Is anyone running or have experience with XG18 WAF with Microsoft RDP Gateway in the last few month’s? I’ve been running fairly successfully with both the Windows, Android, and iOS version of the Microsoft RDP client app, but looks like something has broken the way the Android app works/negotiates through.
I use the static hardening hack/trick to reject /RemoteDeaktopGateway/ URL and this is about the only way the iOS app works. It falls back to RPC over SSL as expected and works fine. Trying to isolate the issue with the Android app by trying a few troubleshooting steps hasn’t changed the behaviour at all. Everything else is as per the KB https://community.sophos.com/kb/en-us/126103 .
At this point I’ve turned off the common threat filter with no change.
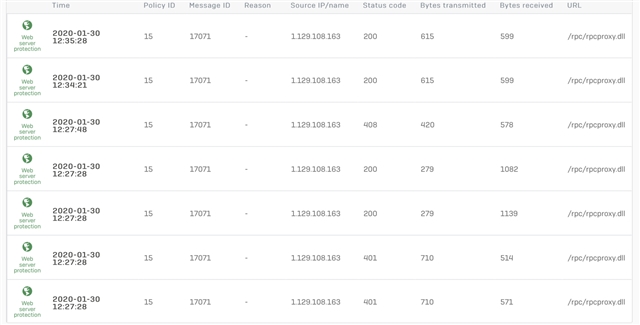
The common error in the RDP app is 0x3000008 - which happens after what appears to be a few attempts to negotiate. As shown in the log as rpcproxy.dll tries to do it’s thing. Obviously using OutlookAnywhere option to pass the RPC and not the RDP traffic. Assume that is still the correct method of using RDP Gateway with XG WAF?
What is weird is the backend RDP 2016 Gateway event logs seems to indicate the start of a successful negotiation, then it disconnects. All certificates etc are valid and configured.
im chasing down a few leads with Microsoft, but I thought I would check with the sophos beta community if they have had experienced any changes recently.
The Microsoft App also seems to be to smart for its own good and potentially seeing the CGNAT of a mobile carrier as “local”. It’s going to be a bit of a finger pointing game I suspect.
Thanks again