Hello all,
We have some external contractors that require access to our Azure network instance, and instead of whitelisting their own public IPs, we want them to come through our firewall (XGS 136, latest SFOS, SSL VPN set to act as gateway mode), so that we can log access and only have to whitelist our company IP range. The remote "internal" users are working as intended; however, the contractors are able to connect to our FW, using Tunnelblick, because they are Mac users, and can't go anywhere.
I have 3 Groups/Profiles of Users created in the FW for SSL VPN:
- Regular employees needing remote access to internal servers only - Configured as split
- Regular remote users that need access to internal and Azure instances - Gateway (standard/unified)
- External Contractors - Gateway (standard/unified) that should only be able to access our Azure instances
The DNS configuration for our SSL VPN is set for internal servers only (added to DNS for group 1, and only DNS available when using SSL VPN for 2 and 3).
There are a couple of issues with group 3:
First Issue: TunnelBlick Warning: DNS server address 192.168.1.1 is not a public IP address and is not being routed through the VPN
This makes sense as the only DNS available in Gateway mode is our internal DNS servers, sitting on our LAN
Second Issue: Users can't connect to Azure instance nor the internet in general (related to Issue 1...)
Would adding just the DNS server host as a permitted Network Resource, correct 1 and 2, without exposing anything else on our internal network? Do we even need to have #Port4 interface as permitted, if access to the DNS server is provided?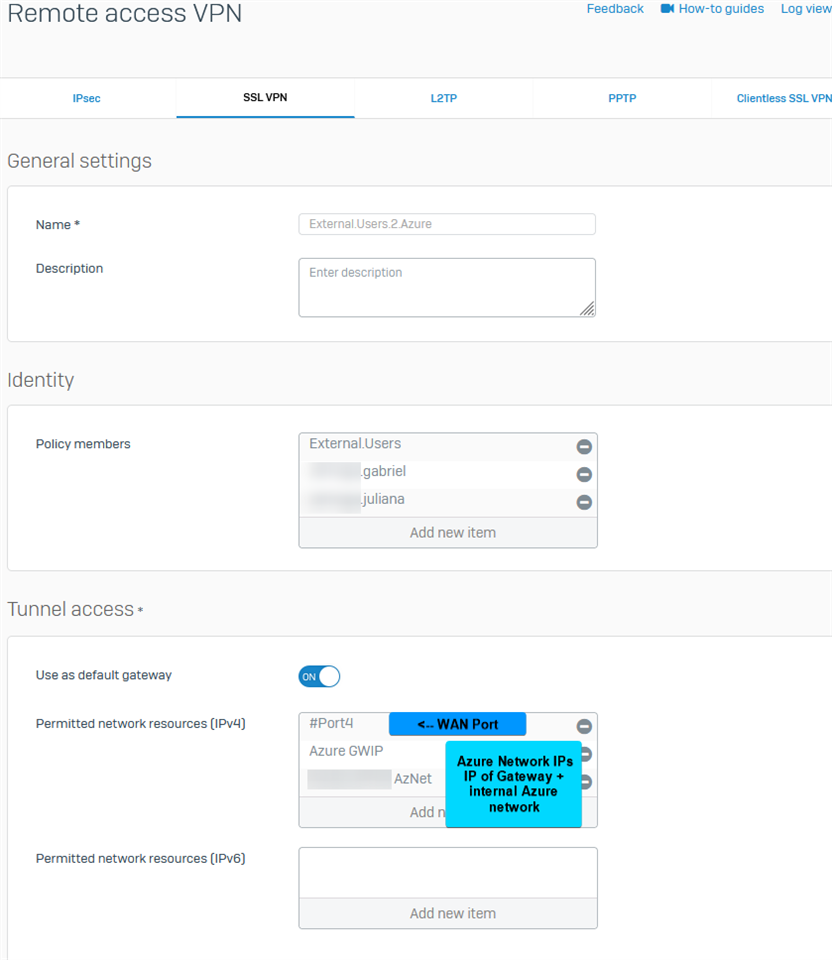
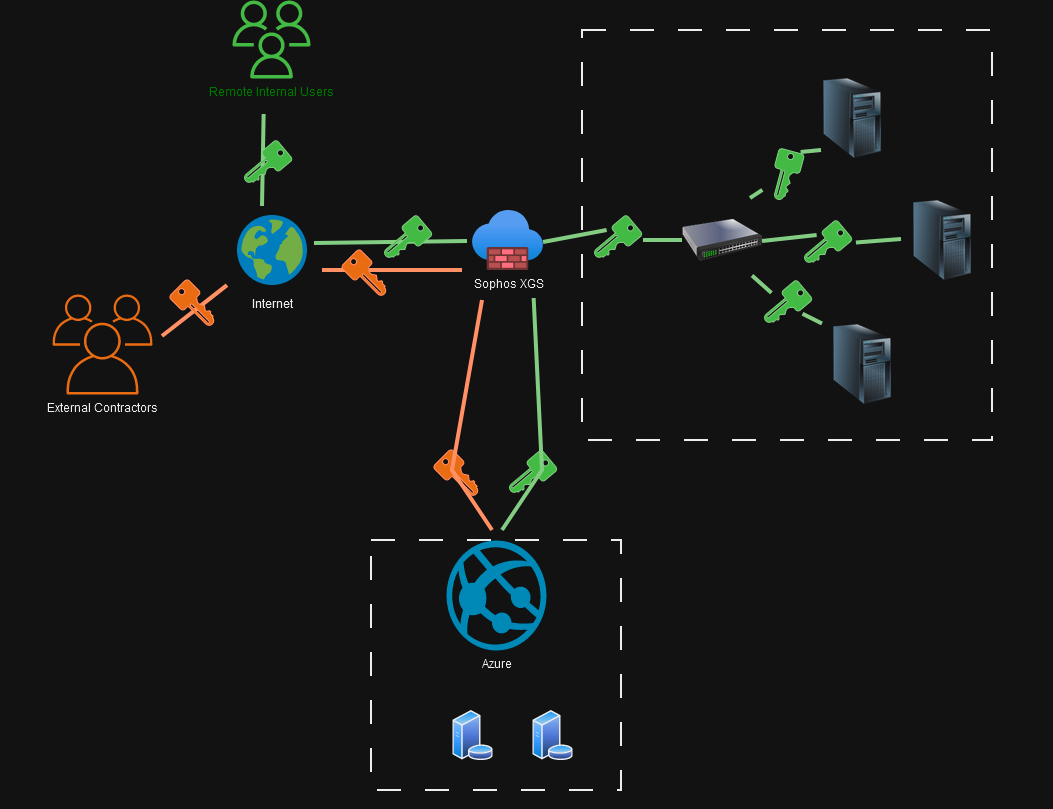
Simple Diagram for the visualists, like me (Orange items stop at the FW, Green items are working as intended).
This thread was automatically locked due to age.



