Hi all,
we want to allow an application by the vendor certificate cause this appilcation uses some powershell stuff.
Now we have the problem that we can only do this, when the application is getting detected as an PUA.
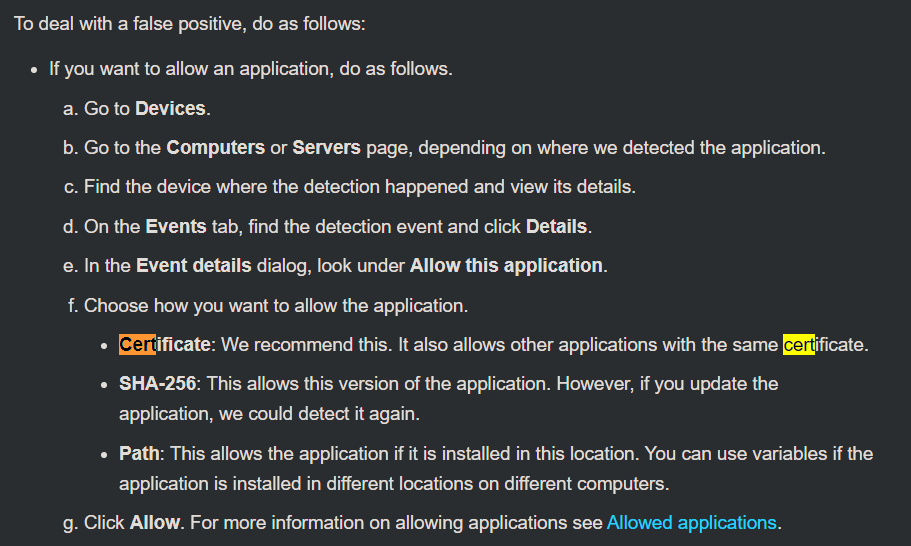
But this is not the case for us.
The Application we want to allow is launching a powershell which executes encoded commands.
So I get only this event details that a powershell got executed.
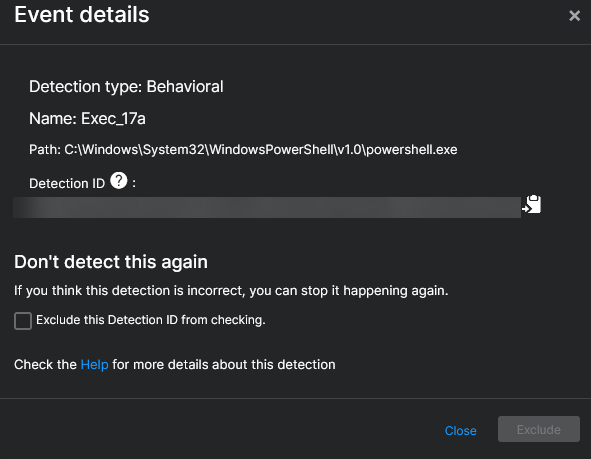
I think excluding this via the Detection ID will not resolv our problem cause we do not want to generally allow powershell to execute this type of executions.
Just when it comes from the specific application.
For me it seems a bit careless to allow the applicaton by path cause when I replace it with an another executable with the same name it will work as well.
And it might be the case that the powershell is getting blocked as well cause I see no association with the parent exe file in sophos central.
What will be the correct way to allow our application?
My personal wish would be by certificate which includes all sub processes which is not configurable under "Allow Applications".
Thanks all for your help!
Added TAGs
[edited by: Qoosh at 9:18 PM (GMT -7) on 26 Oct 2022]



