This is more of an FYI post, then a support request. Although I'd like to hear from those that have ran into this issue and if you had any alternate ways of mitigating this.
I recently upgraded our XG 310 from 17.5-MR10 to 18.0-MR4, then immediately 18.0-MR5. After upgrading it, one of our long-time Sophos Connect VPN feature broke and it finally took 3 months for support to confirm it's broken.
I don't know if this existed in v17.5-MR11+ and prior to v18 FW versions. My open case is (04046519) and support has confirmed the problem and also confirmed no plans on fixing it. None of the release notes that I've dived into has indicated this capability being listed as a change, so I'm sure this was new on support's problem.
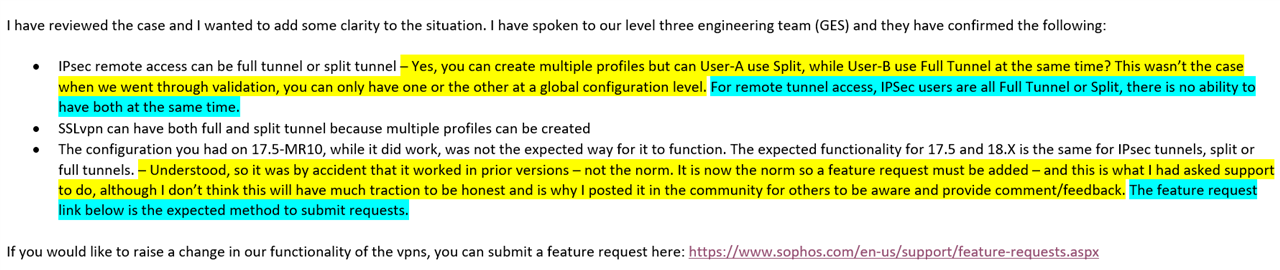
In prior versions of IPSEC-Sophos Connect VPN, you can set either split-tunnel or full-tunnel and deploy it to each client machine via the scx file configured from the SCAdmin utility. With the new firmware upgrade, the split/full tunnel capability is now handled by the Firewall side instead of the endpoints, even though you can still create profiles using the SCAdmin tool and load it onto a client computer.
Even though you can still set full-tunnel or split-tunnel using SCAdmin utility, Sophos Connect will not function correctly if you have your client profile set as Full-Tunnel but the firewall is set to split-tunnel (by way of not configuring the firewall as the default gateway option under the VPN menu).
I don't think development knew this would impact some customers that want to use both full tunnel and split-tunnel options at the same time and the loss of this capability (as well as the intent not to fix it with any future update) is frustrating, especially since it took ~3 months to confirm this issue.
In my use case, I have ~30 active VPN users, and only 10 need to be on full-tunnel to comply with security standards and data compliance. The other 20 can use Split so it doesn't saturate bandwidth. I dont want everyone to be on full tunnel and eating up all the bandwith if they're just generally browing internet.
With the new changes, it breaks this option. Here's what works/doesn't work.
- FW (use as default gateway) + SCX profile (full tunnel) - Works
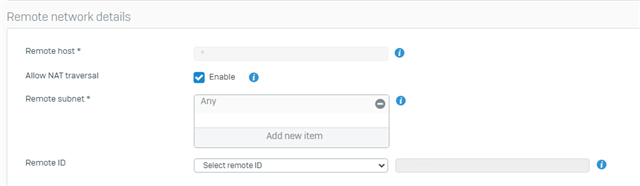
- FW (use as default gateway) + SCX profile (split-tunnel) - Works, but your connections will be all full-tunnel because of the FW setting and the client machine will have the FW internal IP as the default gateway.
- FW (don't use as default gateway) + SCX profile (full tunnel) - Will not work because the client machine does not get a default route set. 0.0.0.0/0 is used as the default route and since the firewall is set up to not be the default route, packets have no way of routing.
- FW (don't use as default gateway) + SCX profile (split tunnel) - Works, just make sure network subnets are configured on both the client SCX profile and the FW's allowed subnets under VPN.
This thread was automatically locked due to age.