IPSec Site-2-Site VPN
from initiator XGS to receiver SG firewall.
the XGS is on v19.5.3
IKEv1 (caused by SG capabilities)
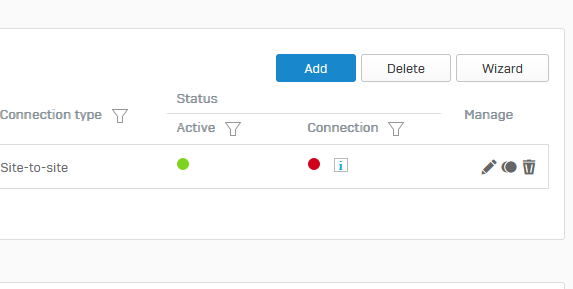
Whenever someone rebooted the ISP router on the XGS site, the XGS will not re-initiate the connection and sits there disconnected until someone logs in manually and clicks on the red icon to connect. Why is it not reconnecting automatically as we've set it up? Any idea?
Thats how it is in disconnected state:
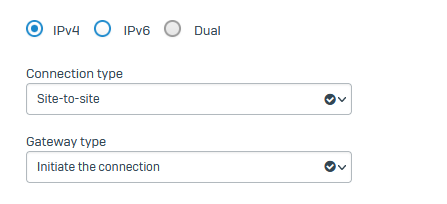
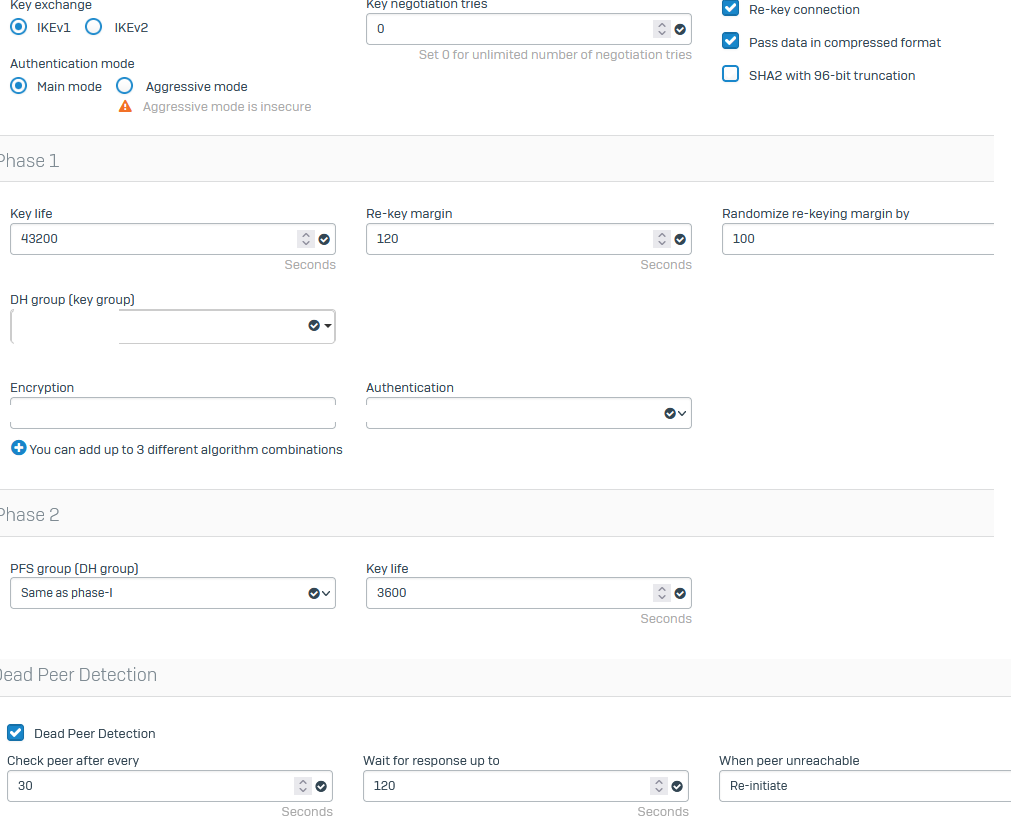
condif on XGS side:
thats the log on xgs side, showing it is giving up and does nothing until the manual connect.
2023-10-09 06:26:48Z 05[IKE] <name-1|770> IKE_SA name-1[770] established between xgsWANip[fqdn]...sgWANip[sgWANip] 2023-10-09 06:26:48Z 05[IKE] <name-1|770> scheduling rekeying in 43045s 2023-10-09 06:26:48Z 05[IKE] <name-1|770> maximum IKE_SA lifetime 43165s 2023-10-09 06:26:48Z 05[IKE] <name-1|770> ### build_i: 0x7febd8020e60 QM_INIT 2023-10-09 06:26:48Z 05[ENC] <name-1|770> generating QUICK_MODE request 1794326612 [ HASH SA No KE ID ID ] 2023-10-09 06:26:48Z 05[NET] <name-1|770> sending packet: from xgsWANip[4500] to sgWANip[4500] (668 bytes) 2023-10-09 06:26:52Z 26[IKE] <name-1|770> sending retransmit 1 of request message ID 1794326612, seq 4 2023-10-09 06:26:52Z 26[NET] <name-1|770> sending packet: from xgsWANip[4500] to sgWANip[4500] (668 bytes) 2023-10-09 06:26:59Z 30[IKE] <name-1|770> sending retransmit 2 of request message ID 1794326612, seq 4 2023-10-09 06:26:59Z 30[NET] <name-1|770> sending packet: from xgsWANip[4500] to sgWANip[4500] (668 bytes) 2023-10-09 06:27:12Z 23[IKE] <name-1|770> sending retransmit 3 of request message ID 1794326612, seq 4 2023-10-09 06:27:12Z 23[NET] <name-1|770> sending packet: from xgsWANip[4500] to sgWANip[4500] (668 bytes) 2023-10-09 06:27:33Z 13[IKE] <name-1|770> sending keep alive to sgWANip[4500] 2023-10-09 06:27:36Z 06[IKE] <name-1|770> sending retransmit 4 of request message ID 1794326612, seq 4 2023-10-09 06:27:36Z 06[NET] <name-1|770> sending packet: from xgsWANip[4500] to sgWANip[4500] (668 bytes) 2023-10-09 06:27:56Z 12[IKE] <name-1|770> sending keep alive to sgWANip[4500] 2023-10-09 06:28:16Z 23[IKE] <name-1|770> sending keep alive to sgWANip[4500] 2023-10-09 06:28:18Z 11[IKE] <name-1|770> sending retransmit 5 of request message ID 1794326612, seq 4 2023-10-09 06:28:18Z 11[NET] <name-1|770> sending packet: from xgsWANip[4500] to sgWANip[4500] (668 bytes) 2023-10-09 06:28:38Z 23[IKE] <name-1|770> sending keep alive to sgWANip[4500] 2023-10-09 06:28:58Z 15[IKE] <name-1|770> sending keep alive to sgWANip[4500] 2023-10-09 06:29:18Z 05[IKE] <name-1|770> sending keep alive to sgWANip[4500] 2023-10-09 06:29:33Z 06[IKE] <name-1|770> giving up after 5 retransmits 2023-10-09 06:29:33Z 06[DMN] <name-1|770> [GARNER-LOGGING] (child_alert) ALERT: IKE message (F4005A00) retransmission to sgWANip timed out. Check if the remote gateway is reachable. 2023-10-09 06:29:33Z 06[IKE] <name-1|770> initiating Main Mode IKE_SA name-1[771] to sgWANip 2023-10-09 06:29:33Z 06[ENC] <name-1|770> generating ID_PROT request 0 [ SA V V V V V V ] 2023-10-09 06:29:33Z 06[NET] <name-1|770> sending packet: from xgsWANip[500] to sgWANip[500] (260 bytes) 2023-10-09 06:29:37Z 05[IKE] <name-1|771> sending retransmit 1 of request message ID 0, seq 1 2023-10-09 06:29:37Z 05[NET] <name-1|771> sending packet: from xgsWANip[500] to sgWANip[500] (260 bytes) 2023-10-09 06:29:44Z 28[IKE] <name-1|771> sending retransmit 2 of request message ID 0, seq 1 2023-10-09 06:29:44Z 28[NET] <name-1|771> sending packet: from xgsWANip[500] to sgWANip[500] (260 bytes) 2023-10-09 06:29:44Z 11[NET] <name-1|771> received packet: from sgWANip[500] to xgsWANip[500] (176 bytes) 2023-10-09 06:29:44Z 11[ENC] <name-1|771> parsed ID_PROT response 0 [ SA V V V V V ] 2023-10-09 06:29:44Z 11[IKE] <name-1|771> received strongSwan vendor ID 2023-10-09 06:29:44Z 11[IKE] <name-1|771> received Cisco Unity vendor ID 2023-10-09 06:29:44Z 11[IKE] <name-1|771> received XAuth vendor ID 2023-10-09 06:29:44Z 11[IKE] <name-1|771> received DPD vendor ID 2023-10-09 06:29:44Z 11[IKE] <name-1|771> received NAT-T (RFC 3947) vendor ID 2023-10-09 06:29:44Z 11[ENC] <name-1|771> generating ID_PROT request 0 [ KE No NAT-D NAT-D ] 2023-10-09 06:29:44Z 11[NET] <name-1|771> sending packet: from xgsWANip[500] to sgWANip[500] (556 bytes) 2023-10-09 06:29:45Z 12[NET] <name-1|771> received packet: from sgWANip[500] to xgsWANip[500] (540 bytes) 2023-10-09 06:29:45Z 12[ENC] <name-1|771> parsed ID_PROT response 0 [ KE No NAT-D NAT-D ] 2023-10-09 06:29:45Z 12[IKE] <name-1|771> local host is behind NAT, sending keep alives 2023-10-09 06:29:45Z 12[IKE] <name-1|771> authentication of 'fqdn' (myself) successful 2023-10-09 06:29:45Z 12[ENC] <name-1|771> generating ID_PROT request 0 [ ID SIG ] 2023-10-09 06:29:45Z 12[NET] <name-1|771> sending packet: from xgsWANip[4500] to sgWANip[4500] (332 bytes) 2023-10-09 06:29:49Z 15[IKE] <name-1|771> sending retransmit 1 of request message ID 0, seq 3 2023-10-09 06:29:49Z 15[NET] <name-1|771> sending packet: from xgsWANip[4500] to sgWANip[4500] (332 bytes) 2023-10-09 06:29:56Z 05[IKE] <name-1|771> sending retransmit 2 of request message ID 0, seq 3 2023-10-09 06:29:56Z 05[NET] <name-1|771> sending packet: from xgsWANip[4500] to sgWANip[4500] (332 bytes) 2023-10-09 06:30:09Z 26[IKE] <name-1|771> sending retransmit 3 of request message ID 0, seq 3 2023-10-09 06:30:09Z 26[NET] <name-1|771> sending packet: from xgsWANip[4500] to sgWANip[4500] (332 bytes) 2023-10-09 06:30:29Z 05[IKE] <name-1|771> sending keep alive to sgWANip[4500] 2023-10-09 06:30:53Z 13[IKE] <name-1|771> sending keep alive to sgWANip[4500] 2023-10-09 06:30:55Z 10[IKE] <name-1|771> ### destroy: 0x7feba4007cb0 2023-10-09 06:30:55Z 10[IKE] <name-1|771> ### destroy: 0x7feba40068e0 ... 2023-10-09 06:30:55Z 10[IKE] <name-1|771> ### destroy: 0x7febd8020fa0 2023-10-09 06:30:55Z 10[IKE] <name-1|771> ### destroy: 0x7febd8020e60 manual reconnect here: 2023-10-09 11:51:26Z 05[CFG] loading secrets from '/_conf/ipsec/connections/name.secrets' 2023-10-09 11:51:26Z 05[CFG] get_nsg_context tblvpnconnection:name 2023-10-09 11:51:26Z 06[CFG] vici initiate 'name-50' 2023-10-09 11:51:26Z 26[IKE] <name-1|781> ### queue_child invoking quick_mode_create 2023-10-09 11:51:26Z 26[IKE] <name-1|781> ### quick_mode_create: 0x7febbc0044b0 config 0x7febbc002650 2023-10-09 11:51:26Z 26[IKE] <name-1|781> initiating Main Mode IKE_SA name-1[781] to sgWANip 2023-10-09 11:51:26Z 26[ENC] <name-1|781> generating ID_PROT request 0 [ SA V V V V V V ] 2023-10-09 11:51:26Z 26[NET] <name-1|781> sending packet: from xgsWANip[500] to sgWANip[500] (260 bytes) 2023-10-09 11:51:26Z 22[NET] <name-1|781> received packet: from sgWANip[500] to xgsWANip[500] (176 bytes)
This thread was automatically locked due to age.

