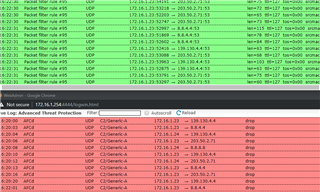
Hi folks, I have turned on the advanced threat protection on my UTM9, having done so I am now getting alot of alerts regading C2\Generic A traffic from my primary and seconday domain controllers, as normal these units are also our internal DNS hosts.
I have run the Sophos virus removal tool against both servers and they have come up clean, I have also tried to add the external DNS servers as exceptions and still getting alerts constantly (The DNS hosts are Google and telstra, our ISP and largest Telco in Australia)
As you can see plenty of traffic is fine, however some is getting flagged
Thanks
Guy
This thread was automatically locked due to age.