Hello,
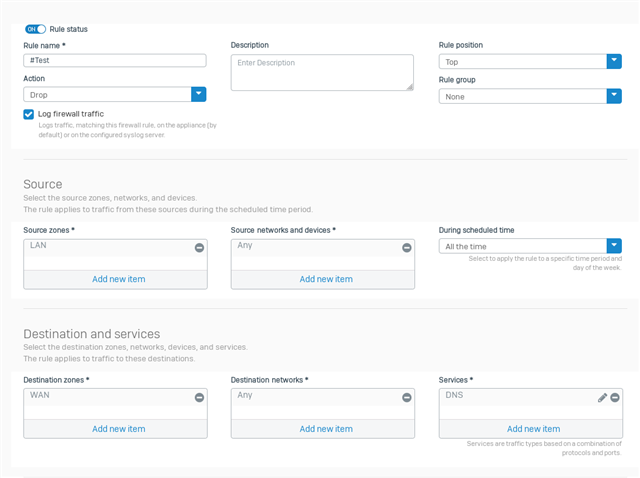
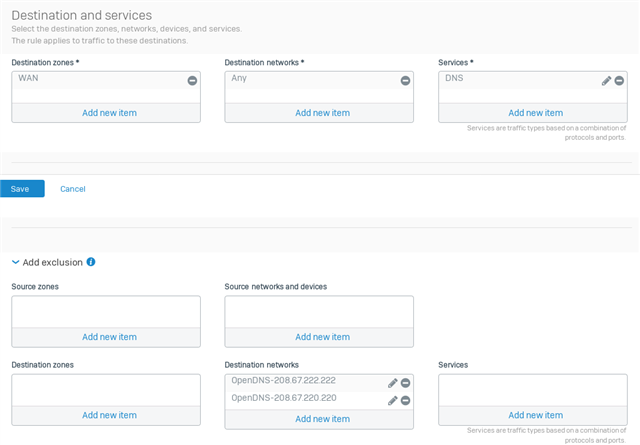
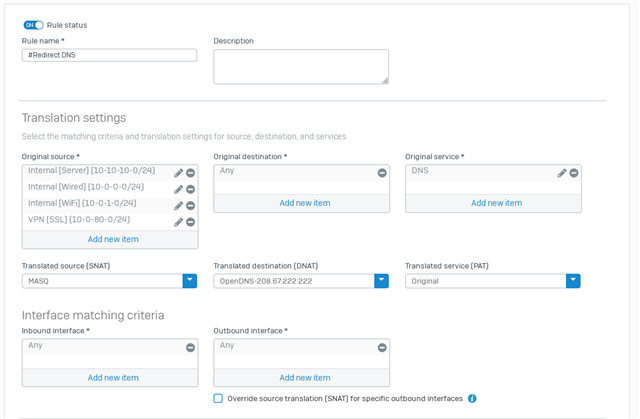
We want our lan users to not be able to change their dns settings on their computers or browsers to use other dns services available on the web. We want to only allow access to these two dns servers : 208.67.222.222 and 208.67.220.220 (these are opendns servers).
How can we setup a firewall rule to block all dns services, except for if that service is reaching to A) the sophos firewall itself, or B) these 2 IP's 208.67.222.222 and 208.67.220.220
This thread was automatically locked due to age.