Disclaimer: This information is provided as-is for the benefit of the Community. Please contact Sophos Professional Services if you require assistance with your specific environment.
.We have made this process significantly easier. Our installer download now includes an MDM profile for permissions and a script for use to deploy the endpoint via MDM. Here are our instructions for how to use these. It is written for JAMF Pro, however the MDM profile and script should work in other MDM solutions.
docs.sophos.com/.../index.html
Overview
This article describes the steps to configure JAMF to allow configure permissions for Sophos Mac Endpoint on macOS 10.15+
Applies to the following Sophos products and versions
Sophos Central Mac Endpoint 10.0.0 and above,
Sophos Central Intercept X 10.0.0 and above,
Sophos Central Device Encryption 1.5.2 and above,
Sophos Anti-Virus for Mac OS X 9.9.7 and above
Table of Contents
Technical Context
With macOS 10.13, Apple introduced a new security level that required each 3rd party vendor's kernel extension to be approved. This required Team ID to be allowed, also known as the Apple Developer ID.
With macOS 10.15, Apple added a new default behavior that prevented applications from writing to the disk.
The information below covers both topics:
- Allowing the Sophos Team ID (2H5GFH3774)
- Granting the disk access for each required process
To alert and inform users, Sophos implement a notification popup. The endpoint will check after each reboot (and continuously every 30 minutes) if the system permissions are compatible.
- This following steps can also be applied to machines running macOS 10.14.x. You may want to prepare your devices to be ready for an upgrade to macOS 10.15+. The instructions below can be followed to prepare device profiles for a future macOS 10.15+ upgrade.
Note: In Sophos for Mac 9.9.5, a notice is displayed if required permissions are not fully enabled. On October 31st, an issue was found where the notice is triggered if the permissions have been added via an MDM profile, as Apple records these in a different location. Sophos is actively working on updating the detection to correct this.
What to do
There are 2 steps required to configure compatibility for macOS 10.15.x (Catalina) and below.
Note: One additional step is required if you want to apply the profile to a macOS 11 (Big Sur) device.
- Grant full disk access for Sophos components
- Allow the Sophos kernel extensions
- (Big Sur - macOS 11) Configure the system extension at the last step.
Grant full disk access for Sophos components
- Open JAMF and log in.
- Go to Computers > Configuration Profiles
- Create a new Configuration Profile, or select an existing one
- Select Privacy Preferences Policy Control (near the bottom of the list)
- Click the + beside App Access
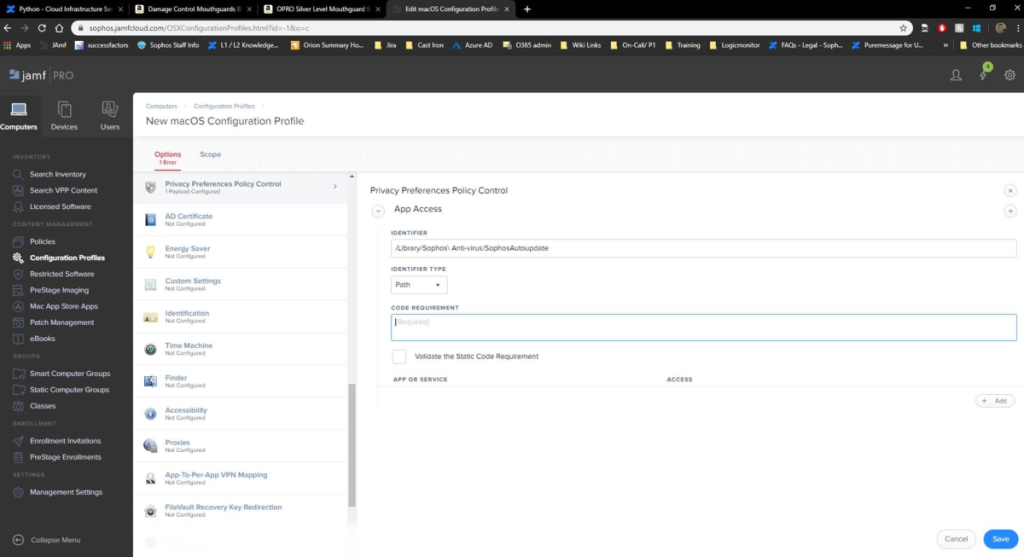
- In Identifier and Code Requirement put in all the entries listed below, and for Identifier type, select BundleID.
Note: Sophos does not recommend using the path based format
Identifier Code Requirement Valid Since Product com.sophos.endpoint.scanextension identifier "com.sophos.endpoint.scanextension" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = "2H5GFH3774" v10.0.2 All com.sophos.liveresponse identifier "com.sophos.liveresponse" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = "2H5GFH3774" v10.0.1 Central only /Library/Sophos Managed Detection and Response/SophosMDR identifier SophosMDR and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = "2H5GFH3774"
v10.0.1 Central with MDR only com.sophos.autoupdate identifier "com.sophos.autoupdate" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = "2H5GFH3774" v10.0.0 OPM only com.sophos.macendpoint.CleanD identifier "com.sophos.macendpoint.CleanD" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = "2H5GFH3774" v10.0.0 All com.sophos.SophosScanAgent identifier "com.sophos.SophosScanAgent" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = "2H5GFH3774" v10.0.0 All com.sophos.macendpoint.SophosServiceManager identifier "com.sophos.macendpoint.SophosServiceManager" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = "2H5GFH3774" v10.0.0 All com.sophos.endpoint.uiserver identifier "com.sophos.endpoint.uiserver" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = "2H5GFH3774" v10.0.0 Central only com.sophos.SDU4OSX identifier "com.sophos.SDU4OSX" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = "2H5GFH3774" v10.0.0 All com.sophos.endpoint.SophosAgent identifier "com.sophos.endpoint.SophosAgent" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = "2H5GFH3774" v10.0.0 All com.sophos.SophosAntivirus identifier "com.sophos.SophosAntiVirus" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = "2H5GFH3774" v10.0.0 All com.Sophos.macendpoint.SophosSXLD identifier "com.Sophos.macendpoint.SophosSXLD" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = "2H5GFH3774" v10.0.0 All - In Code Requirement, this can also be self-generated. Run the following on a Mac with version 10.0.0 (Sophos Central) and above:
codesign --display -r - <app path from table above>
- Once it has been added, permissions can be selected accordingly. Each one should be given "All Files" / "SystemPolicyAllFiles" as the access.
- Save and deploy the configuration as needed.
Allow the Sophos Kernel Extensions
The same profile can be used, but the option "Approved Kernel Extensions" needs to be selected. If this is not configured yet, select the "open" button at the center to begin the configuration.
During configuration, 3 kernel extensions will need to be added, as well as the Sophos Team ID [2H5GFH3774]
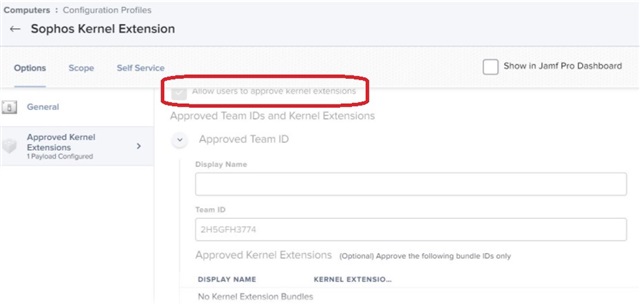
Note: Please ensure that "Allow users to approve kernel extensions" is unchecked.
Referring to the screenshot above, add the following kernel extensions:
- com.sophos.nke.swi
- com.sophos.kext.sfm
- com.sophos.kext.oas
Make sure to save your changes.
(Big Sur - macOS 11) Configure the system extension
Note: Apple has added a new, optional, method of setting authorization of applications for Privacy in Big Sur with MDM. This new method replaces an existing true/false option with a string value option instead. Here is the Apple article on it: https://developer.apple.com/documentation/devicemanagement/privacypreferencespolicycontrol/services/identity Allowed is the normal method of setting permissions, however as of Big Sur, Apple allows you to instead use Authorization. Our detection for permissions has been configured for the “Required” property (which isn’t actually required if you have Authorization instead). If you can set your MDM provider to use the Allowed True/False (Boolean) setting, it should work without any issues. To check if this applies to you, open the .mobileconfig file in a text editor and search for Sophos. Check if you see - <key>Allowed</key><True/>, or <key>Authorization</key><String>Allow</string>. If it is Authorization, this applies to you. We do recognize that there is a move to this alternate form, and as such, we have made an improvement, coming out in our 10.1.3 release in July, to detect both versions. Until this releases, we recommend using the Allowed True/False style privacy permission setting for Sophos processes.
The same profile configuration can be used.
- From the Options, select “System Extensions”.
- This step is similar to the ones above, but for the new system extensions
- The following empty template will be displayed
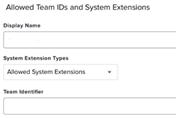
- For the display name, specify the following entries
-
com.sophos.endpoint.networkextension
-
com.sophos.endpoint.scanextension
-
- Add 1 entry for each. Make sure that the System Extension Types are set to “Allowed System Extensions”
- The picture displays a complete profile example. For the Team Identifier, specify the Sophos Team ID [ 2H5GFH3774 ]
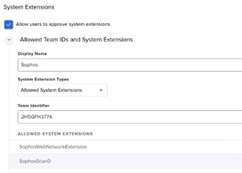
- The picture displays a complete profile example. For the Team Identifier, specify the Sophos Team ID [ 2H5GFH3774 ]
- Reference the following screenshot for an example of the Options overview
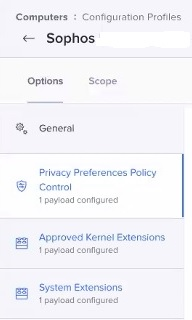
- Don't forget to save your changes
Alternate method
Note: Sophos does not guarantee the security of third party applications and they should be used at your own risk.
There is a utility called PPPC Utility on Github which allows you to build a configuration profile for Privacy Preferences. It can be located here: https://github.com/jamf/PPPC-Utility. To use this, follow the guidance on the link, and drag and drop the Sophos items into it.
This profile can then be loaded into JAMF.
Related videos
Special thanks to MichaelCurtis
Sophos Central MDM Configuration
How to Configure JAMF Privacy Preferences for 10.15 Compatibility
Related information
JAMF Pro keys for 10.0.2 EAP to pre-approve the proxy configuration
Special thanks to mscottblake for sharing this!
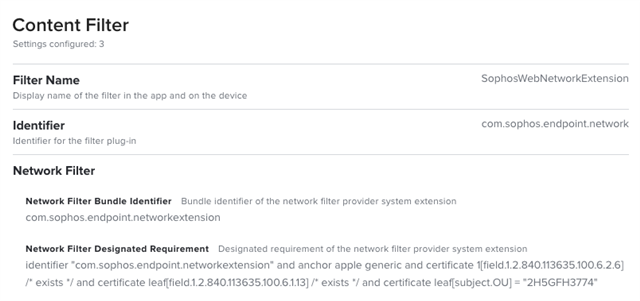
Within the same Configuration Profile, add a Content Filter payload (this requires Jamf Pro 10.26+) with the following keys and values configured:
| Filter Name | SophosWebNetworkExtension |
| Identifier | com.sophos.endpoint.network |
| Network Filter Bundle Identifier | com.sophos.endpoint.networkextension |
| Network Filter Designated Requirement | identifier "com.sophos.endpoint.networkextension" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = "2H5GFH3774" |
Note that the Filter Name can be anything, but it is required.
Once the complete, the payload should look like this:
- JAMF page about this configuration: https://www.jamf.com/jamf-nation/articles/553/preparing-your-organization-for-user-data-protections-on-macos-10-14
- PPPC Utility: https://github.com/jamf/PPPC-Utility
Edit Disclaimer
[edited by: GlennSen at 3:48 PM (GMT -7) on 5 Apr 2023]

