Hello,
We convert the configuration from UTM 135 to XGS 136 and we have one Problem with Remote Access SSL VPN and sNAT.
With the UTM we have a C2S SSL VPN for Homeoffice users to the main office (1).
The main office has 3 additional S2S connections to other locations (networks) (2-4).
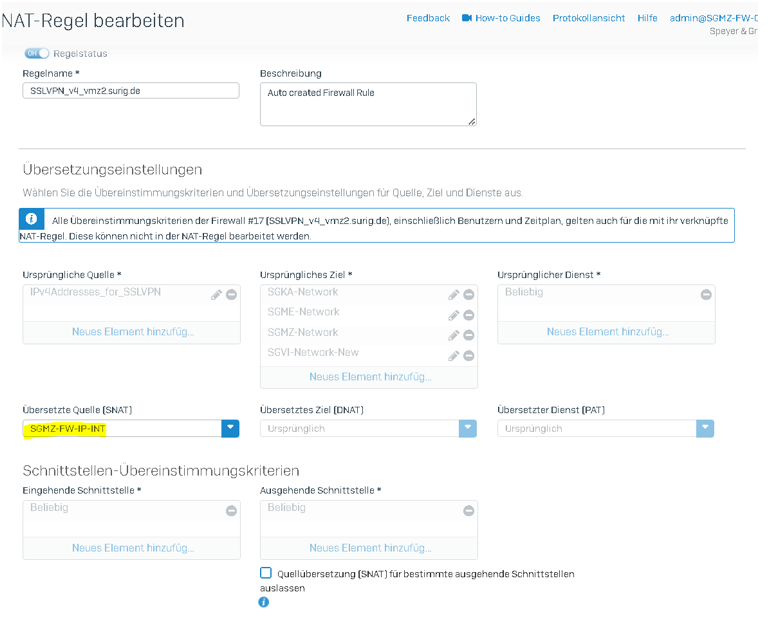
User can reach also these networks (2-4) by using this C2S VPN by using sNAT pointed to the internal FW IP
The traffic is transferred by sNAT to the other three networks 2-4.
This works fine with the UTM but we can’t get it work with the XGS.
Please see below the configuration we have done.
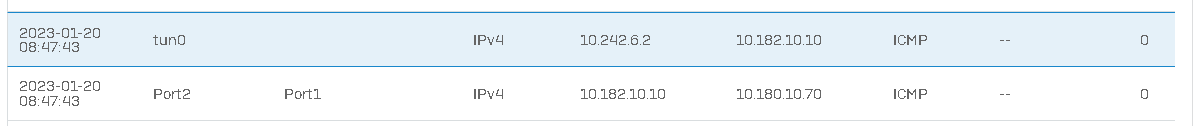
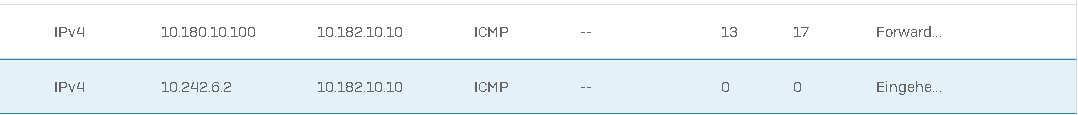
@ at the connection list we can see that ping use the roule. but we get no ping or connection to the networks 2-4 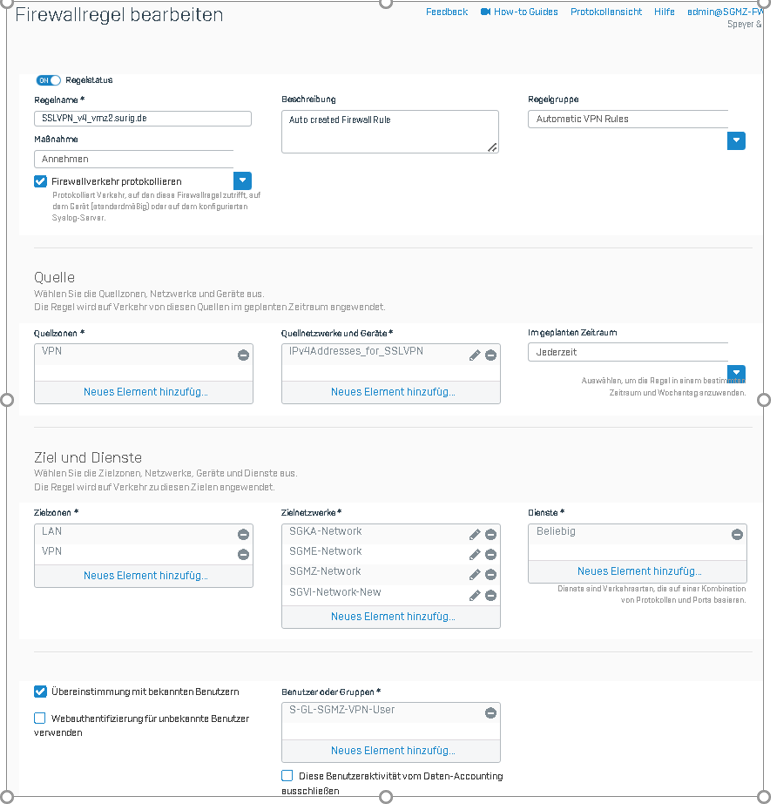
This thread was automatically locked due to age.