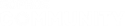Hi folks,
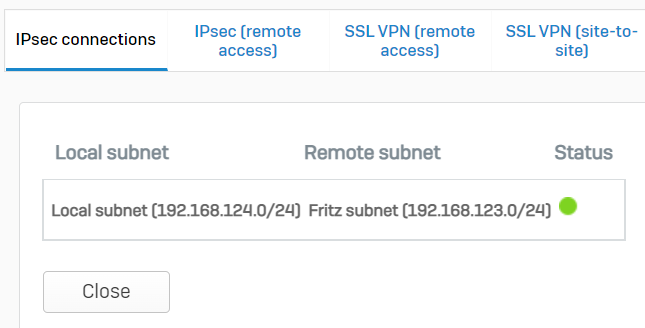
thanks to this post community.sophos.com/.../vpn---site-to-site-sophos-xg-v18x---fritzbox-v7-2x I was able to successfully establish a connection between my Sophos XG (software) SFOS 18.5.1 MR-1-Build326 and FritzBox 7590 OS 7.28
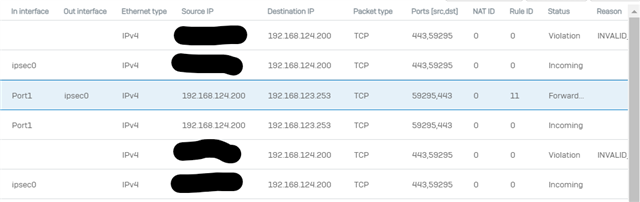
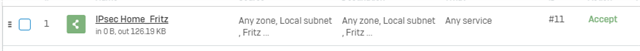
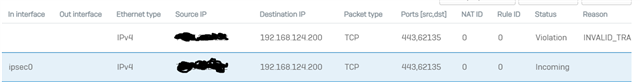
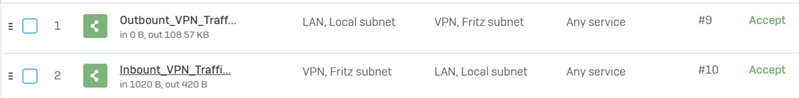
the vpn is active but I can't in any way reach the networks on both sides. I obviously created the appropriate rules on Sophos
SFVH_SO01_SFOS 18.5.1 MR-1-Build326# route -n
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
x.xxx.xxx.0 0.0.0.0 255.255.255.0 U 0 0 0 Port2
10.81.234.0 0.0.0.0 255.255.255.0 U 0 0 0 tun0
10.255.0.0 0.0.0.0 255.255.255.0 U 0 0 0 GuestAP
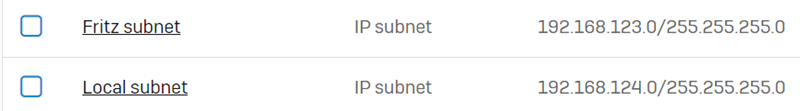
192.168.123.0 0.0.0.0 255.255.255.0 U 0 0 0 ipsec0 (manually addedd)
192.168.124.0 0.0.0.0 255.255.255.0 U 0 0 0 Port1
SFVH_SO01_SFOS 18.5.1 MR-1-Build326# ifconfig ipsec0
ipsec0 Link encap:Ethernet HWaddr 62:CA:75:EC:63:B6
inet addr:169.254.234.5 Bcast:0.0.0.0 Mask:255.255.255.255
inet6 addr: fe80::60ca:75ff:feec:63b6/64 Scope:Link
UP BROADCAST RUNNING NOARP MULTICAST MTU:16260 Metric:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:0 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:0 (0.0 B) TX bytes:0 (0.0 B)
on the Fritzbox
enabled = yes;
editable = yes;
conn_type = conntype_out;
name = "xxxxx";
boxuser_id = 0;
always_renew = no;
reject_not_encrypted = no;
dont_filter_netbios = no;
localip = 0.0.0.0;
local_virtualip = 0.0.0.0;
remoteip = PublicIP;
remote_virtualip = 0.0.0.0;
keepalive_ip = 0.0.0.0;
localid {
fqdn = "PublicDNS";
}
remoteid {
ipaddr = PublicIP;
}
mode = phase1_mode_aggressive;
phase1ss = "dh14/aes/sha";
keytype = connkeytype_pre_shared;
key = "xxxxx";
cert_do_server_auth = no;
use_nat_t = yes;
use_xauth = no;
use_cfgmode = yes;
phase2localid {
ipnet {
ipaddr = 192.168.123.0;
mask = 255.255.255.0;
}
}
phase2remoteid {
ipnet {
ipaddr = 192.168.124.0;
mask = 255.255.255.0;
}
}
phase2ss = "esp-aes256-3des-sha/ah-no/comp-lzs-no/pfs";
accesslist = "permit ip any 192.168.124.0 255.255.255.0";
} ike_forward_rules = "udp 0.0.0.0:500 0.0.0.0:500",
"udp 0.0.0.0:4500 0.0.0.0:4500";
}
I tried to follow this guide too but with no luck https://support.sophos.com/support/s/article/KB-000035835?language=en_US
community.sophos.com/.../ipsec-site-to-site-vpn-connects-but-no-traffic-passes
some idea?
This thread was automatically locked due to age.