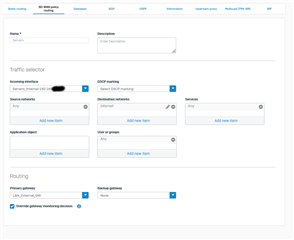
We have two WAN links and have setup SD-WAN policy routing.
We have a rule setup so that all traffic from our server should go over one of the WAN links. This server has software running that pings a variety of external services.
When we reboot the XG Firewall (EAP3 Virtual Machine), a trace route shows that the majority of pings are routed through the correct WAN link but some are being incorrectly routed through the wrong WAN link.
My rule is below