I am in the process of switching over a number of sites from cyberoam to sophos xg106 latest firmware.
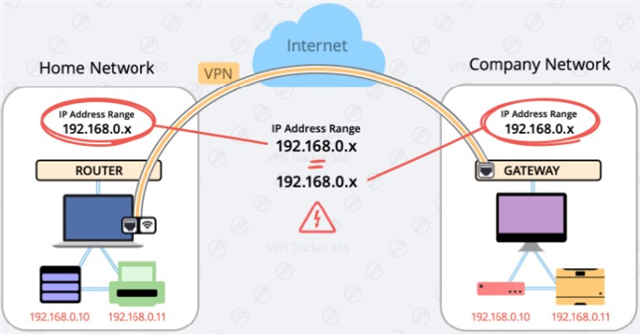
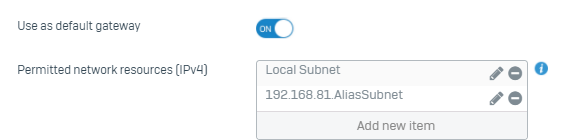
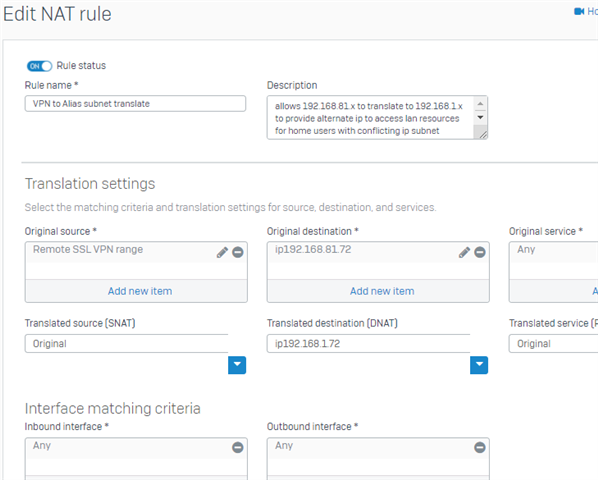
On cyberoam, if the work network had the same subnet as the remote user's home network, I was able to setup an alias or forwarder or virtual host subnet so the remote home worker could still access resource on the work network.
For example if work subnet is 192.168.1.x and home subnet is 192.168.1.x then home user can't ping or use remote desktop to access their work pc.
if you try to reach 192.168.1.abc it will only search the home network.
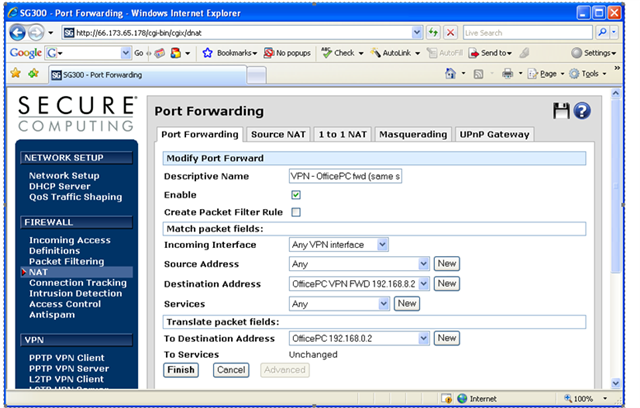
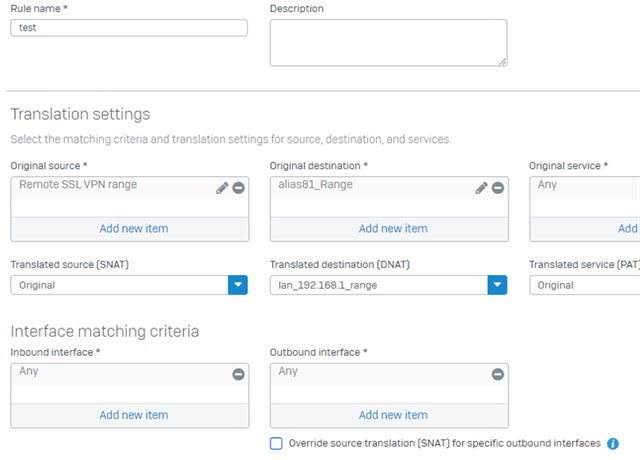
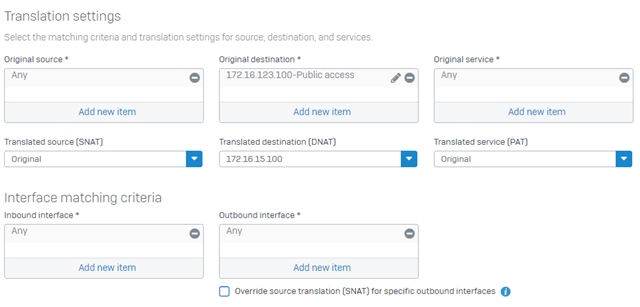
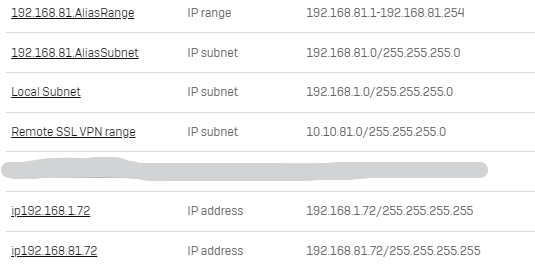
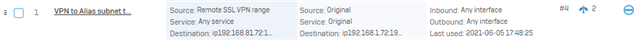
What i've done in the past is setup an translation subnet like 192.168.81.x
If the user try's rdp to 192.168.81.x the firewall will translate it to 192.168.1.x
how can this be done with the sophos?
This thread was automatically locked due to age.