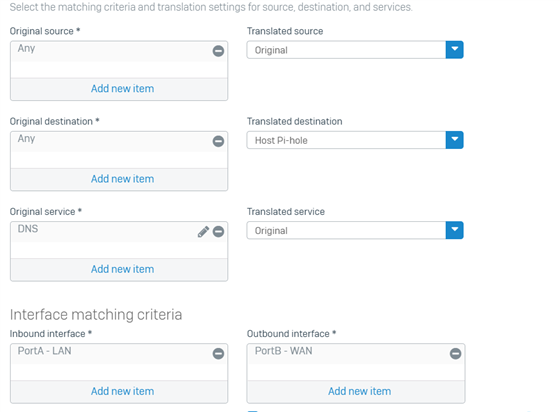
With the new NAT rules I want to redirect all DNS traffic in my network to a DNS server no matter what DNS settings has each device.
I have configured a NAT rules like this, but still devices like Alexa still call directly to 8.8.8.8 bypassing the NAT rule and my DNS server.
Why the v17.5 it wasn't possible but I'm wondering if it's possible now the new NAT options.
This is what I have configured as a NAT rule but doesn't work
Possible solution
I believe the issue is your pihole is also getting caught in this rule: it tries to perform a DNS request, gets its own traffic destination DNAT'ed to itself, and fails to lookup (or performs a loop). Unfortunately there is not a "exception" original source for the DNAT rule. I just resolved this issue by having my pihole have a dedicated interface (a VLAN subinterface), and have the inbound interface be everything except the interface of the pihole.
I don't have "post reply" permissions for some reason, so I could not post a comment/reply to the issue thread.
h
[edited by: l0rdraiden at 11:59 AM (GMT -8) on 28 Nov 2020]