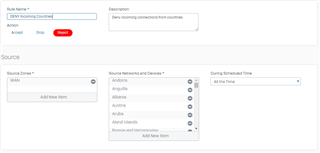
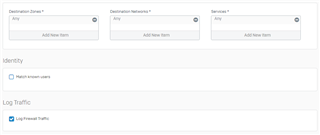
I have created a Deny Rule on the WAN zone to block foreign countries and put it at the top of my rules. But instead of dropping connections, it instead will show the User Portal. It doesn't matter if I choose Reject or Deny. This rule worked properly with firmware ver 16.5.08, but since upgrading to ver 17, it has not worked properly. I am currently on ver 17.1.2.
This thread was automatically locked due to age.