ID 88 2f e5 6d 6f d2 0d bc 22 51 61 3b 2e be 5b eb
2020:01:02-13:54:10 Firewall pluto[6363]: | emitting length of ISAKMP Vendor ID Payload: 20
2020:01:02-13:54:10 Firewall pluto[6363]: | out_vendorid(): sending [Cisco-Unity]
2020:01:02-13:54:10 Firewall pluto[6363]: | ***emit ISAKMP Vendor ID Payload:
2020:01:02-13:54:10 Firewall pluto[6363]: | next payload type: ISAKMP_NEXT_VID
2020:01:02-13:54:10 Firewall pluto[6363]: | emitting 16 raw bytes of V_ID into ISAKMP Vendor ID Payload
2020:01:02-13:54:10 Firewall pluto[6363]: | V_ID 12 f5 f2 8c 45 71 68 a9 70 2d 9f e2 74 cc 01 00
2020:01:02-13:54:10 Firewall pluto[6363]: | emitting length of ISAKMP Vendor ID Payload: 20
2020:01:02-13:54:10 Firewall pluto[6363]: | out_vendorid(): sending [XAUTH]
2020:01:02-13:54:10 Firewall pluto[6363]: | ***emit ISAKMP Vendor ID Payload:
2020:01:02-13:54:10 Firewall pluto[6363]: | next payload type: ISAKMP_NEXT_VID
2020:01:02-13:54:10 Firewall pluto[6363]: | emitting 8 raw bytes of V_ID into ISAKMP Vendor ID Payload
2020:01:02-13:54:10 Firewall pluto[6363]: | V_ID 09 00 26 89 df d6 b7 12
2020:01:02-13:54:10 Firewall pluto[6363]: | emitting length of ISAKMP Vendor ID Payload: 12
2020:01:02-13:54:10 Firewall pluto[6363]: | out_vendorid(): sending [Dead Peer Detection]
2020:01:02-13:54:10 Firewall pluto[6363]: | ***emit ISAKMP Vendor ID Payload:
2020:01:02-13:54:10 Firewall pluto[6363]: | next payload type: ISAKMP_NEXT_VID
2020:01:02-13:54:10 Firewall pluto[6363]: | emitting 16 raw bytes of V_ID into ISAKMP Vendor ID Payload
2020:01:02-13:54:10 Firewall pluto[6363]: | V_ID af ca d7 13 68 a1 f1 c9 6b 86 96 fc 77 57 01 00
2020:01:02-13:54:10 Firewall pluto[6363]: | emitting length of ISAKMP Vendor ID Payload: 20
2020:01:02-13:54:10 Firewall pluto[6363]: | out_vendorid(): sending [RFC 3947]
2020:01:02-13:54:10 Firewall pluto[6363]: | ***emit ISAKMP Vendor ID Payload:
2020:01:02-13:54:10 Firewall pluto[6363]: | next payload type: ISAKMP_NEXT_NONE
2020:01:02-13:54:10 Firewall pluto[6363]: | emitting 16 raw bytes of V_ID into ISAKMP Vendor ID Payload
2020:01:02-13:54:10 Firewall pluto[6363]: | V_ID 4a 13 1c 81 07 03 58 45 5c 57 28 f2 0e 95 45 2f
2020:01:02-13:54:10 Firewall pluto[6363]: | emitting length of ISAKMP Vendor ID Payload: 20
2020:01:02-13:54:10 Firewall pluto[6363]: | emitting length of ISAKMP Message: 176
2020:01:02-13:54:10 Firewall pluto[6363]: | inserting event EVENT_RETRANSMIT, timeout in 10 seconds for #13
2020:01:02-13:54:10 Firewall pluto[6363]: | next event EVENT_RETRANSMIT in 10 seconds for #13
2020:01:02-13:54:10 Firewall pluto[6363]: |
2020:01:02-13:54:10 Firewall pluto[6363]: | *received 300 bytes from ***.***.***.***:11202 on ppp0
2020:01:02-13:54:10 Firewall pluto[6363]: | **parse ISAKMP Message:
2020:01:02-13:54:10 Firewall pluto[6363]: | initiator cookie:
2020:01:02-13:54:10 Firewall pluto[6363]: | d9 2e 70 16 90 bc 69 c7
2020:01:02-13:54:10 Firewall pluto[6363]: | responder cookie:
2020:01:02-13:54:10 Firewall pluto[6363]: | fd 6e 9f ea c3 3d 8a f8
2020:01:02-13:54:10 Firewall pluto[6363]: | next payload type: ISAKMP_NEXT_KE
2020:01:02-13:54:10 Firewall pluto[6363]: | ISAKMP version: ISAKMP Version 1.0
2020:01:02-13:54:10 Firewall pluto[6363]: | exchange type: ISAKMP_XCHG_IDPROT
2020:01:02-13:54:10 Firewall pluto[6363]: | flags: none
2020:01:02-13:54:10 Firewall pluto[6363]: | message ID: 00 00 00 00
2020:01:02-13:54:10 Firewall pluto[6363]: | length: 300
2020:01:02-13:54:10 Firewall pluto[6363]: | ICOOKIE: d9 2e 70 16 90 bc 69 c7
2020:01:02-13:54:10 Firewall pluto[6363]: | RCOOKIE: fd 6e 9f ea c3 3d 8a f8
2020:01:02-13:54:10 Firewall pluto[6363]: | peer: b2 13 90 42
2020:01:02-13:54:10 Firewall pluto[6363]: | state hash entry 24
2020:01:02-13:54:10 Firewall pluto[6363]: | state object #13 found, in STATE_MAIN_R1
2020:01:02-13:54:10 Firewall pluto[6363]: | ***parse ISAKMP Key Exchange Payload:
2020:01:02-13:54:10 Firewall pluto[6363]: | next payload type: ISAKMP_NEXT_NONCE
2020:01:02-13:54:10 Firewall pluto[6363]: | length: 196
2020:01:02-13:54:10 Firewall pluto[6363]: | ***parse ISAKMP Nonce Payload:
2020:01:02-13:54:10 Firewall pluto[6363]: | next payload type: ISAKMP_NEXT_NAT-D
2020:01:02-13:54:10 Firewall pluto[6363]: | length: 36
2020:01:02-13:54:10 Firewall pluto[6363]: | ***parse ISAKMP NAT-D Payload:
2020:01:02-13:54:10 Firewall pluto[6363]: | next payload type: ISAKMP_NEXT_NAT-D
2020:01:02-13:54:10 Firewall pluto[6363]: | length: 20
2020:01:02-13:54:10 Firewall pluto[6363]: | ***parse ISAKMP NAT-D Payload:
2020:01:02-13:54:10 Firewall pluto[6363]: | next payload type: ISAKMP_NEXT_NONE
2020:01:02-13:54:10 Firewall pluto[6363]: | length: 20
2020:01:02-13:54:10 Firewall pluto[6363]: | **emit ISAKMP Message:
2020:01:02-13:54:10 Firewall pluto[6363]: | initiator cookie:
2020:01:02-13:54:10 Firewall pluto[6363]: | d9 2e 70 16 90 bc 69 c7
2020:01:02-13:54:10 Firewall pluto[6363]: | responder cookie:
2020:01:02-13:54:10 Firewall pluto[6363]: | fd 6e 9f ea c3 3d 8a f8
2020:01:02-13:54:10 Firewall pluto[6363]: | next payload type: ISAKMP_NEXT_KE
2020:01:02-13:54:10 Firewall pluto[6363]: | ISAKMP version: ISAKMP Version 1.0
2020:01:02-13:54:10 Firewall pluto[6363]: | exchange type: ISAKMP_XCHG_IDPROT
2020:01:02-13:54:10 Firewall pluto[6363]: | flags: none
2020:01:02-13:54:10 Firewall pluto[6363]: | message ID: 00 00 00 00
2020:01:02-13:54:10 Firewall pluto[6363]: "D_REF_IpsRoaIpsecRemotAcces_AaaUseRpaletti-0"[13] ***.***.***.***:11202 #13: NAT-Traversal: Result using RFC 3947: peer is NATed
2020:01:02-13:54:10 Firewall pluto[6363]: | inserting event EVENT_NAT_T_KEEPALIVE, timeout in 60 seconds
2020:01:02-13:54:10 Firewall pluto[6363]: | size of DH secret exponent: 1528 bits
2020:01:02-13:54:10 Firewall pluto[6363]: | ***emit ISAKMP Key Exchange Payload:
2020:01:02-13:54:10 Firewall pluto[6363]: | next payload type: ISAKMP_NEXT_NONCE
2020:01:02-13:54:10 Firewall pluto[6363]: | emitting 192 raw bytes of keyex value into ISAKMP Key Exchange Payload
2020:01:02-13:54:10 Firewall pluto[6363]: | keyex value 02 aa 8f eb 20 1e d3 9f 44 09 6c 0c b9 19 6b ee
2020:01:02-13:54:10 Firewall pluto[6363]: | 12 de 5c c9 bd 42 9c f7 0b be 18 b5 bc ea e7 ab
2020:01:02-13:54:10 Firewall pluto[6363]: | f0 a8 70 3d a9 5d 3a 56 8a ce ec af 0d 7d 8d d3
2020:01:02-13:54:10 Firewall pluto[6363]: | 1d 69 49 0c 6d 78 b2 26 38 35 a4 52 d2 da 81 ef
2020:01:02-13:54:10 Firewall pluto[6363]: | d9 5a 35 56 81 85 4a f4 b2 5b 07 01 e2 64 07 be
2020:01:02-13:54:10 Firewall pluto[6363]: | 56 d7 21 eb 43 2b e3 91 17 a6 d2 03 a9 3e 3a 65
2020:01:02-13:54:10 Firewall pluto[6363]: | 8c e2 dd 46 9d 53 5d 9c 71 e0 03 6d aa 68 af f2
2020:01:02-13:54:10 Firewall pluto[6363]: | a9 ed 13 70 de ff ac e7 48 3a 60 e7 2c 50 33 0a
2020:01:02-13:54:10 Firewall pluto[6363]: | 73 27 29 aa 21 13 d3 5e 8a 0d 05 1b 15 b1 e2 d3
2020:01:02-13:54:10 Firewall pluto[6363]: | d2 c9 e1 ec 53 9e 14 71 bf c0 77 d2 27 fd df 1b
2020:01:02-13:54:10 Firewall pluto[6363]: | 78 a7 de 18 5e 90 8c 93 77 a0 de 39 44 49 77 49
2020:01:02-13:54:10 Firewall pluto[6363]: | 56 46 8c 4d d6 11 4c 65 3f 56 4b 38 69 1c cf c5
2020:01:02-13:54:10 Firewall pluto[6363]: | emitting length of ISAKMP Key Exchange Payload: 196
2020:01:02-13:54:10 Firewall pluto[6363]: | ***emit ISAKMP Nonce Payload:
2020:01:02-13:54:10 Firewall pluto[6363]: | next payload type: ISAKMP_NEXT_NAT-D
2020:01:02-13:54:10 Firewall pluto[6363]: | emitting 16 raw bytes of Nr into ISAKMP Nonce Payload
2020:01:02-13:54:10 Firewall pluto[6363]: | Nr 7e b9 4e 58 9c bf cb 6e 6a b2 f1 57 47 07 86 f6
2020:01:02-13:54:10 Firewall pluto[6363]: | emitting length of ISAKMP Nonce Payload: 20
2020:01:02-13:54:10 Firewall pluto[6363]: | sending NATD payloads
2020:01:02-13:54:10 Firewall pluto[6363]: | ***emit ISAKMP NAT-D Payload:
2020:01:02-13:54:10 Firewall pluto[6363]: | next payload type: ISAKMP_NEXT_NAT-D
2020:01:02-13:54:10 Firewall pluto[6363]: | emitting 16 raw bytes of NAT-D into ISAKMP NAT-D Payload
2020:01:02-13:54:10 Firewall pluto[6363]: | NAT-D b4 d3 36 19 f2 ab f3 27 94 ae 4a 00 d7 b1 8a 1c
2020:01:02-13:54:10 Firewall pluto[6363]: | emitting length of ISAKMP NAT-D Payload: 20
2020:01:02-13:54:10 Firewall pluto[6363]: | ***emit ISAKMP NAT-D Payload:
2020:01:02-13:54:10 Firewall pluto[6363]: | next payload type: ISAKMP_NEXT_NONE
2020:01:02-13:54:10 Firewall pluto[6363]: | emitting 16 raw bytes of NAT-D into ISAKMP NAT-D Payload
2020:01:02-13:54:10 Firewall pluto[6363]: | NAT-D e4 65 dd 3f a2 f6 7a 4b 2c 00 01 d8 61 70 4a 53
2020:01:02-13:54:10 Firewall pluto[6363]: | emitting length of ISAKMP NAT-D Payload: 20
2020:01:02-13:54:10 Firewall pluto[6363]: | emitting length of ISAKMP Message: 284
2020:01:02-13:54:10 Firewall pluto[6363]: | inserting event EVENT_RETRANSMIT, timeout in 10 seconds for #13
2020:01:02-13:54:10 Firewall pluto[6363]: | next event EVENT_RETRANSMIT in 10 seconds for #13
2020:01:02-13:54:10 Firewall pluto[6363]: |
2020:01:02-13:54:10 Firewall pluto[6363]: | *received 92 bytes from ***.***.***.***:23924 on ppp0
2020:01:02-13:54:10 Firewall pluto[6363]: | **parse ISAKMP Message:
2020:01:02-13:54:10 Firewall pluto[6363]: | initiator cookie:
2020:01:02-13:54:10 Firewall pluto[6363]: | d9 2e 70 16 90 bc 69 c7
2020:01:02-13:54:10 Firewall pluto[6363]: | responder cookie:
2020:01:02-13:54:10 Firewall pluto[6363]: | fd 6e 9f ea c3 3d 8a f8
2020:01:02-13:54:10 Firewall pluto[6363]: | next payload type: ISAKMP_NEXT_HASH
2020:01:02-13:54:10 Firewall pluto[6363]: | ISAKMP version: ISAKMP Version 1.0
2020:01:02-13:54:10 Firewall pluto[6363]: | exchange type: ISAKMP_XCHG_INFO
2020:01:02-13:54:10 Firewall pluto[6363]: | flags: ISAKMP_FLAG_ENCRYPTION
2020:01:02-13:54:10 Firewall pluto[6363]: | message ID: fb 9f 7e 44
2020:01:02-13:54:10 Firewall pluto[6363]: | length: 92
2020:01:02-13:54:10 Firewall pluto[6363]: | ICOOKIE: d9 2e 70 16 90 bc 69 c7
2020:01:02-13:54:10 Firewall pluto[6363]: | RCOOKIE: fd 6e 9f ea c3 3d 8a f8
2020:01:02-13:54:10 Firewall pluto[6363]: | peer: b2 13 90 42
2020:01:02-13:54:10 Firewall pluto[6363]: | state hash entry 24
2020:01:02-13:54:10 Firewall pluto[6363]: | state object #13 found, in STATE_MAIN_R2
2020:01:02-13:54:10 Firewall pluto[6363]: | ***parse ISAKMP Hash Payload:
2020:01:02-13:54:10 Firewall pluto[6363]: | next payload type: ISAKMP_NEXT_N
2020:01:02-13:54:10 Firewall pluto[6363]: | length: 20
2020:01:02-13:54:10 Firewall pluto[6363]: | ***parse ISAKMP Notification Payload:
2020:01:02-13:54:10 Firewall pluto[6363]: | next payload type: ISAKMP_NEXT_NONE
2020:01:02-13:54:10 Firewall pluto[6363]: | length: 28
2020:01:02-13:54:10 Firewall pluto[6363]: | DOI: ISAKMP_DOI_IPSEC
2020:01:02-13:54:10 Firewall pluto[6363]: | protocol ID: 1
2020:01:02-13:54:10 Firewall pluto[6363]: | SPI size: 16
2020:01:02-13:54:10 Firewall pluto[6363]: | Notify Message Type: AUTHENTICATION_FAILED
2020:01:02-13:54:10 Firewall pluto[6363]: | removing 16 bytes of padding
2020:01:02-13:54:10 Firewall pluto[6363]: | NAT-T: new mapping ***.***.***.***:11202/23924)
2020:01:02-13:54:10 Firewall pluto[6363]: "D_REF_IpsRoaIpsecRemotAcces_AaaUseRpaletti-0"[13] ***.***.***.***:23924 #13: ignoring informational payload, type AUTHENTICATION_FAILED
2020:01:02-13:54:10 Firewall pluto[6363]: | info: d9 2e 70 16 90 bc 69 c7 fd 6e 9f ea c3 3d 8a f8
2020:01:02-13:54:10 Firewall pluto[6363]: | next event EVENT_RETRANSMIT in 10 seconds for #13
2020:01:02-13:54:20 Firewall pluto[6363]: |
2020:01:02-13:54:20 Firewall pluto[6363]: | *time to handle event
2020:01:02-13:54:20 Firewall pluto[6363]: | event after this is EVENT_NAT_T_KEEPALIVE in 50 seconds
2020:01:02-13:54:20 Firewall pluto[6363]: | handling event EVENT_RETRANSMIT for ***.***.***.*** "D_REF_IpsRoaIpsecRemotAcces_AaaUseRpaletti-0" #13
2020:01:02-13:54:20 Firewall pluto[6363]: | inserting event EVENT_RETRANSMIT, timeout in 20 seconds for #13
2020:01:02-13:54:20 Firewall pluto[6363]: | next event EVENT_RETRANSMIT in 20 seconds for #13
2020:01:02-13:54:40 Firewall pluto[6363]: |
2020:01:02-13:54:40 Firewall pluto[6363]: | *time to handle event
2020:01:02-13:54:40 Firewall pluto[6363]: | event after this is EVENT_NAT_T_KEEPALIVE in 30 seconds
2020:01:02-13:54:40 Firewall pluto[6363]: | handling event EVENT_RETRANSMIT for ***.***.***.*** "D_REF_IpsRoaIpsecRemotAcces_AaaUseRpaletti-0" #13
2020:01:02-13:54:40 Firewall pluto[6363]: | inserting event EVENT_RETRANSMIT, timeout in 40 seconds for #13
2020:01:02-13:54:40 Firewall pluto[6363]: | next event EVENT_NAT_T_KEEPALIVE in 30 seconds
Can you help me?
Best regards,
Roberto
This thread was automatically locked due to age.