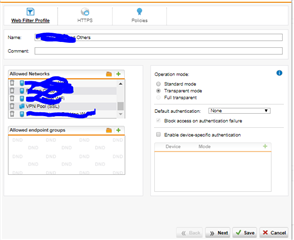
Hi Guys,
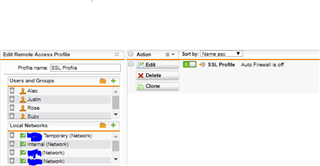
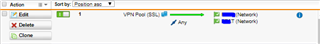
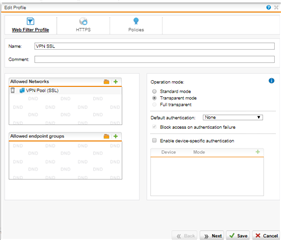
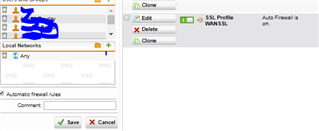
Recently we've set up the SSL VPN Connection in our office. We just want to ask something cause right now we are completely puzzled out by configuring the Sophos UTM9 for SSL VPN. We configured it successfully and was able to install the SSL VPN through the User Portal, but we want to know is, is it possible to to implement the Web Filtering inside the SSL VPN? cause we want some users to access the SSL VPN at home at the same time they can use the network in our office when they are connected to the VPN. Please see screen shot below to help us.
Please help us understand and help us
Thanks
-JSigz
This thread was automatically locked due to age.