Hello there,
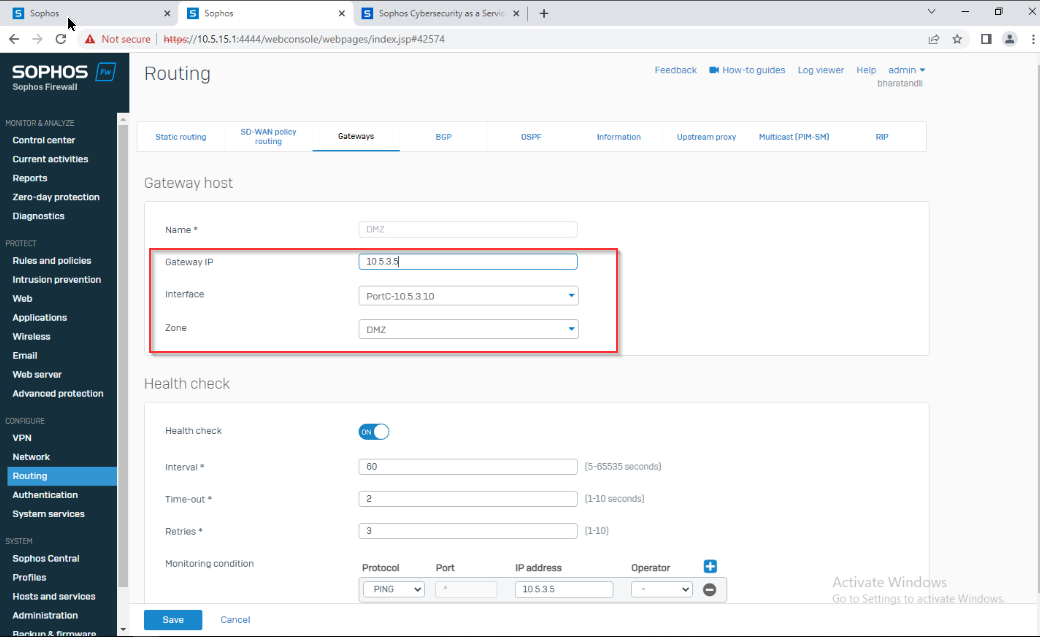
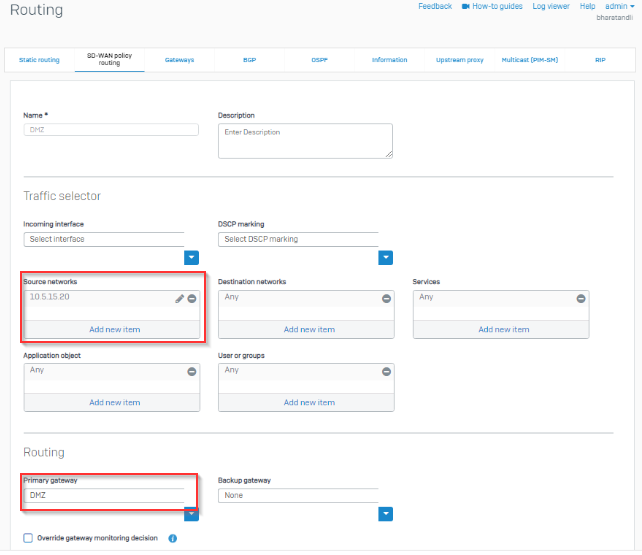
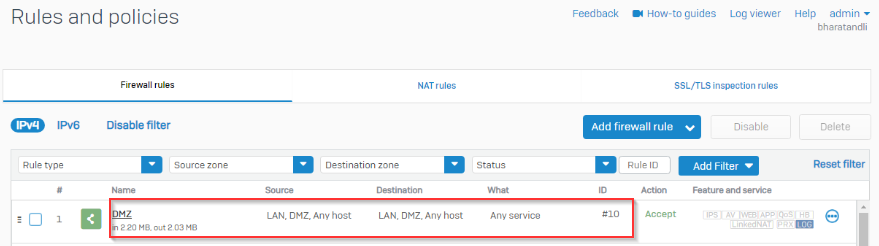
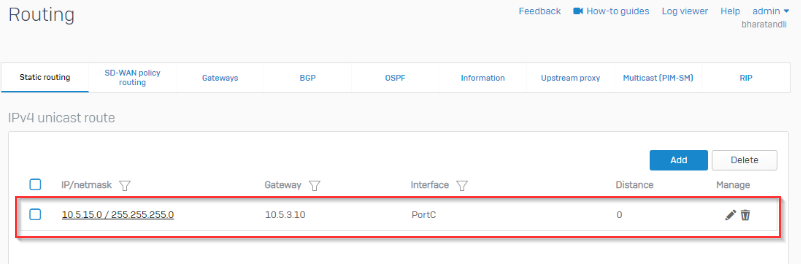
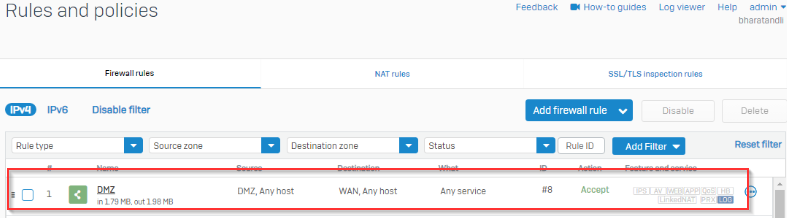
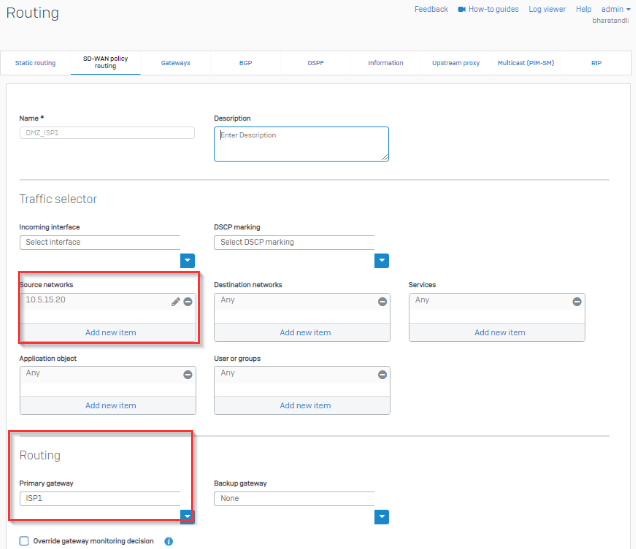
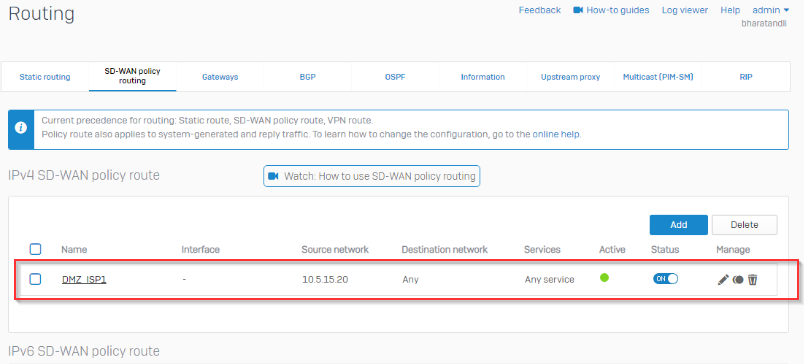
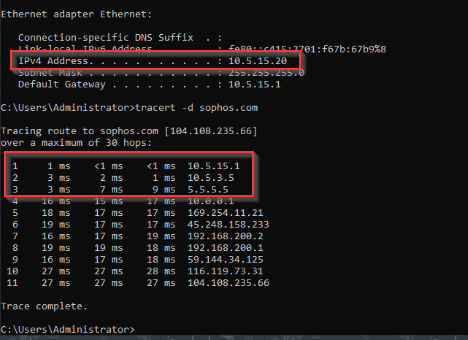
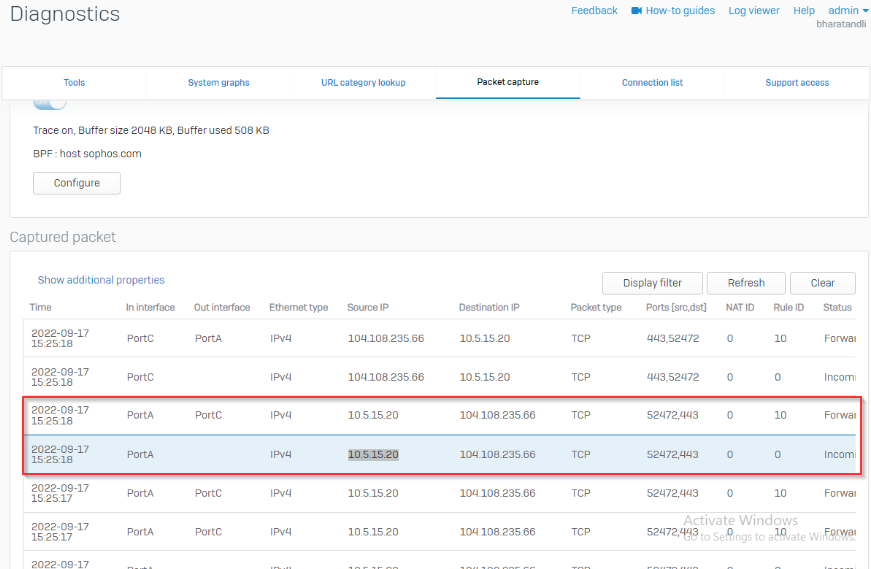
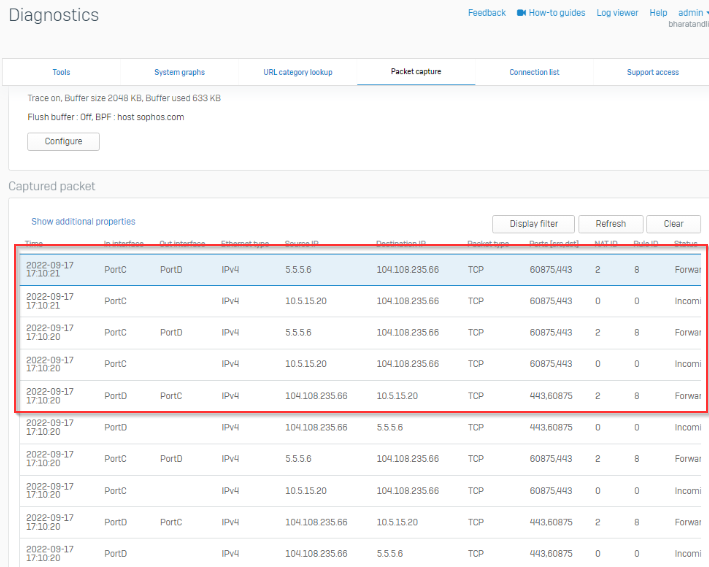
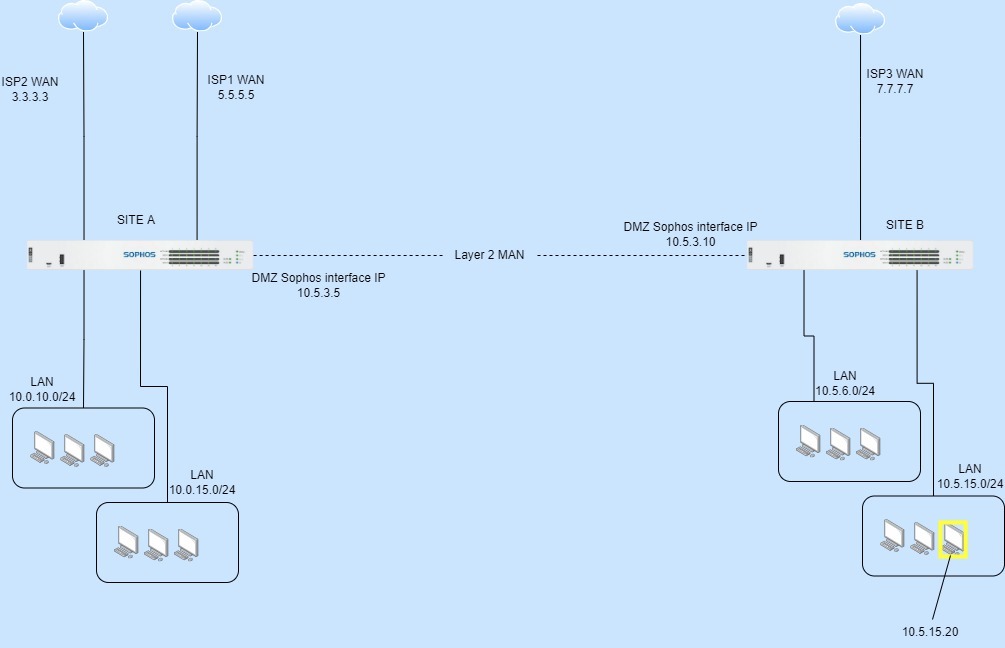
I’m trying and failing to route all internet traffic from device 10.5.15.20 at SITE B across the layer 2 MAN and out ISP1 WAN at SITE A.
I’m trying not to impact any other traffic at SITE B with this configuration, only internet bound traffic from 10.5.15.20 should be routed in a way that it traverses the Layer 2 MAN and is routed to the internet via ISP1 WAN at SITE A.
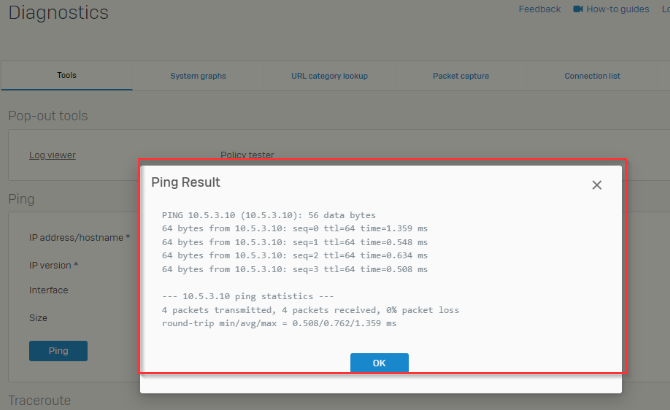
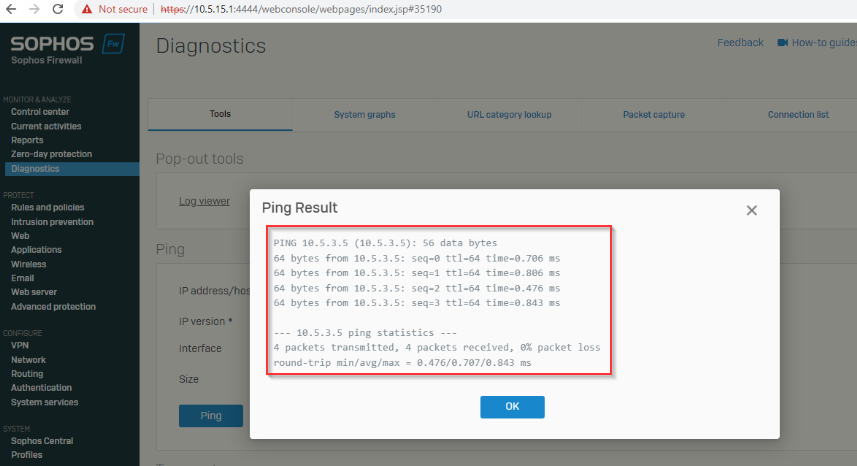
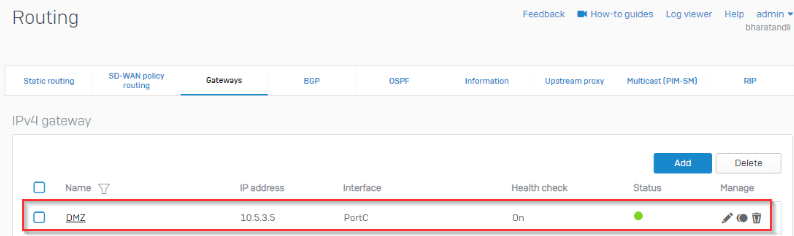
This layer 2 MAN from the provider is not MPLS and has no provided gateway or routes, the interfaces at both sites can ping each other across the MAN connection. It's basically a Layer 2 switch connection.
Any recommendations?
Both firewalls at each site are running SFOS v19 MR1.
Any help is appreciated!
This thread was automatically locked due to age.