Can anyone help me get my site to site up between a XGS116 and a Cisco ASA5506.
I am pretty sure its an issue with phase 2 as I can see the vpn on the cisco asdm vpn monitoring but it looks like its showing phase 1 but not phase 2. Also the sophos logs is showing an issue with phase 2 policy although the log message makes no sense to me.
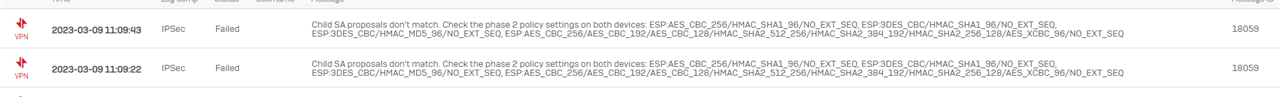
The part that doesnt make sense is all those things listed. I dont have them selected in the Sophos or the Cisco.
This is what i have on the sophos
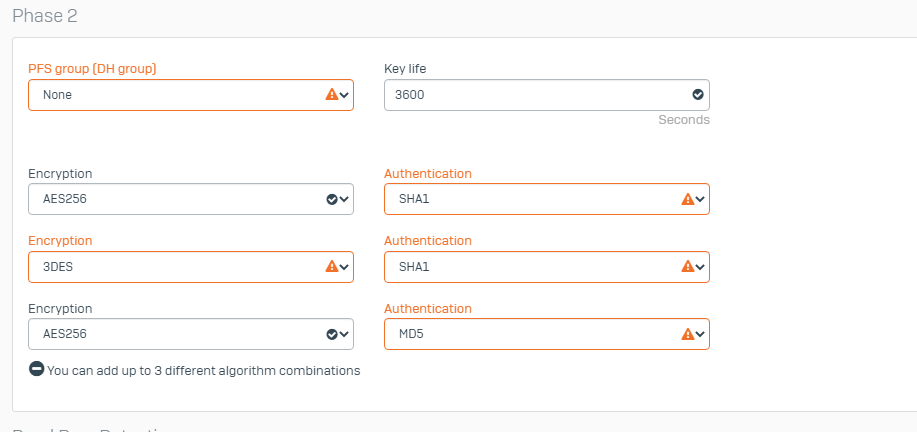
And this is what I have on the Cisco

So what doesnt make sense to me is why the Sophos error log is showing loads of Encryptions when I havent got them selected anywhere so its not helping me work out why phase 2 isnt working.
If anyone could help me sort this it would be appreciated.
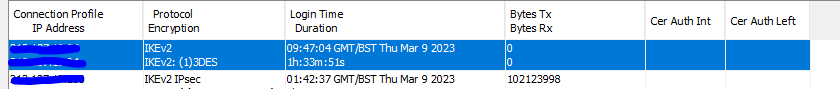
For extra info this is what cisco shows in VPN monitoring
This thread was automatically locked due to age.


