Hi folks,
looking for some help with DoS settings.
Suddenly my security cameras are failing DoS UDP and ICMP flooding. I have disabled DoS fro UDP and ICMP to allow the cameras to work.
What I have tried and failed with.
1/. new application for viewing the cameras, no positive affect
2/. change the DoS UDP setting to larger values, went as high as 12500, no positive affect
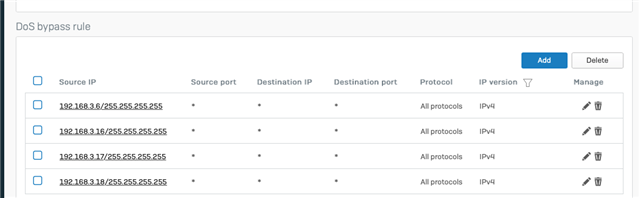
3/. added many DoS bypass rules for 5 external networks using large masks and two internal networks
4/. setup DoS bypass for incoming traffic, no polite affect.
So, the question is how do I exclude 4 devices from DoS protection or in the worst case the entire IoT network?
Ian
This thread was automatically locked due to age.