Hi All,
I am setting up a VPN to a new site with a cisco 887 and UTM 9
I dont have full control over the other end but can get things changed if needed
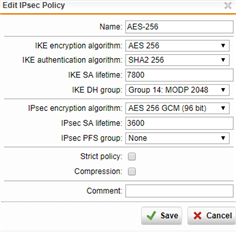
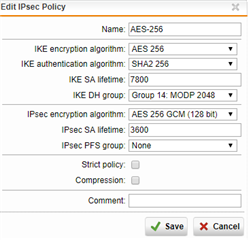
UTM SETUP IS
Cisco Setup
Encryption: aes 256
Hash : sha256
DH Group : group 14
isakmp pre share key :
from the log
This thread was automatically locked due to age.