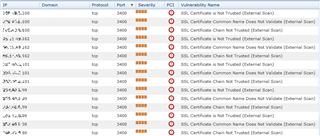
Trying to clean up my PCI compliance scans and get this:
There was a discussion originally by Bill Roland about it ( https://community.sophos.com/products/xg-firewall/f/firewall-and-policies/91708/pci-scan-failing-due-to-red-port-3400 ) but the answer seems to be sorry, that's how it is.
Does anyone have a better solution to hiding these extra port 3400's? We have used the Local ACL to shield the User Portal and SSL VPN from all our external IP addresses except for the single one those services should be going to but it appears the RED service isn't considered a "Local Service" (which I think it should be. AlanT - Shouldn't this be???).
Since its not a local service I can't easily create a local ACL to block the extra IPs and would have to do it through the actual firewall. But since the RED devices are deployed to users homes which can have changing IP addresses there is no reliable way to block this traffic.
The only other answer would be to allow us to use properly signed certificates but that also doesn't seem to be a possibility.
Any ideas?
(I did put in a suggestion for this at https://ideas.sophos.com/forums/330219-xg-firewall/suggestions/36500494-red-service-port-3400-should-be-considered-a-loc because I can't think of a better way to do it)
This thread was automatically locked due to age.