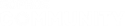Hello.
I've come across a minor issue with the Web Filter where a user may still be able to load a webpage, even though it is 'blocked.'
Running the latest version of XG firewall (18.0.4 MR-4).
To replicate:
1. Create a URL group and add a domain, for example: example.com
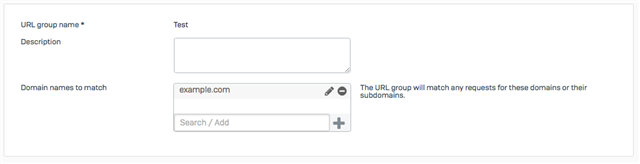
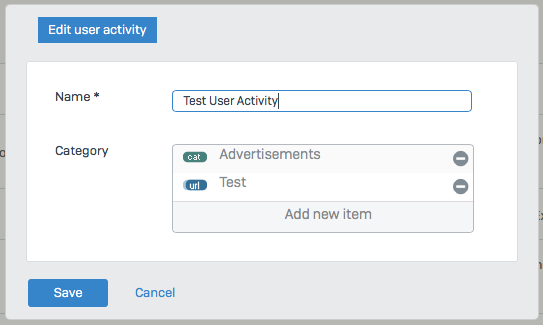
2. Create a User Activity with the URL group added.
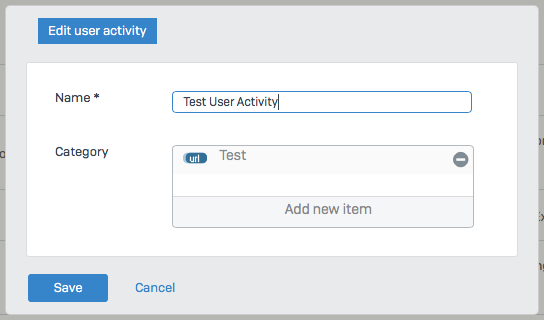
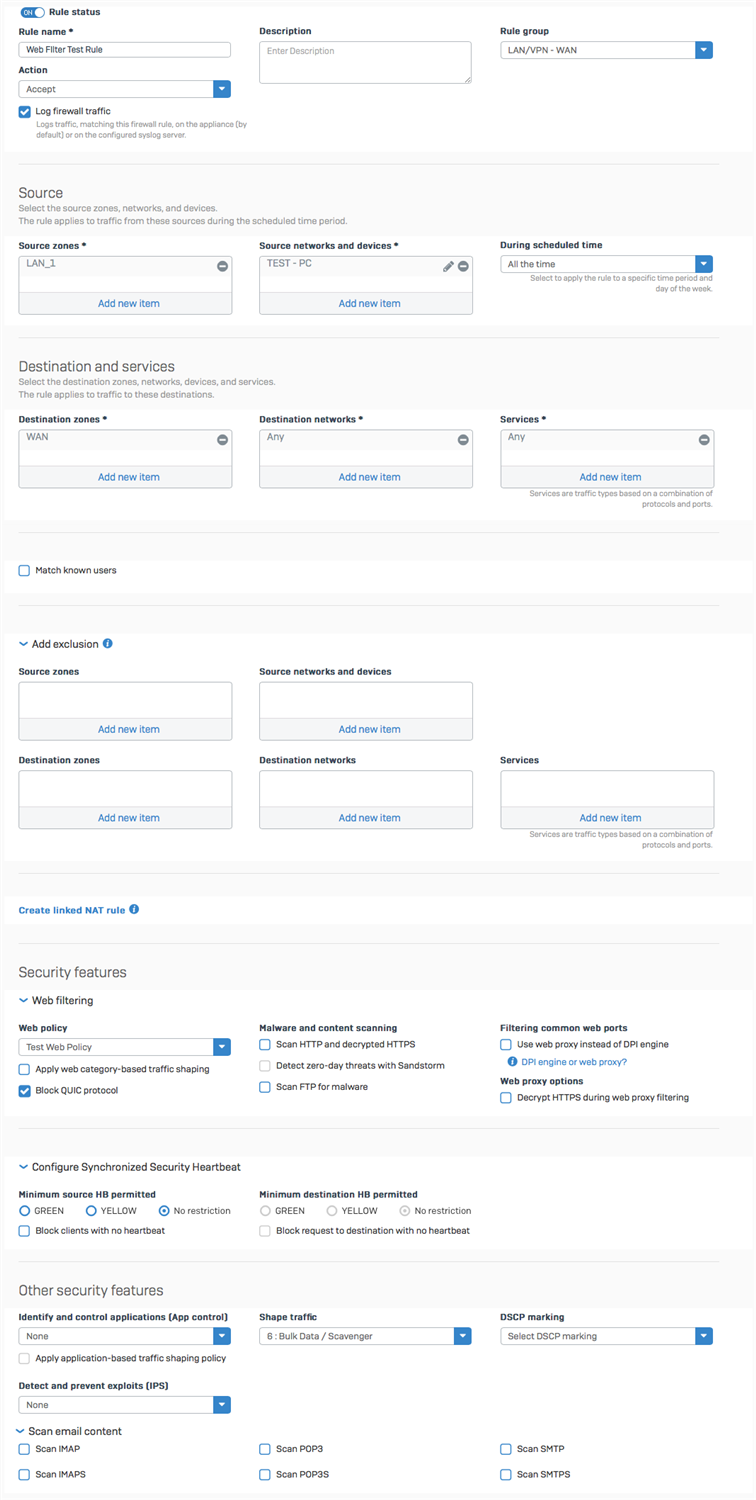
3. Create a web filter Policy, denying the above created User Activity.
4. Apply the web filter Policy to a firewall rule.
On a PC impacted by the firewall rule, load the URL with a period (.) at the end of the URL. For example: http://example.com.
Without the period at the end of the URL, the webpage is blocked (as expected). With the period, it loads in full.
One more thing, the PC points to the XG for DNS.
Is anyone else able to replicate this issue?
This thread was automatically locked due to age.