Disclaimer: This information is provided as-is for the benefit of the Community. Please contact Sophos Professional Services if you require assistance with your specific environment.
______________________________________________________________________________________________________________________________________
Table of Contents
Overview
The new engine provides a high degree of flexibility when it comes to solving some interesting network problems. I don't know if it has been shared here or not, but you can use NAT to achieve NTP proxy like functionality. A standard use case seen is that clients would like to use the IP address of the firewall as the NTP server. Consider this as an example environment:
- Firewall has at least 2 interfaces, LAN and WAN. LAN interface has an RFC1918 address, and the WAN interface utilizes a public address.
- Clients behind the firewall would like to use the LAN interface IP as the NTP 'server'. In this regard, the default gateway and NTP destination use the same address on your clients.
- The NTP server you want to sync with is external to the organization, e.g. pool.ntp.org.
Types of Transparent NTP
There are two different approaches to a transparent NTP solution.
1.:
NTP should be forwarded to a particular externally(WAN) host/host group.
2.:
NTP should be forwarded to a own ressource within the network and this server should provide the information.
1st Scenario
First scenario is rather simple.
You need one NAT Rule, which translate everything NTP based to a particular host.
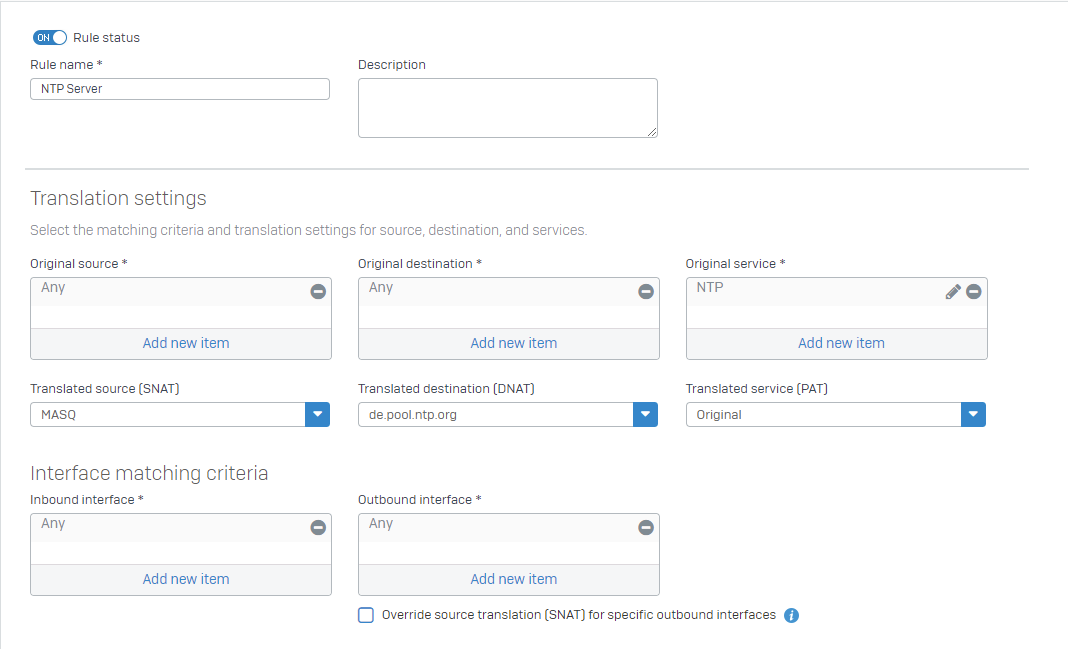
You can specify all internal hosts with "Interface matching criteria - Inbound Interfaces".
This example shows ANY. You can select all internal network interfaces (expect WAN).
This rule will fetch all NTP related traffic, forward it to a public NTP service and use MASQ. MASQ is required for WAN related traffic.
You need a firewall rule:
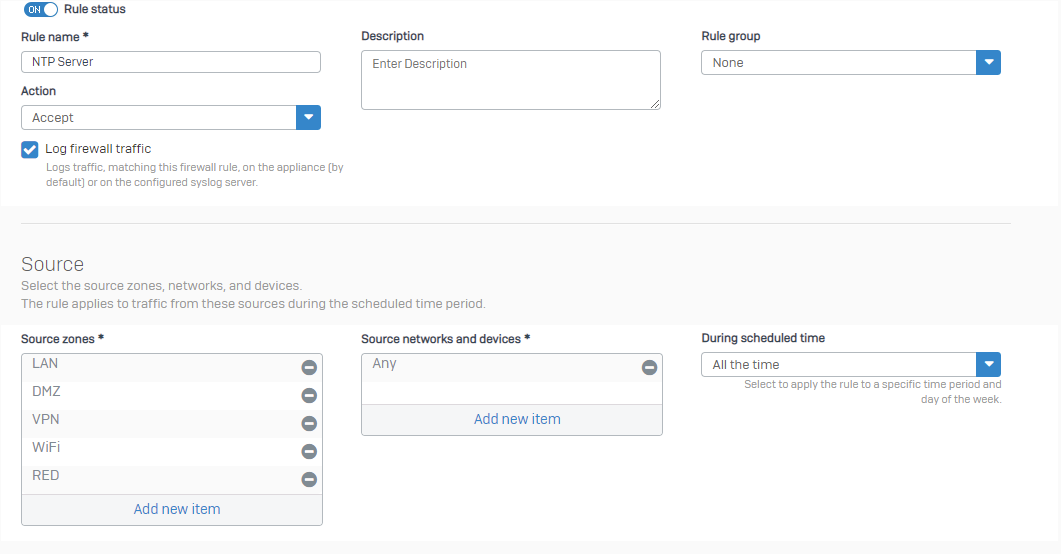
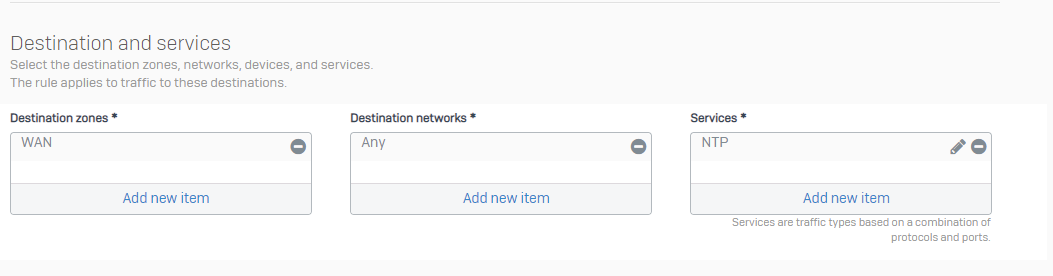
You can attach IPS rules to this, if you want.
Build your own NTP rule, with all NTP related IPS pattern.
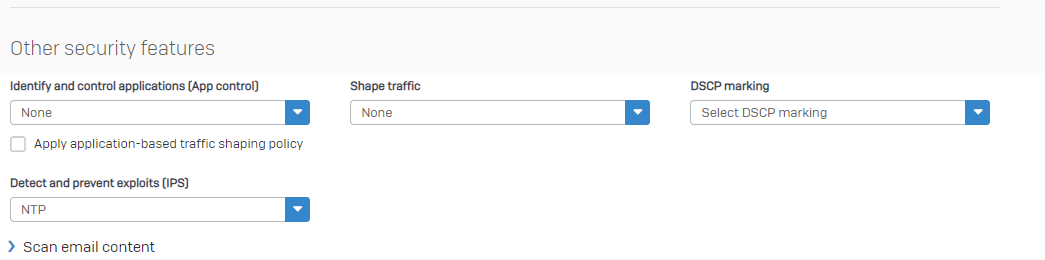
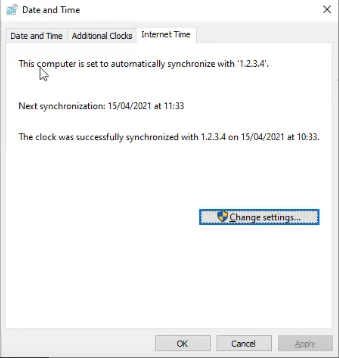
Regardless of the configured IP on a client behind Sophos Firewall, the NTP request will work.
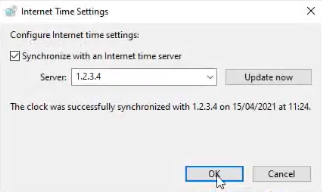
(Example: 1.2.3.4)
2nd Scenario
Second scenario needs more rules, as you can easily generate a NTP loop.
Your internal server need a own NAT rule and own firewall rule.
Example = Windows2016 is a NTP server.
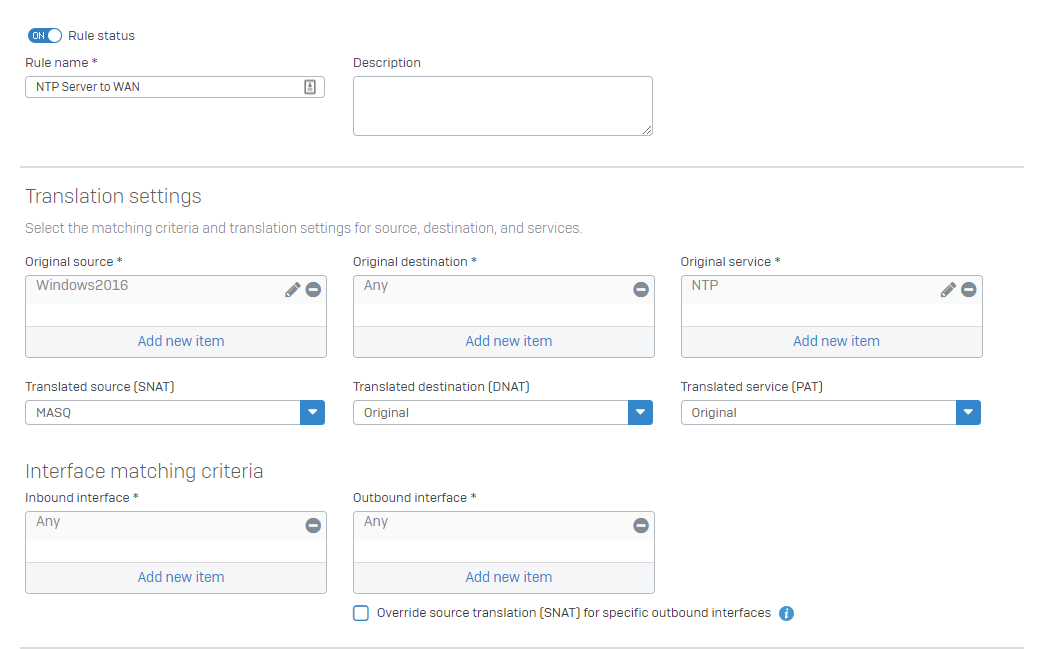
NAT Rule 1#
NTP Server to WAN (to get the NTP server to the WAN NTP servers.)
You can also force the internal NTP server to get the IP from a particular NTP pool, but we assume, the NTP server has his own NTP request pool.
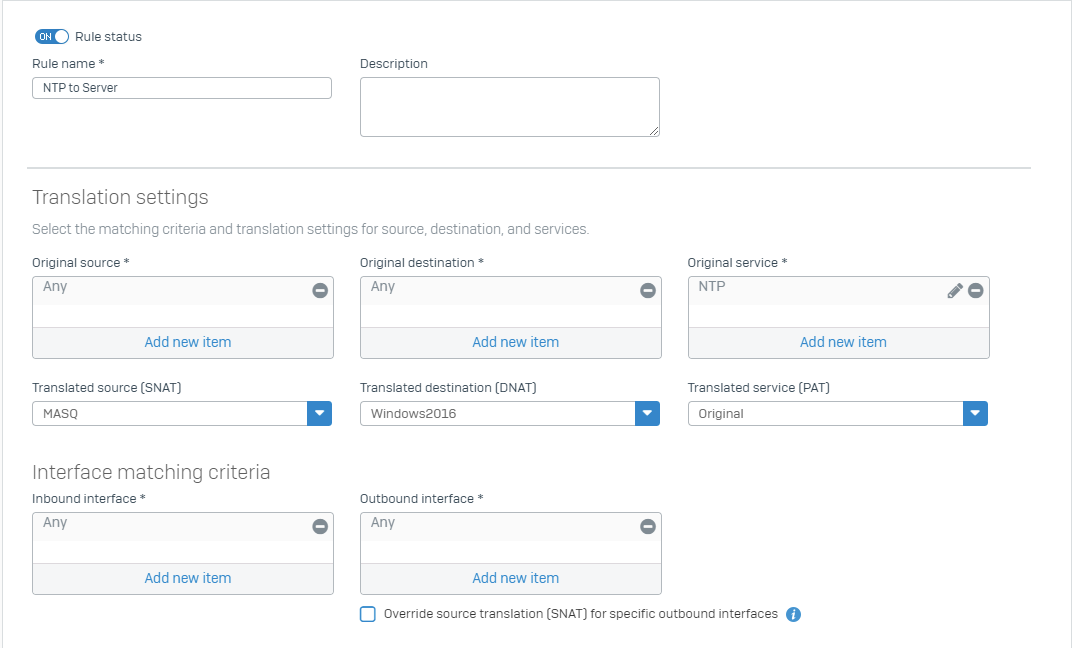
NAT 2#
It will forward the NTP traffic transparent to the internal NTP server.
Firewall rules:
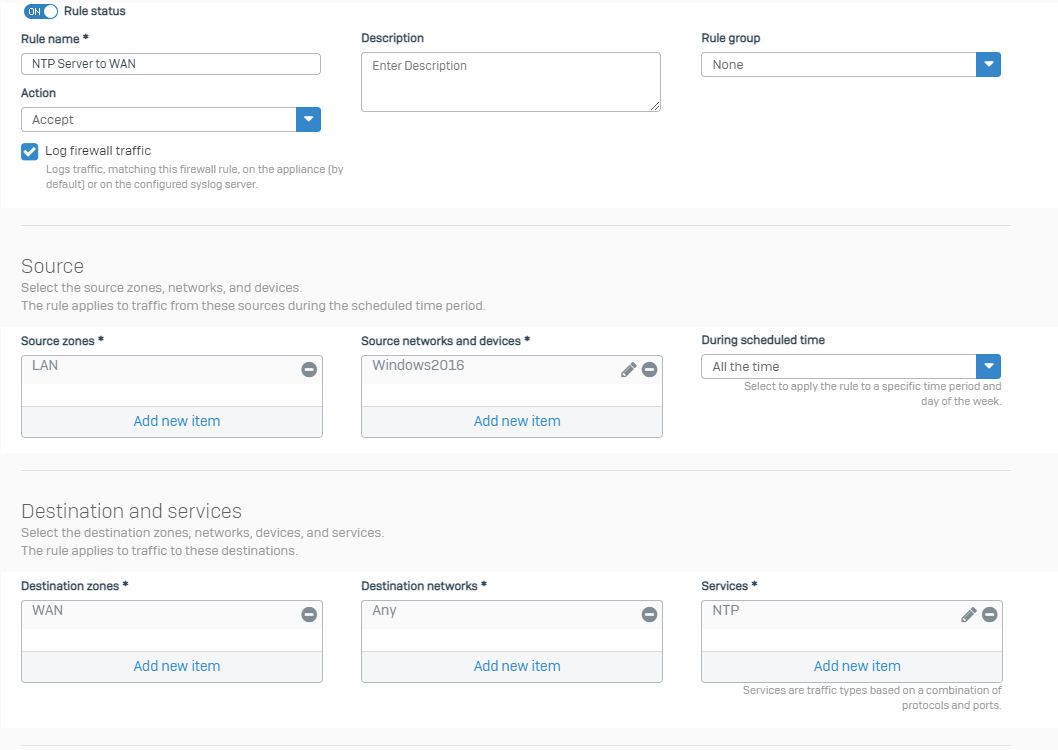
Firewall rule #1
Allowing the traffic of the NTP server to the WAN to get current time.
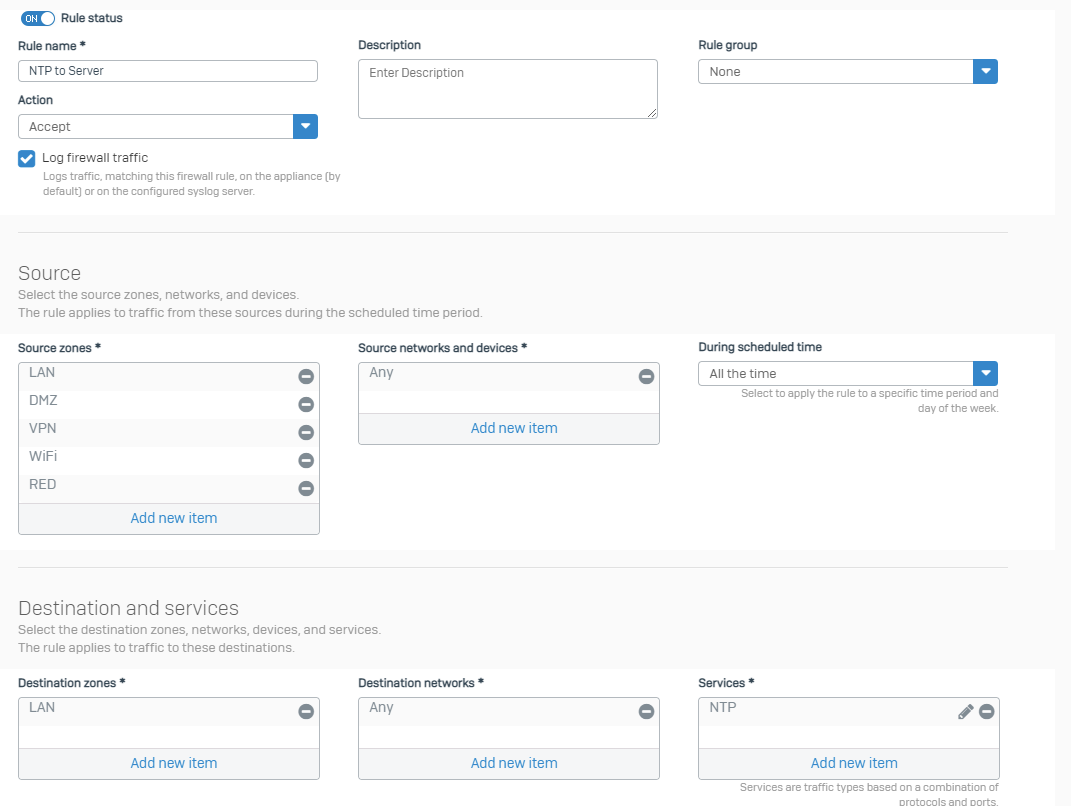
Firewall rule #2
Allowing the Traffic from all internal clients to the internal NTP server.
Notice the destination zone.
Naturally, you can create variations of this NAT policy, based on your network configuration and the location of the NTP server.
______________________________________________________________________________________________________________________________________
Edited format, edited title, added horizontal lines, added table of contents
[edited by: Raphael Alganes at 3:06 PM (GMT -8) on 24 Nov 2023]


