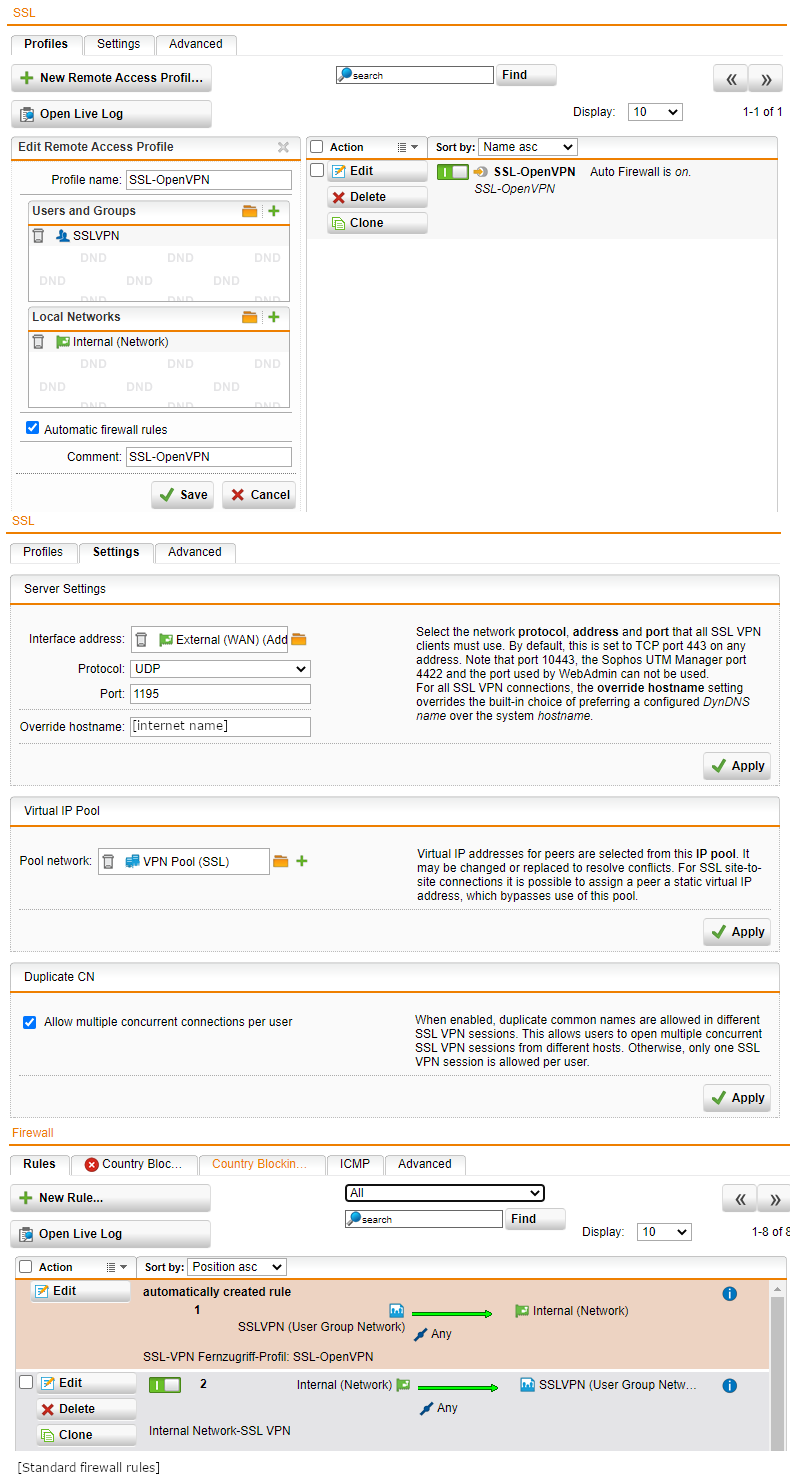
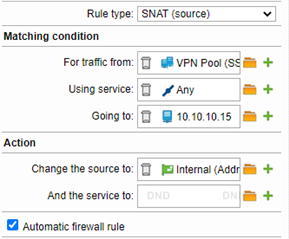
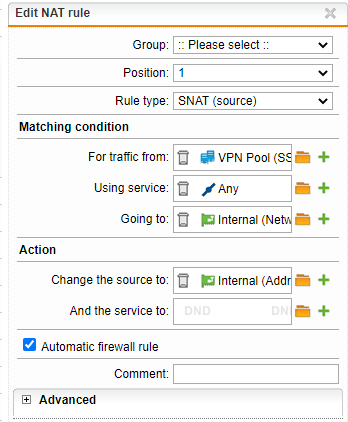
I have set up UTM 9.702-1 for Home use and want to connect remotely to internal network via OpenVPN. Internet Router is an AVM Fritz!Box and UTM uses AVM Fritz!Box as gateway. The OpenVPN Windows 10 client connects with UTM and has access to UTM but not to the internal network.
The connection log in the OpenVPN client software shows at the end that a route is set from VPN Pool (SSL) network 192.168.11.128/25 with gateway 192.168.11.129 to internal network 192.168.9.0/24:
Thu Jul 02 11:11:37 2020 C:\WINDOWS\system32\route.exe ADD 192.168.9.0 MASK 255.255.255.0 192.168.11.129
Thu Jul 02 11:11:37 2020 Route addition via service succeeded
Sadly the route is not usable / not working.
I tried different client software, tried to set the route manually as static or dynamic route under “Interfaces & Routing”, different client connection config file and so on.
Any help is greatly appreciated to gain access to internal network from VPN Pool (SSL) network!
=====================================
Konfiguration for OpenVPN
=====================================
=====================================
ovpn config file for client connection
=====================================
auth-nocache
client
dev tun
proto udp
remote [public ip address] 1195
verify-x509-name "C=de, L=[city], O=[company name], CN=firewall, emailAddress=admin@company.eu"
route remote_host 255.255.255.255 net_gateway
resolv-retry infinite
nobind
persist-key
persist-tun
auth-user-pass
cipher AES-256-CBC
auth SHA512
comp-lzo
route-delay 4
verb 3
reneg-sec 0
<ca>
[certificate]
</ca>
<cert>
[certificate]
</cert>
<key>
[key]
</key>
=====================================
Client Connection log file
=====================================
Thu Jul 02 11:11:28 2020 OpenVPN 2.4.4 x86_64-w64-mingw32 [SSL (OpenSSL)] [LZO] [LZ4] [PKCS11] [AEAD] built on Sep 26 2017
Thu Jul 02 11:11:28 2020 Windows version 6.2 (Windows 8 or greater) 64bit
Thu Jul 02 11:11:28 2020 library versions: OpenSSL 1.0.2l 25 May 2017, LZO 2.10
Thu Jul 02 11:11:28 2020 MANAGEMENT: TCP Socket listening on [AF_INET]127.0.0.1:25344
Thu Jul 02 11:11:28 2020 Need hold release from management interface, waiting...
Thu Jul 02 11:11:29 2020 MANAGEMENT: Client connected from [AF_INET]127.0.0.1:25344
Thu Jul 02 11:11:29 2020 MANAGEMENT: CMD 'state on'
Thu Jul 02 11:11:29 2020 MANAGEMENT: CMD 'log all on'
Thu Jul 02 11:11:29 2020 MANAGEMENT: CMD 'echo all on'
Thu Jul 02 11:11:29 2020 MANAGEMENT: CMD 'hold off'
Thu Jul 02 11:11:29 2020 MANAGEMENT: CMD 'hold release'
Thu Jul 02 11:11:30 2020 MANAGEMENT: CMD 'username "Auth" "[username]"'
Thu Jul 02 11:11:30 2020 MANAGEMENT: CMD 'password [...]'
Thu Jul 02 11:11:31 2020 MANAGEMENT: >STATE:1592212291,RESOLVE,,,,,,
Thu Jul 02 11:11:31 2020 TCP/UDP: Preserving recently used remote address: [AF_INET][public ip address]:1195
Thu Jul 02 11:11:31 2020 Socket Buffers: R=[65536->65536] S=[65536->65536]
Thu Jul 02 11:11:31 2020 UDP link local: (not bound)
Thu Jul 02 11:11:31 2020 UDP link remote: [AF_INET][public ip address]:1195
Thu Jul 02 11:11:31 2020 MANAGEMENT: >STATE:1592212291,WAIT,,,,,,
Thu Jul 02 11:11:31 2020 MANAGEMENT: >STATE:1592212291,AUTH,,,,,,
Thu Jul 02 11:11:31 2020 TLS: Initial packet from [AF_INET][public ip address]:1195, sid=f2940432 d7e7e286
Thu Jul 02 11:11:31 2020 VERIFY OK: depth=1, C=de, L=[city], O=[company name], CN=[company name] VPN CA, emailAddress=[email]
Thu Jul 02 11:11:31 2020 VERIFY X509NAME OK: C=de, L=[city], O=[company name], CN=firewall, emailAddress=[email]
Thu Jul 02 11:11:31 2020 VERIFY OK: depth=0, C=de, L=[city], O=[company name], CN=firewall, emailAddress=[email]
Thu Jul 02 11:11:32 2020 Control Channel: TLSv1.2, cipher TLSv1/SSLv3 DHE-RSA-AES256-GCM-SHA384, 2048 bit RSA
Thu Jul 02 11:11:32 2020 [firewall] Peer Connection Initiated with [AF_INET][public ip address]:1195
Thu Jul 02 11:11:33 2020 MANAGEMENT: >STATE:1592212293,GET_CONFIG,,,,,,
Thu Jul 02 11:11:33 2020 SENT CONTROL [firewall]: 'PUSH_REQUEST' (status=1)
Thu Jul 02 11:11:33 2020 PUSH: Received control message: 'PUSH_REPLY,route-gateway 192.168.11.129,route-gateway 192.168.11.129,topology subnet,ping 10,ping-restart 120,route 192.168.9.0 255.255.255.0,ifconfig 192.168.11.132 255.255.255.128'
Thu Jul 02 11:11:33 2020 OPTIONS IMPORT: timers and/or timeouts modified
Thu Jul 02 11:11:33 2020 OPTIONS IMPORT: --ifconfig/up options modified
Thu Jul 02 11:11:33 2020 OPTIONS IMPORT: route options modified
Thu Jul 02 11:11:33 2020 OPTIONS IMPORT: route-related options modified
Thu Jul 02 11:11:33 2020 Outgoing Data Channel: Cipher 'AES-256-CBC' initialized with 256 bit key
Thu Jul 02 11:11:33 2020 Outgoing Data Channel: Using 512 bit message hash 'SHA512' for HMAC authentication
Thu Jul 02 11:11:33 2020 Incoming Data Channel: Cipher 'AES-256-CBC' initialized with 256 bit key
Thu Jul 02 11:11:33 2020 Incoming Data Channel: Using 512 bit message hash 'SHA512' for HMAC authentication
Thu Jul 02 11:11:33 2020 interactive service msg_channel=460
Thu Jul 02 11:11:33 2020 ROUTE_GATEWAY 192.168.1.1/255.255.255.0 I=18 HWADDR=50:7b:9d:58:72:a3
Thu Jul 02 11:11:33 2020 open_tun
Thu Jul 02 11:11:33 2020 TAP-WIN32 device [OpenVPN] opened: \\.\Global\{7FD1AB5C-B6F6-4BE0-99EC-E7EEBB59BCFC}.tap
Thu Jul 02 11:11:33 2020 TAP-Windows Driver Version 9.21
Thu Jul 02 11:11:33 2020 Set TAP-Windows TUN subnet mode network/local/netmask = 192.168.11.128/192.168.11.132/255.255.255.128 [SUCCEEDED]
Thu Jul 02 11:11:33 2020 Notified TAP-Windows driver to set a DHCP IP/netmask of 192.168.11.132/255.255.255.128 on interface {7FD1AB5C-B6F6-4BE0-99EC-E7EEBB59BCFC} [DHCP-serv: 192.168.11.254, lease-time: 31536000]
Thu Jul 02 11:11:33 2020 Successful ARP Flush on interface [14] {7FD1AB5C-B6F6-4BE0-99EC-E7EEBB59BCFC}
Thu Jul 02 11:11:33 2020 do_ifconfig, tt->did_ifconfig_ipv6_setup=0
Thu Jul 02 11:11:33 2020 MANAGEMENT: >STATE:1592212293,ASSIGN_IP,,192.168.11.132,,,,
Thu Jul 02 11:11:37 2020 TEST ROUTES: 2/2 succeeded len=2 ret=1 a=0 u/d=up
Thu Jul 02 11:11:37 2020 MANAGEMENT: >STATE:1592212297,ADD_ROUTES,,,,,,
Thu Jul 02 11:11:37 2020 C:\WINDOWS\system32\route.exe ADD [public ip address] MASK 255.255.255.255 192.168.1.1
Thu Jul 02 11:11:37 2020 Route addition via service succeeded
Thu Jul 02 11:11:37 2020 C:\WINDOWS\system32\route.exe ADD 192.168.9.0 MASK 255.255.255.0 192.168.11.129
Thu Jul 02 11:11:37 2020 Route addition via service succeeded
Thu Jul 02 11:11:37 2020 Initialization Sequence Completed
Thu Jul 02 11:11:37 2020 MANAGEMENT: >STATE:1592212297,CONNECTED,SUCCESS,192.168.11.132,[public ip address],1195,,
This thread was automatically locked due to age.