Hi,
a SFOS 19.0.1 Firewall is sending notifications via mail and system log about new firmware today. They are much too frequent.
Probably something has gone bad while you were pushing the firmware to new machines.
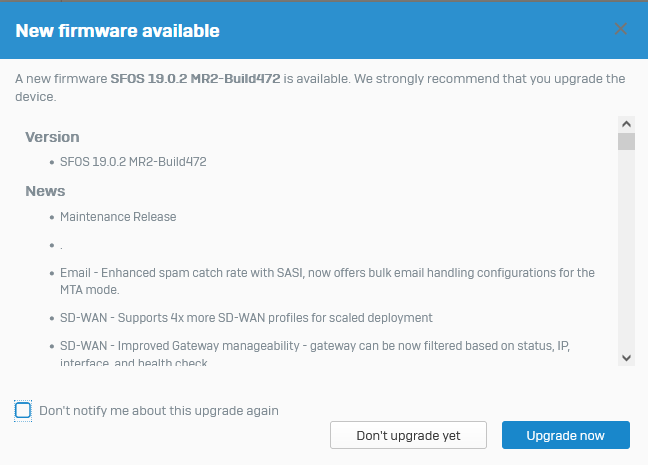
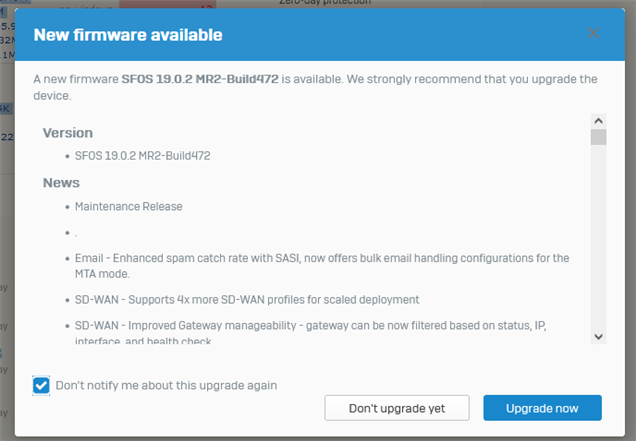
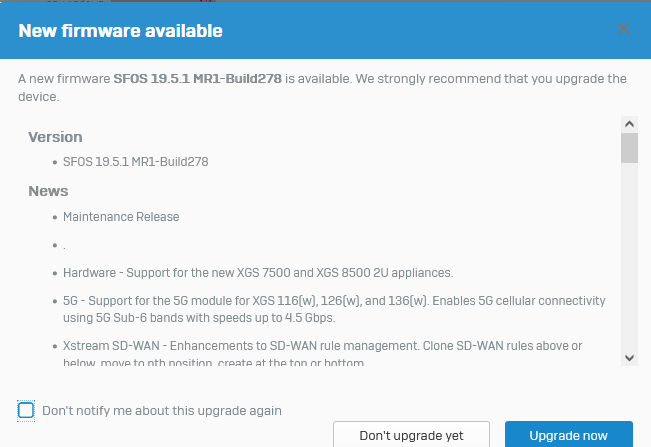
When I logged on the notification popup was definitely about 19.5. MR1 - not 19.0.2. I dismissed the message and ticked: do not show again. That was at about 14:00 today.
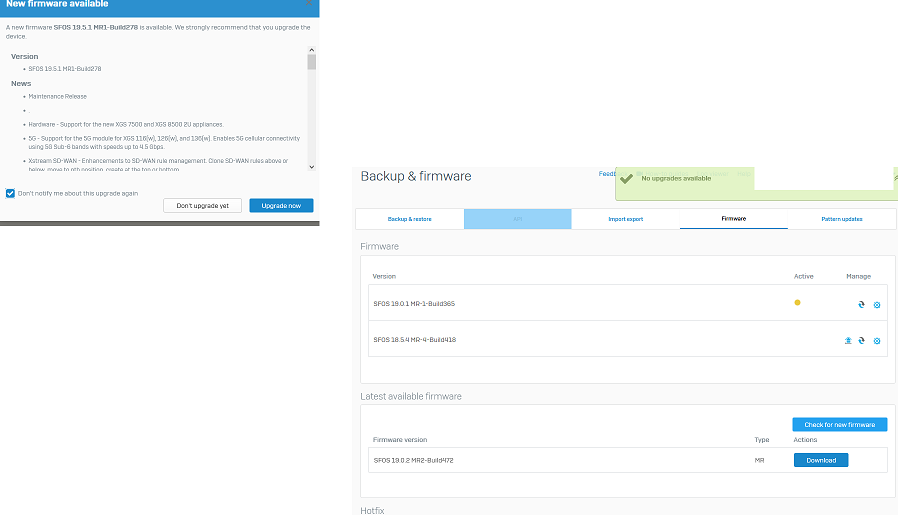
In the firmware menu there is only the update to 19.0.2 shown.
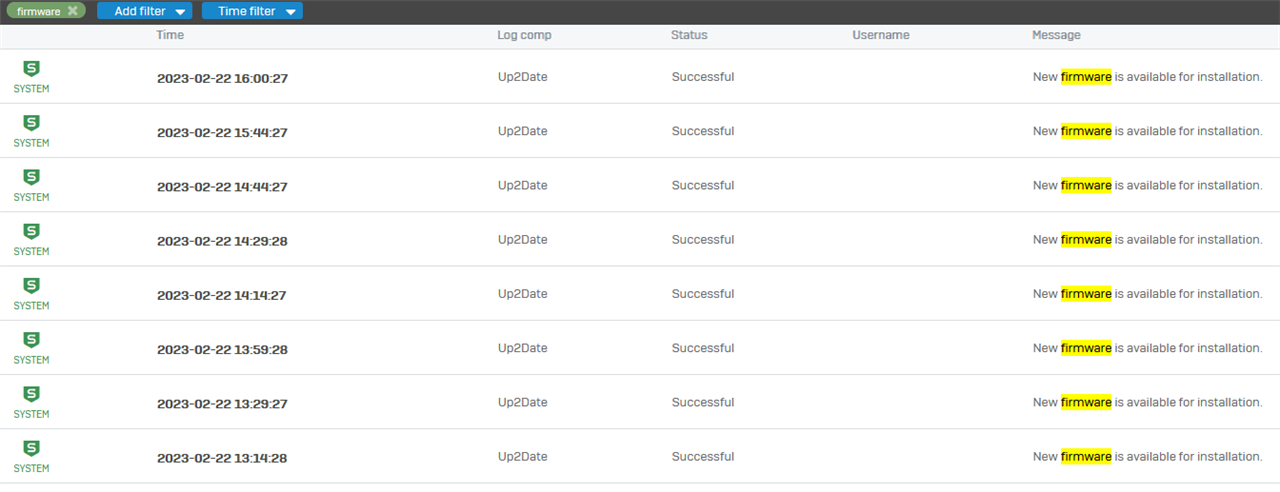
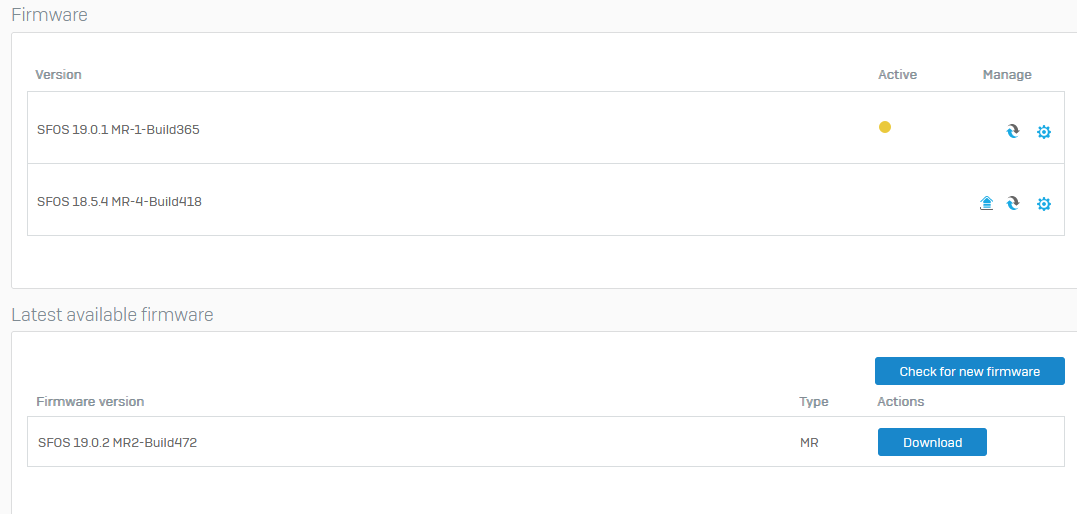
manual search brings "No upgrades available"
This thread was automatically locked due to age.