Hallo Zusammen,
ich habe ein neues Sophos XGS 2100, aktuell ohne Lizenz. Wir sollen von UTM auf XGS migrieren.
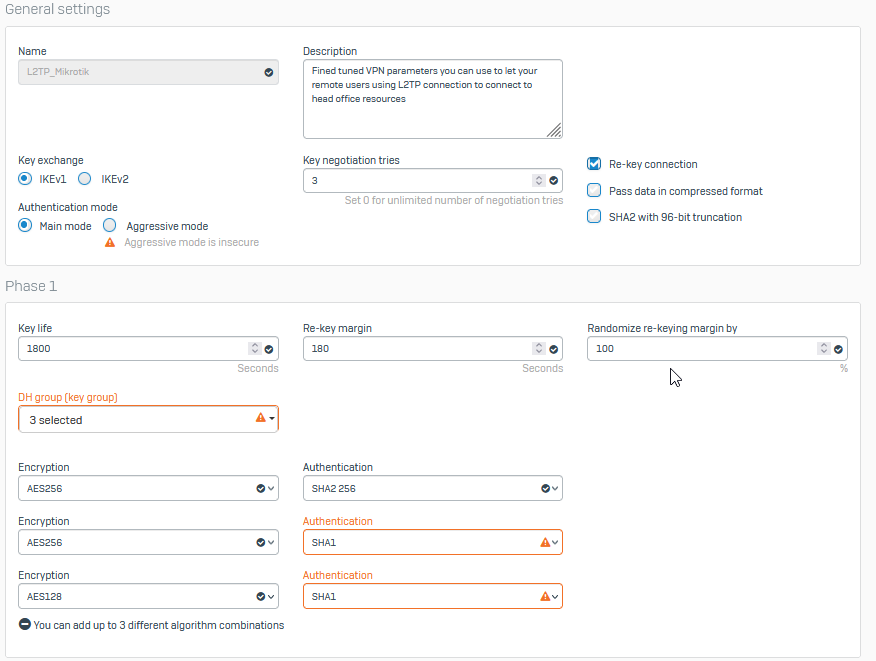
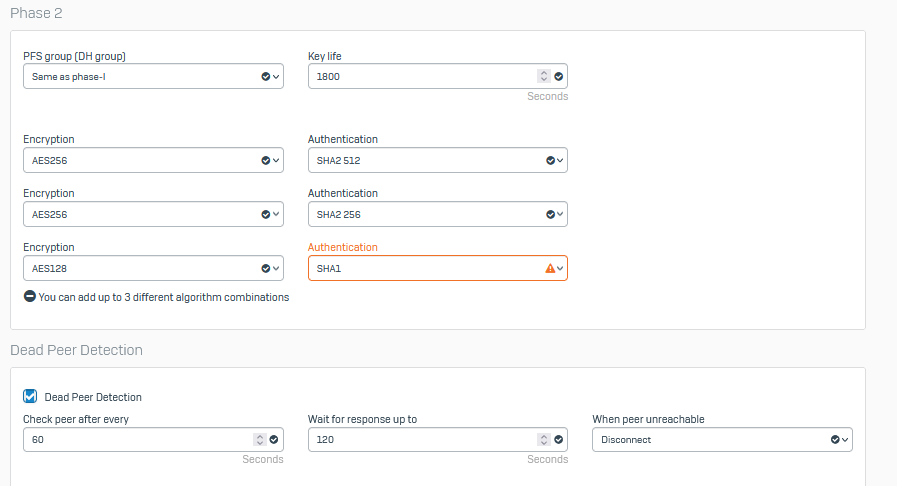
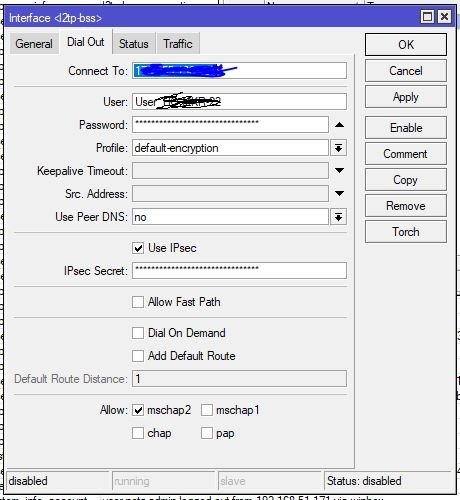
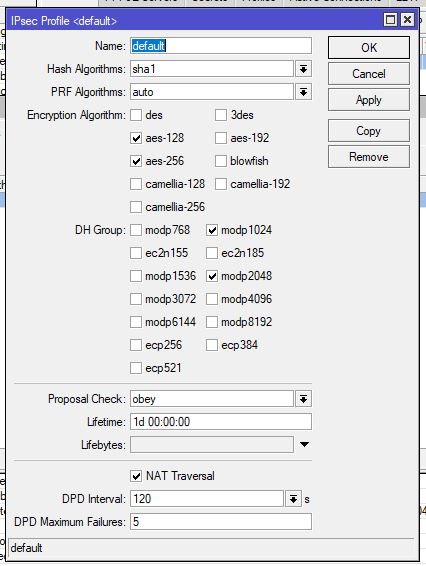
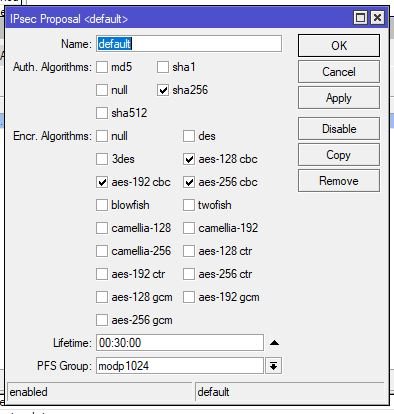
Für Homeoffice benutzen wir Mikrotik als L2TP/IPsec (client). Alles supe läuft mit UTM SG320, aber funktioniert mit XGS 2100 nicht.
Planen:
Mikrotik -- (LAN) --> Home Router -- (WAN) --> Sophos UTM / XGS.
Die Konfiguration für L2TP habe ich mit Windows geprüft, die Verbindungen wurde hergestellt. Sophos XGS zeigt in der Protokolldatei darüber an.
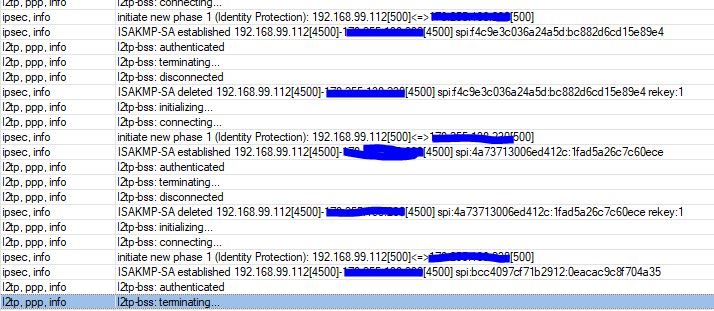
Wenn ich mit Mikrotik versuche, dann zeigt Sophos XGS in der Protokolldatei darüber nichts an.
In Packet capture:
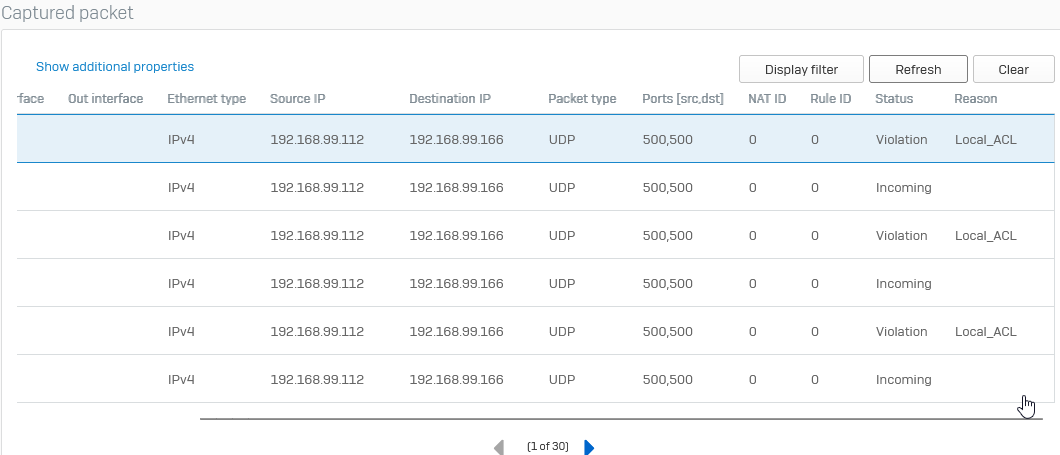
Mikrotik zeigt, dass erste Phase terminated.
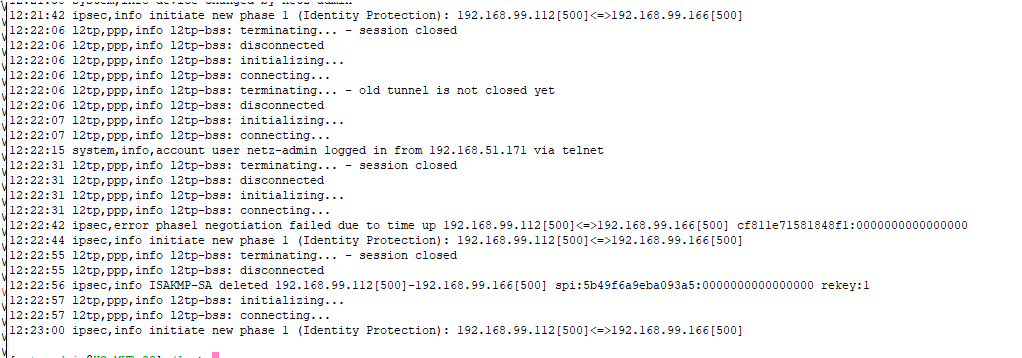
Wer hat Erfahrungen bitte HELP! :))
This thread was automatically locked due to age.