Sehr geehrte Community,
ich habe ein Problem mit iPadOS und der IPsec-VPN-Verbindung in Zusammenhang mit der Telekom.
Beim Versuch, einen VPN-Tunnel von meinem iPad aufzubauen, gelingt dies nur unregelmäßig. Lediglich (geschätzt) 2 von 10 Verbindungsversuchen sind erfolgreich. Das iPad zeigt dabei immer die Fehlermeldung: "Kommunikation mit VPN-Server fehlgeschlagen".
Interessanterweise funktioniert die Verbindung von Windows-Clients und iPhones (iOS) reibungslos. Sobald das iPad mit einem WLAN verbunden ist oder ich einen Hotspot über das iPhone (ebenfalls Telekom LTE) nutze, stellt es die Verbindung ebenfalls zuverlässig her.
Ein weiterer Außendienst Mitarbeiter ist aktuell in Italien und nutzt Telekom IT. Dieser hat keinerlei Probleme mit der Verbindung.
Hier meine Konfiguration:
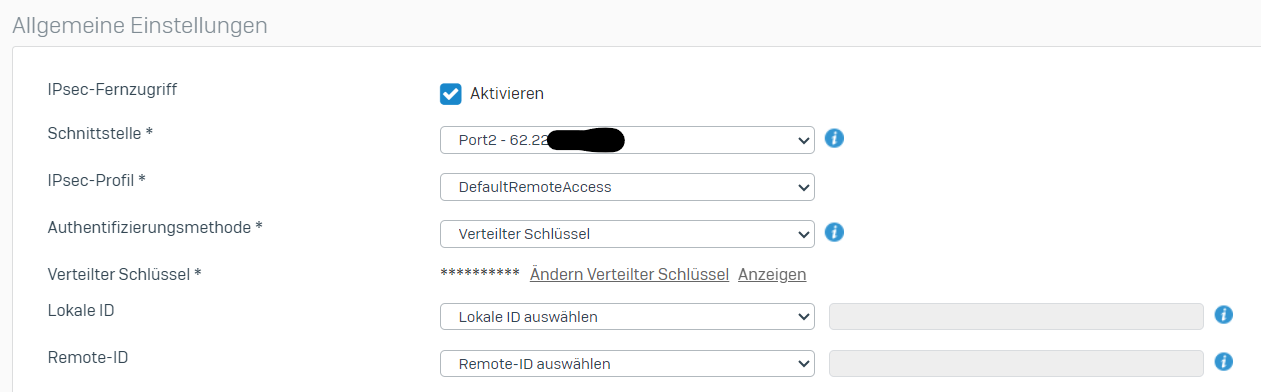
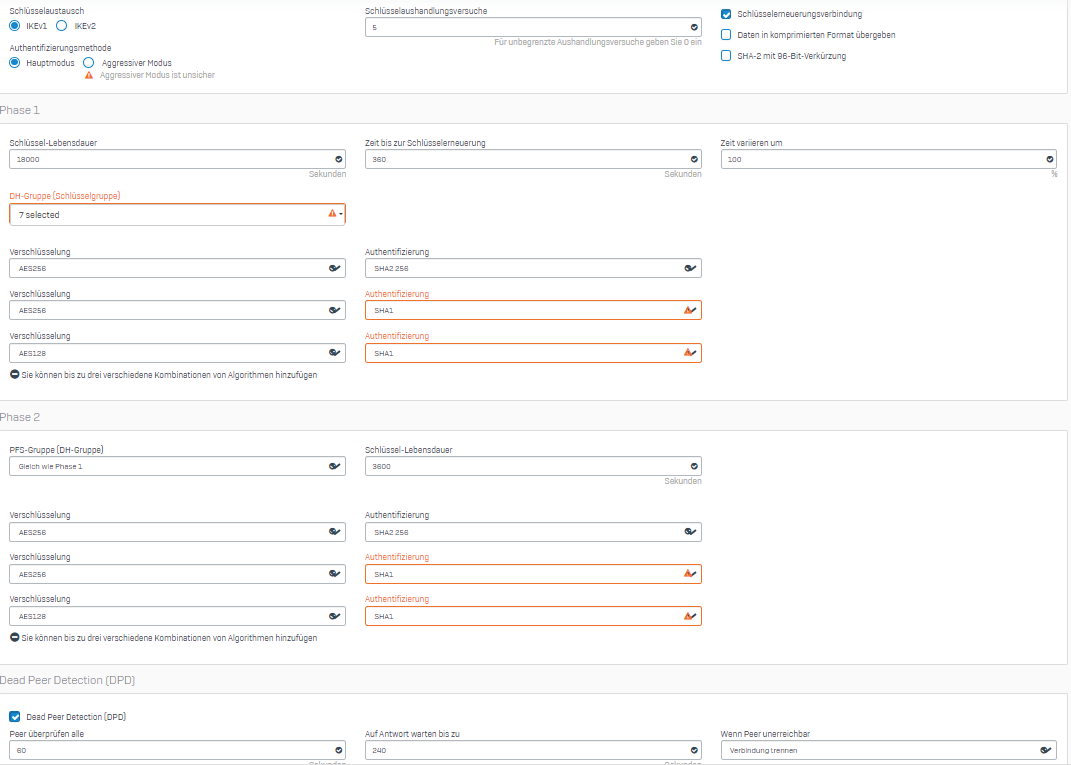
Added V20.0 MR2 TAG
[edited by: Erick Jan at 12:39 AM (GMT -7) on 1 Oct 2024]


