Hello,
I would think this happens often but I cannot seem to find a solution.
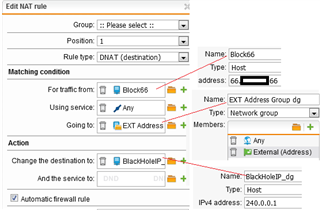
I have an old VPN IPsec (UTM 9x ) tunnel that my side has gone away and is disabled. But the remote side is still sending packets trying to connect.
What is the best way to stop this traffic from filling up my Active IPsec logs ?
I tried a rule to drop or reject the Public IP that traffic is coming from but it does not seem to have any affect.
And yes - I have repeatedly asked the remote end to turn down their vpn - but they either do not know how or just refuse.
This thread was automatically locked due to age.