Hello all,
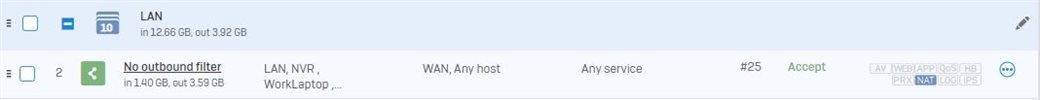
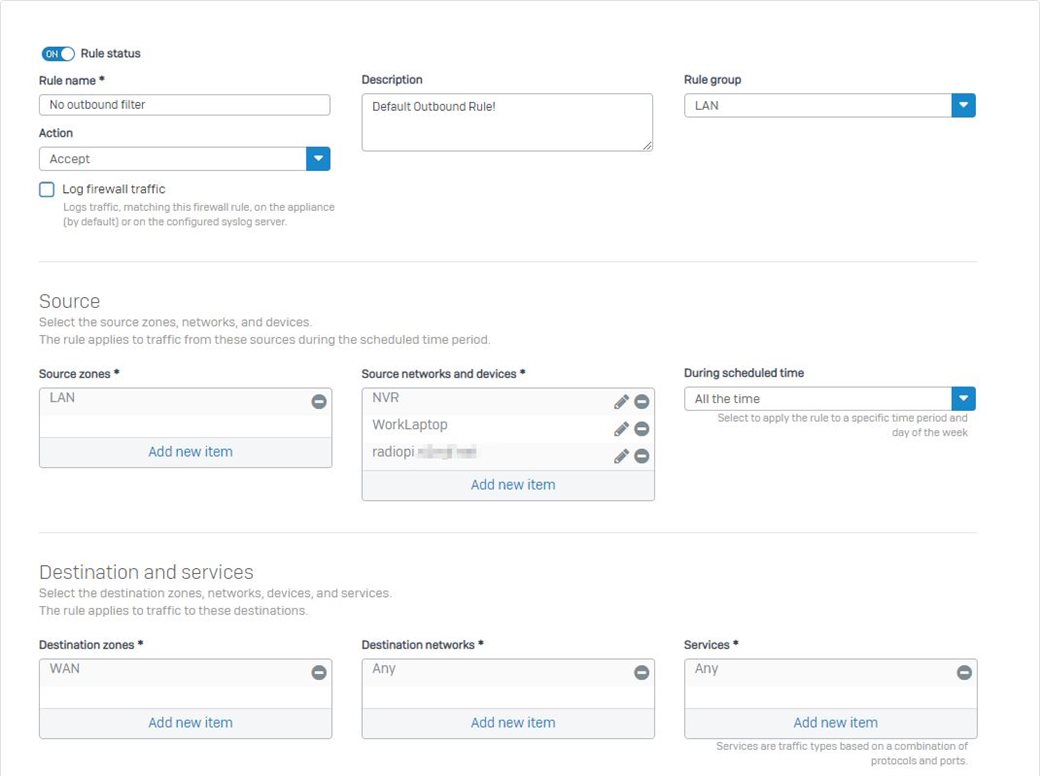
I have recently upgraded my home firewall to v18 EAP3 and since then, I can no longer connect to my work's VPN from my work laptop. My work (sadly) uses SonicWall Global VPN client (UDP500) and I've created a rule specific to the static LAN IP of my company laptop.
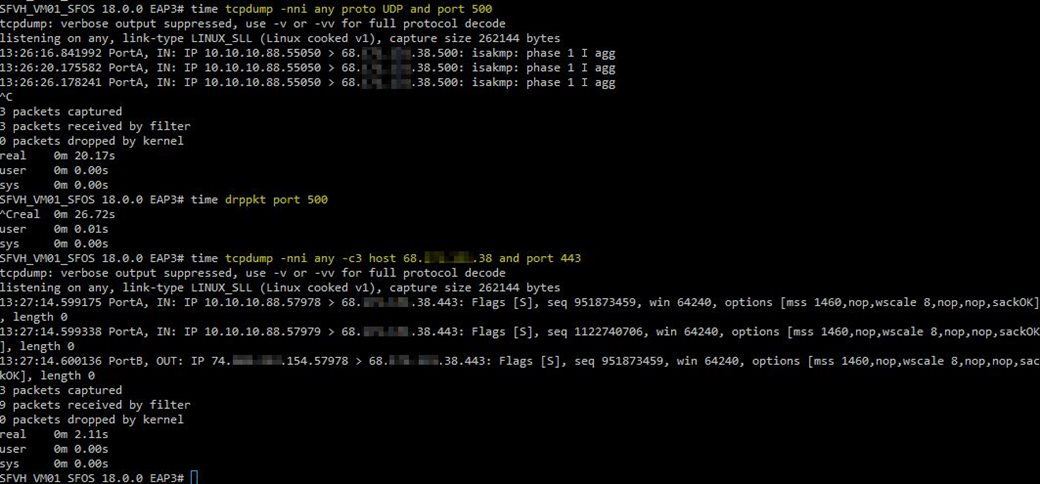
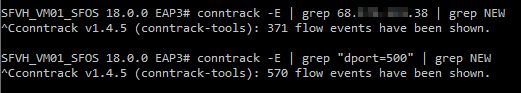
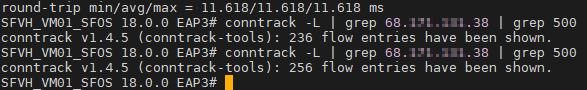
A packet capture shows my laptop attempting to connect to the remote host on the LAN interface but not forwarding through to the internet. Ironically, if I try to access the same IP via HTTPS, it forwards right through.
Has anyone else had any issues with v18 EAP3 not forwarding outbound UDP port 500?
Thanks all!