He utilize Cacti server for network bandwidth monitoring and packet loss so we can have historical information for our clients. Please hella good when dealing with ISPs and packet loss. :)
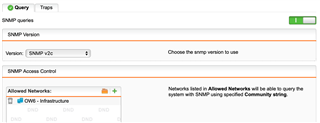
We come from a Mikrotik world but one of our clients use a SG135 box. We want to set up the same SNMP monitoring but I for the life of me cannot get it to work. I have enabled the SNMP Query under Management > SNMP. I have tried both v2c and v3 set my allowed networks, and so on. From the Cacti side, all I get is "SNMP error". I have done a tcpdump on the Sophos box and do not see anything coming from my public IP on 161 or anything for that matter. I have gone as far as creating a firewall entry that has source as cacti, service SNMP, and the destination: External (WAN).
I also see that nmap shows 161 as "filtered" from my office as well as well as from the cacti server.
Has anyone heard of or seen this before and can help me out?
This thread was automatically locked due to age.