Hi to all
I am in process of redesign of my home network to adding UTM to équation.
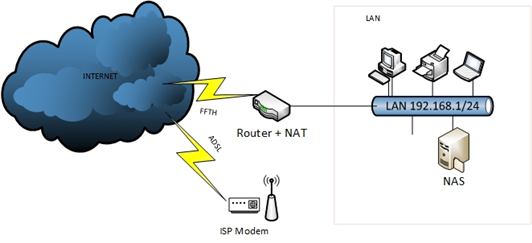
All device are managed with 10gbe (fiber) or 1gbe connection (RJ45)
I'm connected with FFTH, bandwidth is 100 Mbps upload/download, but it can be possible to upgrade it to Gigabyte soon.
I use an ADSL connexion as backup (no failover in place now)
My current setup is like this :
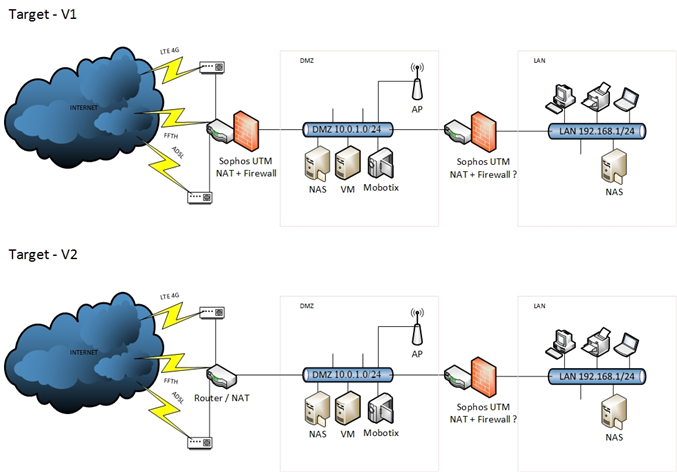
And this is what i plan to made :
I have some few technical interrogation
1. I dunno if Sophos UTM can replace a routeur with NAT function.
Does UTM can do Router + NAT + firewall role ? If it do NAT, is it activate by default or i need to do something ?
2. Does Sophos UTM can handle failover connexion with multiple WAN connexion ?
For example, if FFTH connexion is down, does it can switch to ADSL, if ADSL is down, switch to LTE, and if ADSL is back, switch for LTE to ADSL, and FFTH is back, switch from ADSL to FFTH ?
If not, what kind of device do i need to manage three wan connexion in front of UTM ?
3. Does i need to have NAT + Firewall feature between DMZ zone and LAN zone ?
Better secure or not usefull ?
4. I plan to use 1U Rack form chassis to install UTM, Dell R220 (E3 v3 CPU) or Dell R230 (E3 v5 CPU) seems interesting.
I'm currently testing R220 and it seems to work properly, i just put it on my and use it to filter all my day to day action and prepare the setup properly.
To isolate LAN and DMZ i will to purchase one more to have both UTM.
I would like some advise to choose the best hardware components.
I think that i need to upgrade the network interface to 10Gbe, what is the best Ethernet brand/model compliant with UTM ?
What Xeon CPU does i need to purchase to have better performance ?
In case of migration from UTM to XG, could you sugget me a hardware compliant with both version please ?
If the home network process is not correct or can be optimised, don't hesitate to make any suggestion ;)
Best Regards.
This thread was automatically locked due to age.