Hi Guys,
i have 2 XC 135 with the last firmware update installed on both of them.
The HA connection is made with the QuickHA funktion, in Active-Passive configuration, using a 7.5m straight cable on prot 7 as dedicated HA connection........the HA connection was normally working since two days ago, when i had a problem (i was working from home) i was kicked out from the VPN and the HA config ping from the Primary to the secondary a couple of times.
The day after, back in office, the Auxiliary device was shutted out.....i had to disconnect pysically the firewall from the current and reattach it.
after the restart........using the SSh console, i need to restat it again and the HA was again ok.
After a couple of hours, i had again the ping of the functionality between the Primary and the Auxiliary and the Peer start to be in Fault alarm.
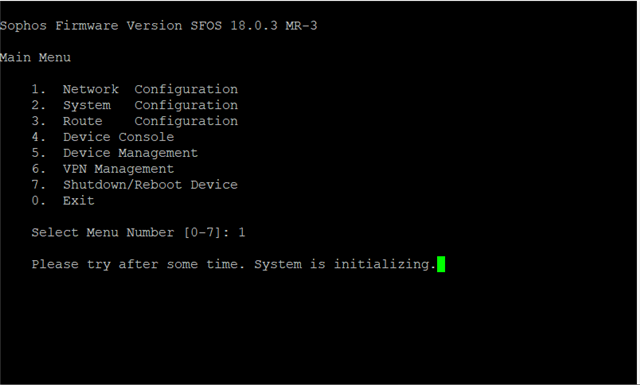
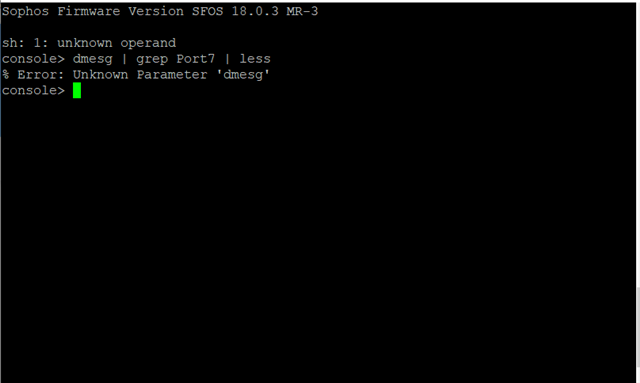
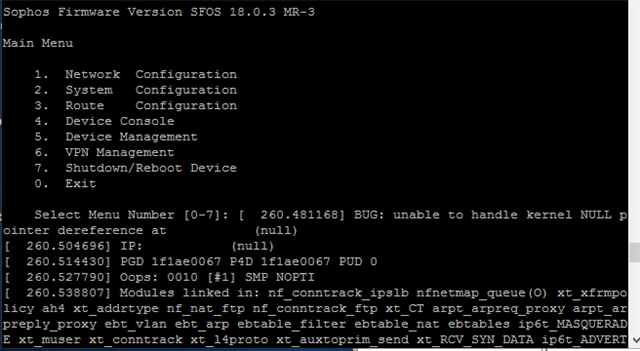
i finished my idea.........i don´t know anymore what to do......here below the logs that i found:
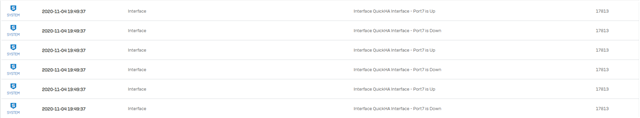
any ideas?
PS (the ha was estabilished using the instruction in this support call https://community.sophos.com/xg-firewall/f/discussions/123582/ha-doesnt-work-in-any-conditions/450470#450470)
This thread was automatically locked due to age.