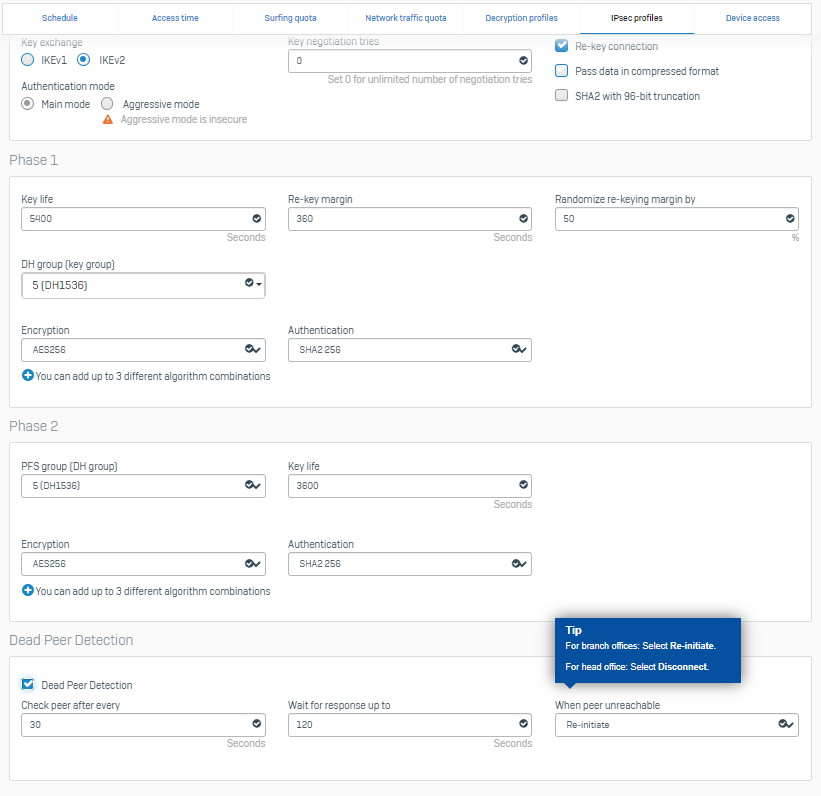
Hi,
I had a S2S VPN between a XGS2100 (18.5.3) and XG125 (19.0.1)
After upgrading both Sites for 19.5 GA the VPN connection crashes 2-3 times a week.
The VPN is up and connected, but no traffic is routed from S2S, only a manual disconnect and reconnect will fix this.
Where do i start to fix a random S2S VPN error / routing error / etc... ?
Can i switch strongswan into debug mode for a week and wait for the next bug?
Or is there any way to find this inside the normal logs?
Thanks
Jürgen
This thread was automatically locked due to age.