Hi
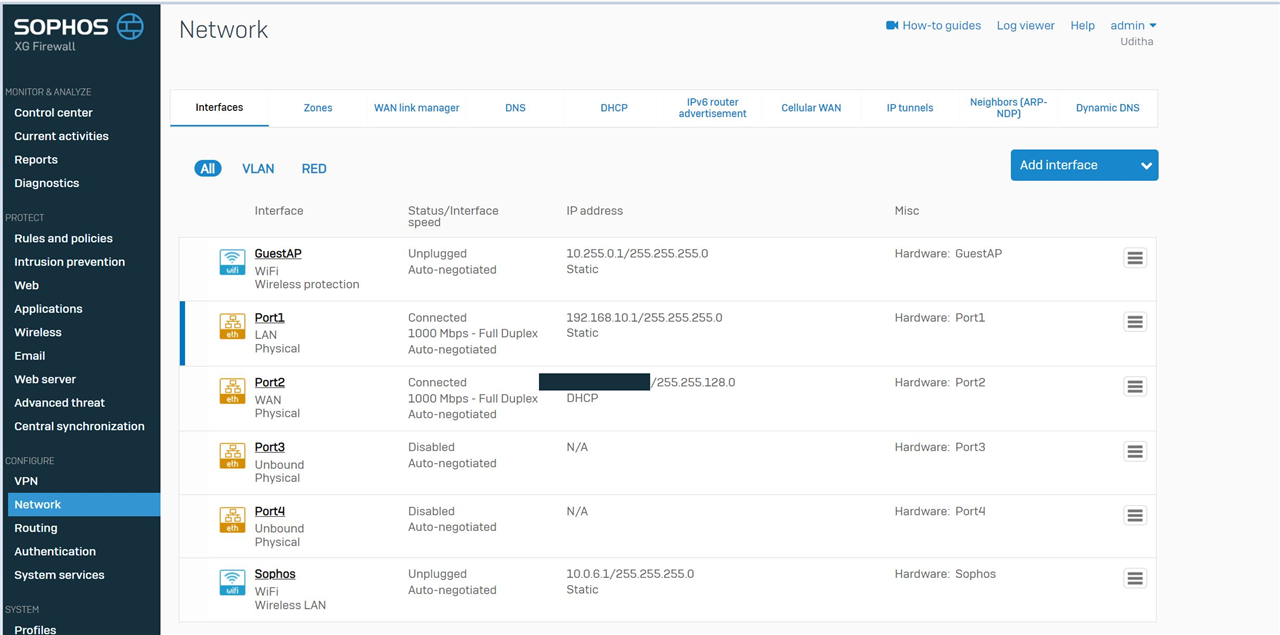
I am using Sophos XG115 as the firewall and i do have a layer 3 switch (Unifi 8 port POE 60W switch) which leverages VLANS created & tagged at XG115.
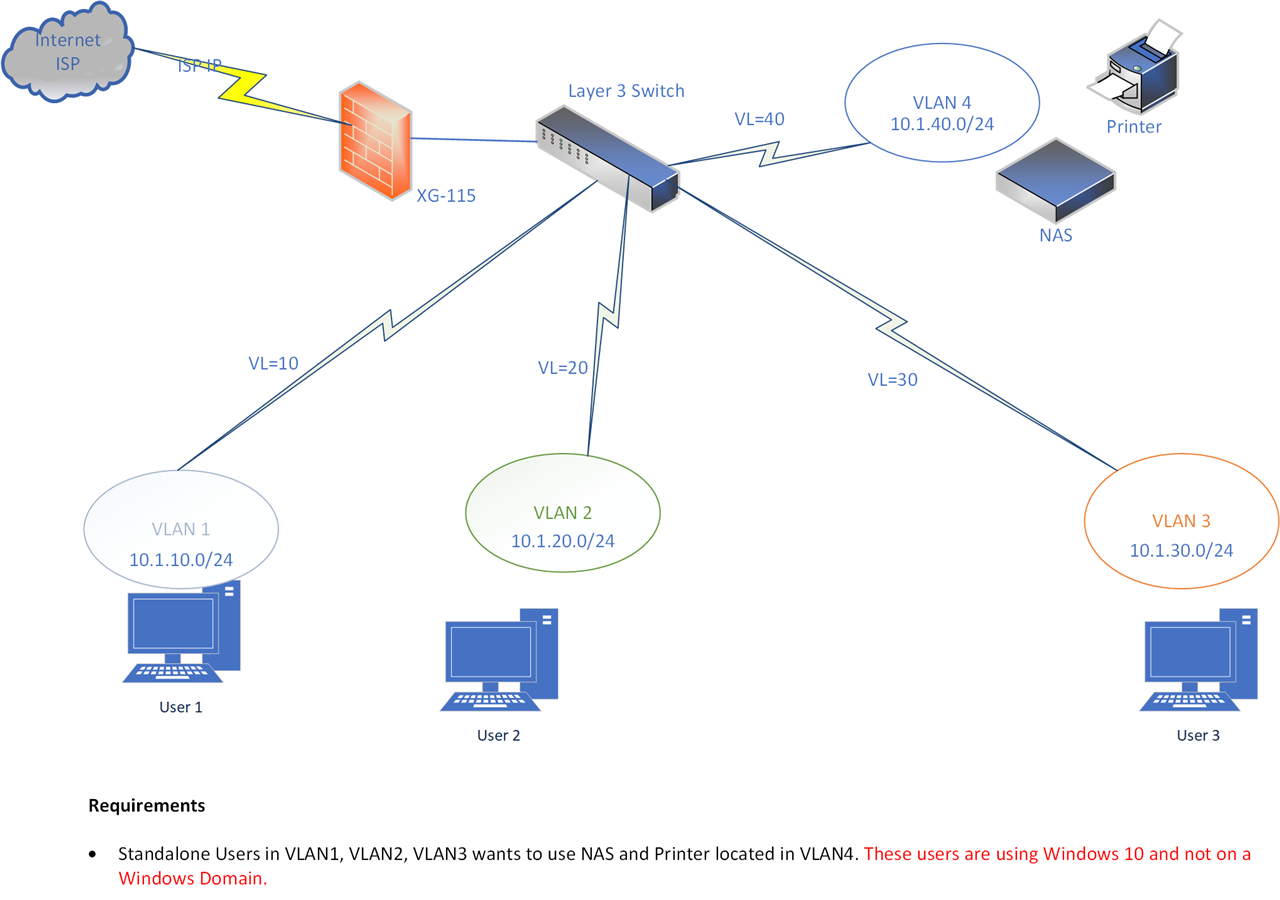
Users in different VLANs want to connect to devices (e.g. Network Printer and Network Attached Storage device [TerraMaster]) located in another VLAN.
i have created a firewall rule which enables the communication between VLANS. I have also created DHCP records for each VLANs at XG115.
I am able to PING to the gateway addresses of each VLAN. Unfortunately, the trace route keeps on failing at the gateway address of LAN network port at XG11 5when trying to reach to devices in different VLANs.
Can someone help me in steps on what we should be adding or enabling to allow users in different VLANs to access the NAS and Printer?
Please note that users are on stand-alone Windows 10 devices. There is no active directory or LDAP integrations (i mean there is no Windows server).
Below is a diagram of the network. An early response is highly appreciated.
This thread was automatically locked due to age.