Since version 18, Sophos Firewall has been able to do port-agnostic SSL/TLS decryption and web filtering. This extends our inspection for web threats beyond ports 80 and 443. We've used this ability to release IPS signatures that can detect some HTTP attacks in decrypted traffic on any port.
In version 19, we've introduced a feature that will apply a broader range of web-related IPS signatures to decrypted TLS traffic, regardless of the port. Overall this provides a significant enhancement in our ability to protect against attacks that may try to circumvent regular IPS protection.
The feature is not enabled by default yet. We would really like to get some more exposure to a wider range of situations and traffic.
If you're using EAP2 and TLS decryption, it would be great if you could turn this feature on. Here's how to do it:
- Connect to the device console using SSH, or using the 'Console' option in the drop-down menu in the top-right of the Control Center
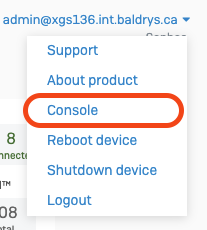
- Enter the admin password, then Select option 4 - Device Console from the Main Menu:
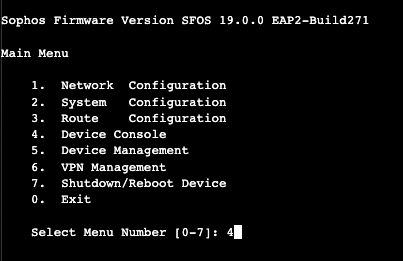
- Enter the following command at the console> prompt:
console> set ips scan_decrypted_port_agnostic on
- There will be a small delay while the configuration is changed and the IPS engine reloads
Enabling this feature may lead to an increase in the number of IPS signature events on your Firewall. Each firewall sends telemetry to SophosLabs when IPS signatures fire, enabling us to respond to potential false positives very quickly and update signature sets.
You can disable this feature again if necessary with the following command:
console> set ips scan_decrypted_port_agnostic off
Thanks for your help! Please feel free to tell us about your experiences in responses to this post.
Added tags
[edited by: RichBaldry at 6:10 PM (GMT -8) on 2 Feb 2022]