Hi,
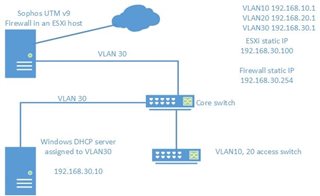
I have configured the setup mentioned in following drawing with Cisco 3650 core switch and two Cisco 2960 switches. After configuring ip route 0.0.0.0 0.0.0.0 192.168.30.254 on core switch, vlan 30 is able to access internet while other vlans couldn't. Could someone please say what seems to be the issue preventing vlan 10 and 20 from accessing internet?
DHCP server and inter-vlan routing is working. I've installed Sophos UTM v9 on a ESXi host
This thread was automatically locked due to age.