Disclaimer: This information is provided as-is for the benefit of the Community. Please contact Sophos Professional Services if you require assistance with your specific environment.
Table of Contents
Overview
This Recommended Reads is Part 2 of the Series "Access the Sophos Firewall Web Admin from ZTNA.
Note: The information in this Recommended is relevant to Setting up a Directory Service in Azure and a Security without following the full series.
Requirements
Administrator rights to access Azure AD (Entra)
Setup a Directory Service
The Directory Service is used to manage the users and groups that you will give access to.
I am using Microsoft Entra ID, better known as Azure AD, which is also the Identify Provider I will be using.
First access Azure https://portal.azure.com/#home
Go to Microsoft Entra ID

If you already have a tenant, you can skip the next step, if you don't click Add Tenant,
Select a tenant type = Microsoft Entra ID
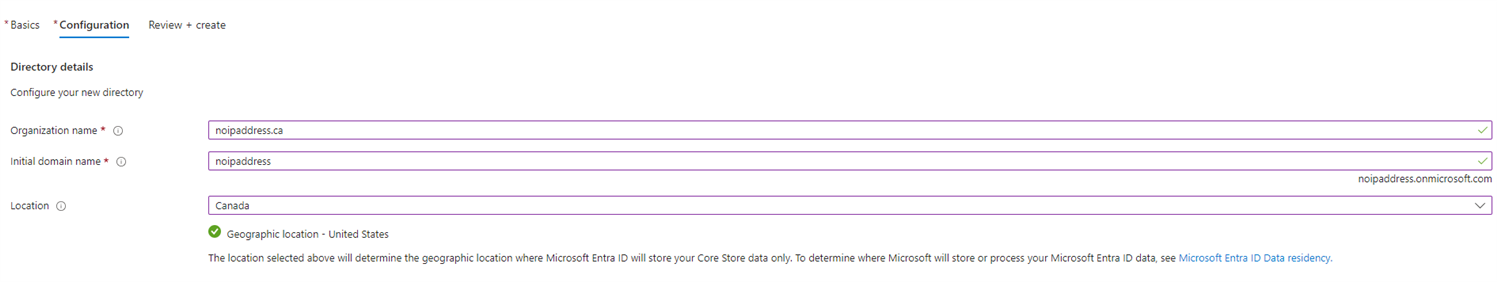
Organization name = noipaddress.ca (Your Organization name (domain))
Initial Domain name = noipaddress.onmicrosoft.com ( that will end up as yourdomain.onmicrosoft.com)
Next, we need to register the ZTNA App
Go to Manage > App Registrations
And click + New Registration
Name = ZTNA APP (or something meaningful)
Supported Account Types = Accounts in this organizational directory only (yourdomain only - Single tenant)
Redirect URI = Web
Redirect URI (text box) = ztna.noipaddress.ca/.../callback
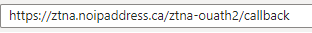
NOTE: The above step (Redirect URI (text box)) is very important since we’re setting up ZTNA in Gateway mode = Sophos Cloud, (the Sophos Firewall as the ZTNA Gateway); this URL will also work as the ZTNA Portal (The URL the user will enter in their browser to access Agentless apps in ZTNA).
API Permissions
Within the APP you just created, go to API Permissions.
Click + Add a Permission.

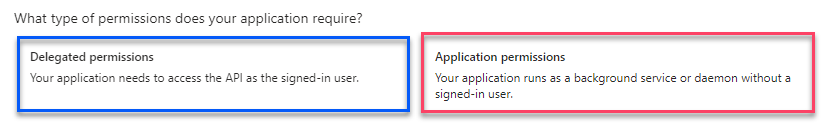
In the new side window that opened (Request API permissions) click Microsoft Graph
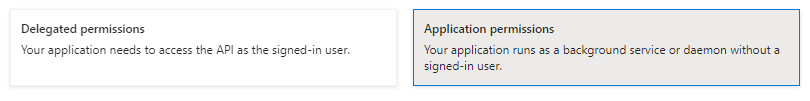
First, click Application Permissions
in the text box, search for the below and select it
- Directory.Read.All
Then, click Delegated Permissions
in the text box, search for the below and select it (you can enter in the text box the name as it is)
- Directory.Read.All
- Group.Read.All
- openID
- profile (profile is in the openID set of permissions)
- User.Read
- User.Read.All
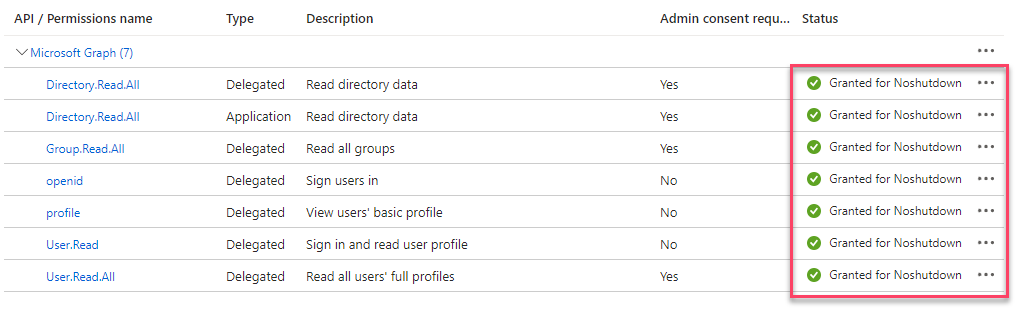
You should end up with the following list (make sure the Type matches)
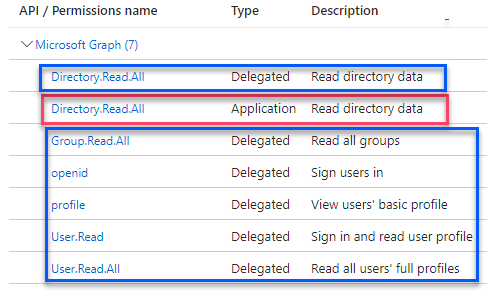
Note: if you fail to add any of the above permissions, your users will get errors when trying to authenticate
Next, click Grant Admin consent for
The status of all the API, would change to Granted
Next, we need to create a secret in Azure; this is so the app can identify itself to the authentication service when receiving the token at the URL we provided above.
In the same App Go to Overview
Then go to Client Credentials: Add a certificate or secret.
Client Secrets
+ New Client Secret
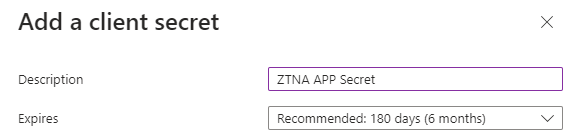
In the new side window that opens, enter a Description
Description = ZTNA APP Secret
Expires = Recommended: 180 days (6 months)
and click Add
Note: Every 6 months, you’ll need to regenerate the secret
WARNING: Take a screenshot or copy the Value field ID, as once you move from the window, the Value field won’t show the Value entry, and you need to add this to Sophos Central.
Back to the Certificates & Secrets screen, you’ll see the recently created secret; copy the Value and Secret ID in your Notepad++ for the time being

Create an Azure AD Group (Microsoft Entra ID group)
Note: If you already have a group, you don't need to follow this step, just make sure to copy the Object ID of the group you want to use.
Go to Azure Active Directory
Click Groups
Click New Group
New Group
Group type = Security
Group Name = ZTNA

And add users by clicking "No members selected"
A new side window will show, search, and select the users that will belong to this group
Once you select your users, click Select and then Create (IF you don't see your group refresh your page)
Please make a note of the object ID as we will need it, to add the group to Sophos Central.
TAGs
[edited by: emmosophos at 11:16 PM (GMT -8) on 10 Nov 2023]
