Release Post: Sophos Firewall v21 Early Access Announcement
Whats New Link: https://assets.sophos.com/X24WTUEQ/at/7t8k46h9ttmxt6pn8g58k7wb/sophos-firewall-key-new-features-v21.pdf
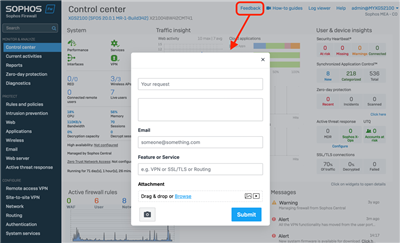
Please provide feedback using the option at the top of every screen in your Sophos Firewall as shown below or via the Community Forums.
NOTE: Sophos Firewall v21 does NOT include support for XG and SG Series appliances. XG Series EOL is March 31, 2025.
XG/SG Hardware will find them self until the EOL on the V20.0 Branche with MR2 +
Sophos SFOS Home users are not affected, as SFOS Home is running the software version.
For LE Related config issues, please review this post first: Let´s Encrypt Deep Dive & Debugging in SFOSv21.0
LE
[bearbeitet von: LuCar Toni um 8:59 AM (GMT -7) am 31 Aug 2024]

