I manage two Sophos UTM SG in two different Branchs of the Company.
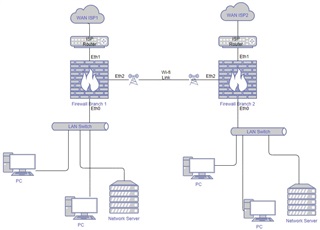
CURRENT SITUATION
"BRANCH A" is connected to internet by "ISP A" on interface ETH1 of its UTM. ISP is the Internet Service Provider
"BRANCH B" is connected to internet by a different ISP named "ISP B" on interface ETH1 of a second/its UTM.
UTM of "BRANCH" A is also connected to UTM of "BRANCH B" by a IpSEC VPN (this is only an additional info but is not the focus of this case)
SITUATION TO BE EXPLORED IF FEASIBLE (see below picture)
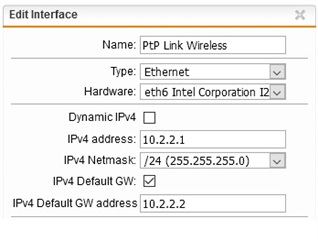
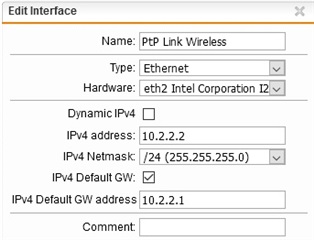
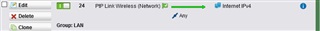
I want to setup a wi-fi/wireless PtP link (Hyperlan 5ghz link using Ubiquity Hardware) and connect "BRANCH A" UTM (by its ETH2 interface) to the "BRANCH B" UTM (by its ETH2 interface). Distance between branchs is 3 km (see below picture/diagram).
Wi-fi PtP Link acts like a "Ethernet cable patch" between the two firewalls.
The Focus in to obtain an "crossed Internet Failover Service" between the two Branchs, I mean if one of the two ISP connections go down the branch in failure will use the ISP connection of the other Branch (and vice-versa).
Any suggestion to setup this interesting Scenario??
Many thank in advance for the support
This thread was automatically locked due to age.