Hi,
ipsec-l2tp remote vpn is unable to pass ipsec phase 1 connection, client i nativ Windows 10
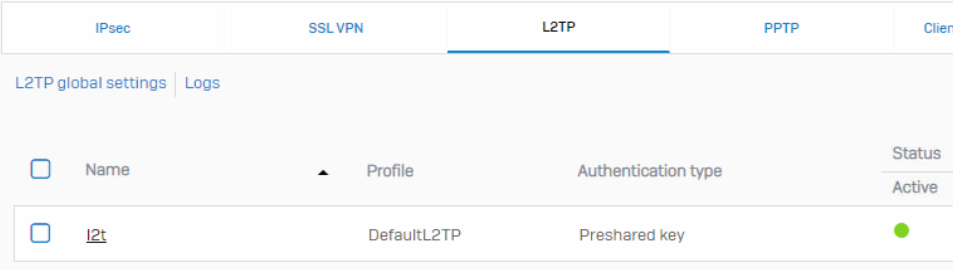
L2tp is enabled,
Profile is default L2TP
Gateway type: respond only
Preshared key is added
Port is wan port, have tried sub interface too
No local id
remote host and subnet is any
No remote id
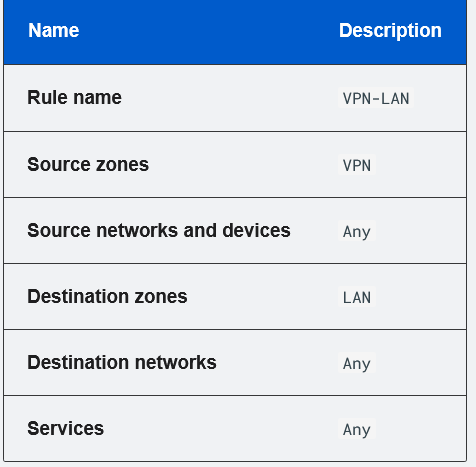
Firewall rule is added for vpn zone to internal zone
Ipsec phase 1 is active for 30 seconds then terminates, no l2tp activity in log
Any suggestions?
/Lennart
This thread was automatically locked due to age.