Hello Sophos Community,
I am a Sophos beginner and have questions regarding the options for site connection via REDs or site-to-site VPN, as I have no practical experience here.
What are my requirements?
- The idea is to connect 3 locations, whereby several zones/networks/VLANS are to be managed across those locations. Some networks are to exist uniformly across locations.
- The complete security architecture of the Sophos environment should be active (app control, etc.).
- It should be possible to manage several zones or alternatively network segments across locations (e.g. SD-RED-60 with VLAN support).
Simple example of Zones/Networks:
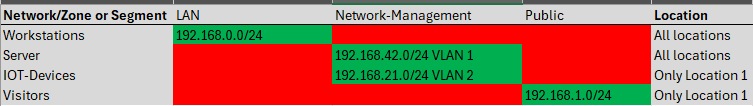
The alternatives are:
- Implementation with one Firewall and SD-REDs:
If I have understood correctly, only the unified mode can be used for REDs so that the security features take effect. However, this has the disadvantage that all traffic, including the WAN, is routed through the single Sophos firewall?
- In addition, a RED cannot map several zones as administered in the firewall. It can only belong to one zone, right? If so, would you have to use network masking (Host and Networks) in the firewall rules?
Implementation via site-to-site with multiple firewalls:
- In order to map several zones per location, a firewall would have to be available for each location and these would have to be connected via a site-to-site connection.
- Is it then possible to administer these firewalls in parallel via Sophos Central with Templates. Or is there a catch?
About the alternatives:
- Is there a disadvantage in terms of firewall rules or security when working with REDs and network masking?
- From your experience, what is the better approach, if at all possible, as described?
Many thanks in advance
This thread was automatically locked due to age.

