Hi
We have set up an SSL VPN on our XGS Firewall.
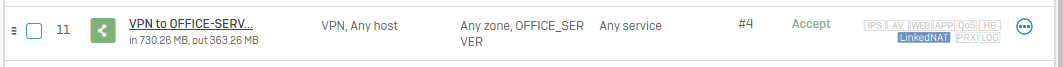
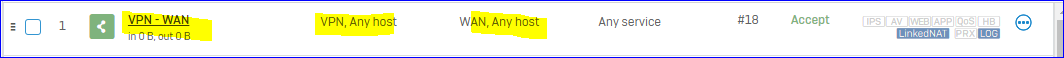
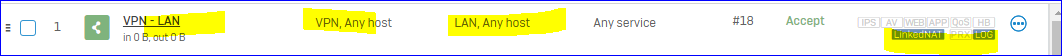
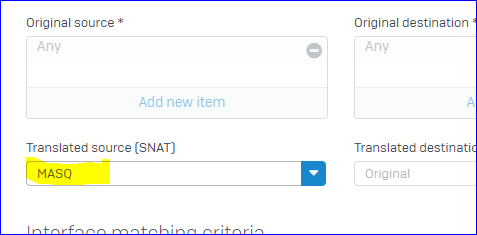
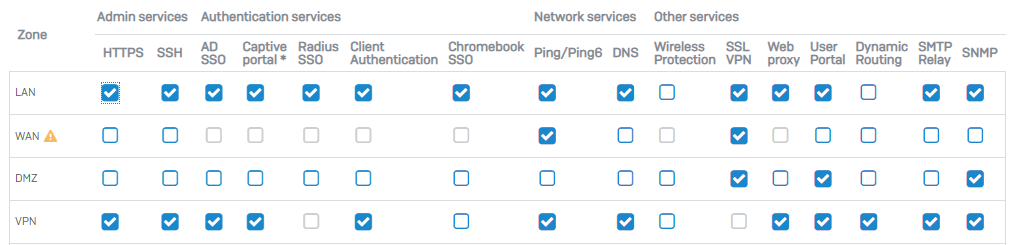
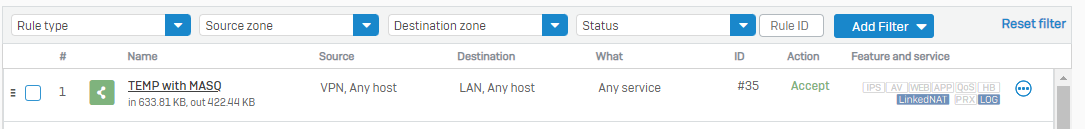
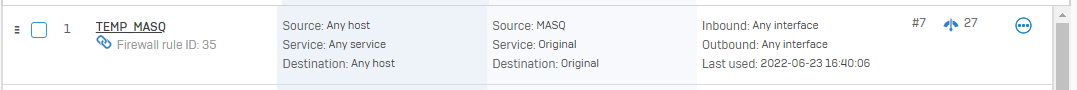
We want to route all the traffic trough the tunnel and make any network available in the tunnel (we have specific firewall rules set up to handle wo should access what).
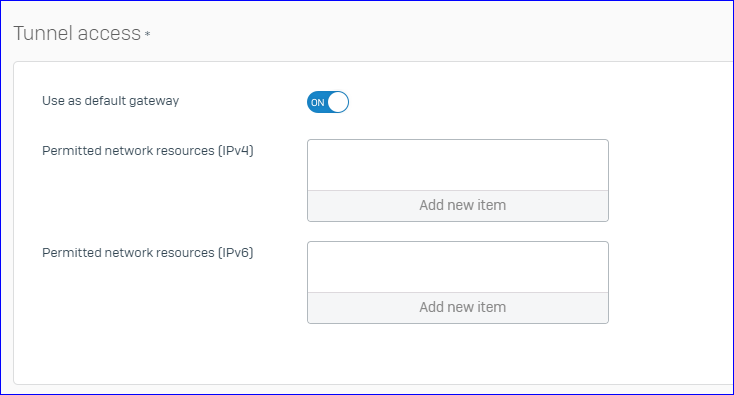
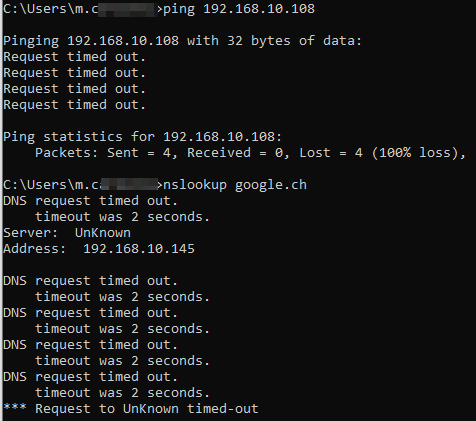
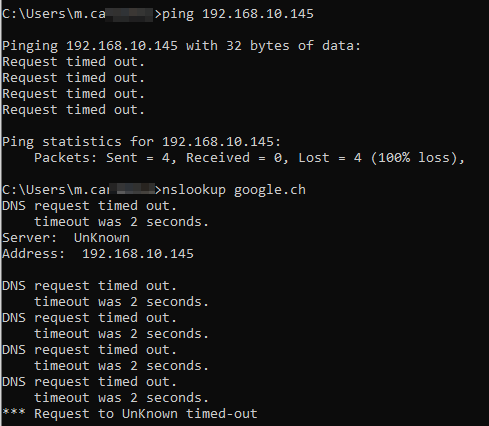
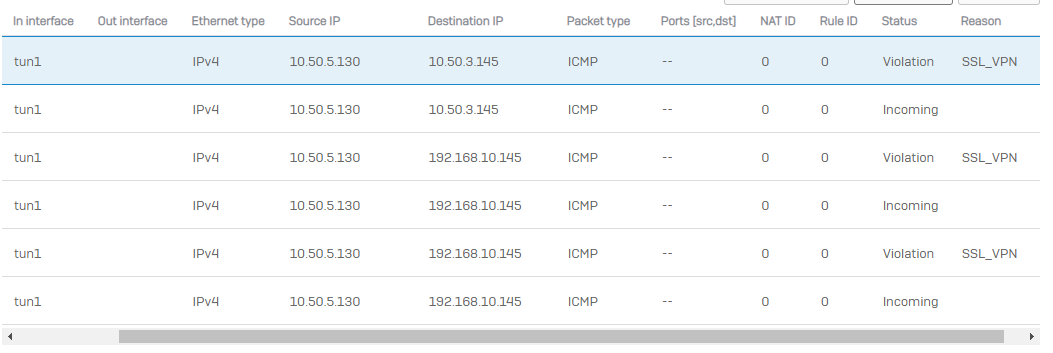
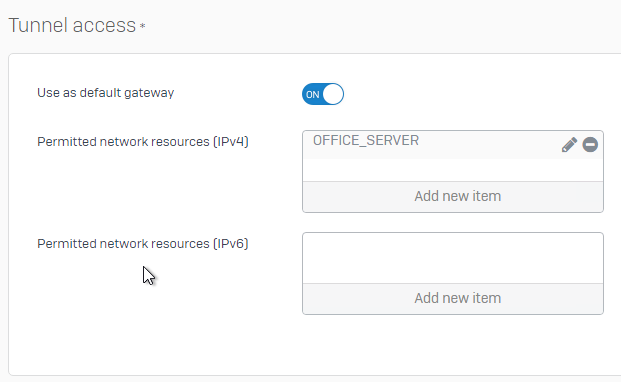
The Problem we have now, is that when we set the SSL VPN with "Use as default gateway", it does not work if we do not set an permitted ressource as well.
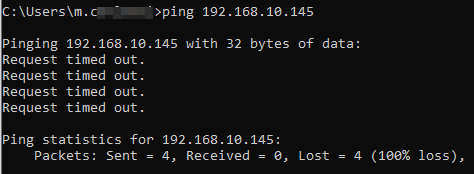
Not work = Can not connect to any ressource except the internet, even tho whe have all the required firewall rules set up
This would require us to list any network ressources we have there, which will change regulary and is quite a long list.
Is there a way, where can allow "any" as a permitted ressource?
Sophos XGS does not allow me to create a 0.0.0.0/0.0.0.0 network object.
Thanks
Mario
This thread was automatically locked due to age.