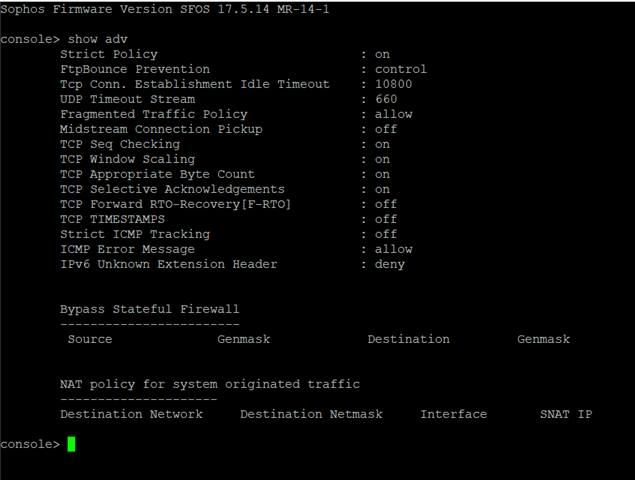
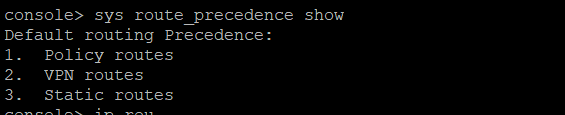
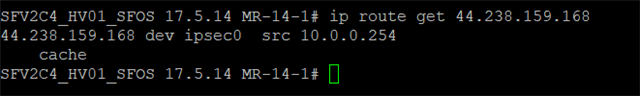
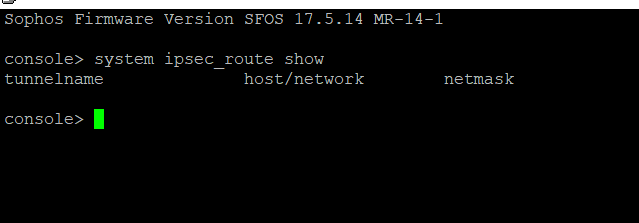
I'm having a few issues with an XG in place at the moment. Various things are failing such as checking for firmware/pattern updates, being able to use the web filtering feature and also using the inbuilt FTP backup feature.
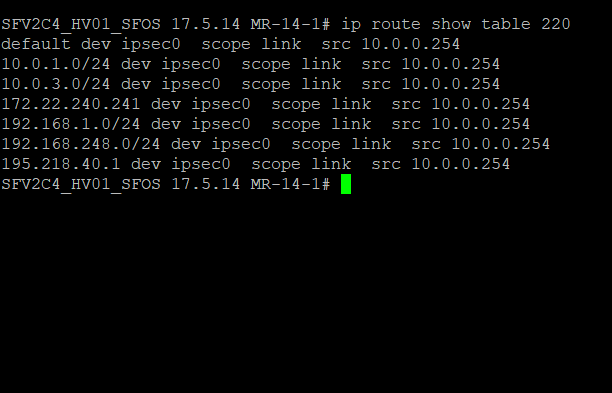
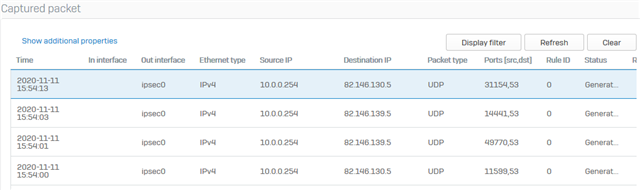
I have discovered that the XG is unable to resolve any DNS queries, I have tried multiple external DNS but no luck. The issue appears to be the way the XG is handling it's own traffic, it appears its creating the request from the internal LAN IP and then sending this to ipsec0. Also doing a packet capure of the FTP backup and it is doing the same, as though the XG initiated traffic is somehow getting caught in an IPSEC policy. I have checked all VPNs and nothing matches the src and dst so unclear why this is behaving in this way.
If I point the XG to an internal DNS server this works but the FTP backup as its external and fails as its doing the same thing.
Got a call logged with Sophos support but after 3 weeks they arent showing much interest and have caused more problems with their attempted fixes which from what I can see have no relvance and have had to intervene when the engineer started deleting and regenrating certificates causing all sorts of SSLVPN issues.
I know there are commands to be able to send XG intiated traffic down a VPN however this has not been implemented, I want the opposite of that. Anyone ever seen this before? There are no tunnel interfaces and also no static routes, just a simple LAN and WAN setup with a few site to site VPNs, SSLVPN and some port forwarding.
This thread was automatically locked due to age.