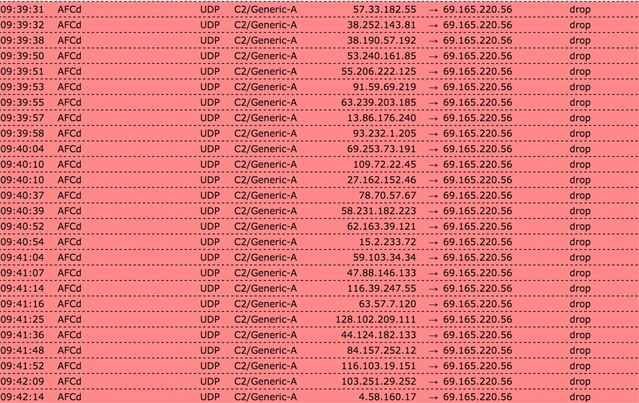
Hi everyone, looks like I have a similar situation to a few people.
NO Windows machines on the network, just OSX and Linux (QNAP). Woke up to over 1400 emails regarding ATP C2/Generic-A. But the originiating seems to be from AFCd? Any idea what this is?
Googling has given me no ideas. Any ideas anyone?
This thread was automatically locked due to age.