Hi all,
Shall we start this new thread with the looks and feels of XG v18 MR-3?
community.sophos.com/.../xg-firewall-v18-mr3
This thread was automatically locked due to age.
Important note about SSL VPN compatibility for 20.0 MR1 with EoL SFOS versions and UTM9 OS. Learn more in the release notes.
Hi all,
Shall we start this new thread with the looks and feels of XG v18 MR-3?
community.sophos.com/.../xg-firewall-v18-mr3
Hello, Im running v18 MR-3 over 5 days and Im having a seirous problem.
Currently we have a Ipsec tunnel established and working.
I have created a SDWAN rule to direct my traffic to internet using my WAN interface
and I have configured the route precedence to
Routing Precedence:
1. VPN routes
2. Static routes
3. SD-WAN policy routes
The traffic From HO to Bo over ipsec interface it works correctly, but in random momments some hosts from BO Lan when try access hosts to HO Lan has the access interruped.
With a little troubleshooting I could check that in this momment the Hosts from BO try access the hosts to HO over WAN interface, even the ipsec tunnel is UP and other hosts from the same subnet BO LAN is working over IPSEC tunnel.
It seems that route precedence sotp to works and redicrect the traffic over SDWAN rule.
Does someone has any experience like this!?
Regards
Carlos
Hi Carlos,
We will try to reproduce the problem in our lab. In the mean time, could you please upload the config on HO and BO here ? Or if you could share the access to your device, we will debug the issue.
on the remote Firewall check the routes with route -e and on advanced console with console> system ipsec_route show
we have a case open where the routes into the tunnel are not visible and the XG does not know that the network is behind ipsec0 virtual interface. although on Web GUI in Diagnostics - Route lookup it lists the correct gateway.
Hi LHerzog.
Thanks by reply, I just check system ipsec_route show and the information are not visible
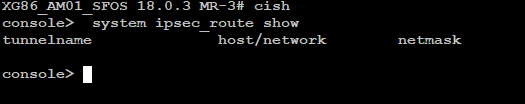
But only for information, we have a devices running with v18 MR1, with the same configs related.
Ipsec + SDWAn rules and it is working as expect. But checking it now, I cannot see the ipsec routes too.
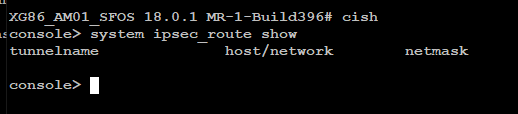
regards
Carlos
Those cish ipsec_routes are "manually configured routes". Not the basic SA routes.
Please check the #ipsec status
__________________________________________________________________________________________________________________
Those cish ipsec_routes are "manually configured routes". Not the basic SA routes.
Please check the #ipsec status
__________________________________________________________________________________________________________________
Please open another thread to keep the visibility here.
Feel free to delete your comments here.
__________________________________________________________________________________________________________________