What feature is impacted?
ConnectWise/ScreenConnect remote admin sessions from behind Sophos XG firewall
What is the severity of the issue? (High, medium, low, minimal)
HIGH
Summary of the issues:
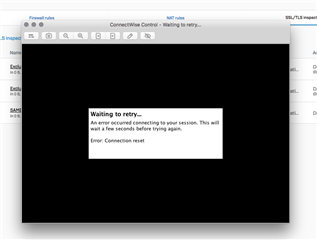
When attempting to remote control a PC using the ScreenConnect service by ConnectWise (screenconnect.com) using a PC behind a Sophos XG firewall running SFOS v18 EAP2
the machine will fail to be able to negotiate a session with the remote PC via the ConnectWise Control client app.
Observed behavior (What it did or didn’t do):
ConnectWise Control app would attempt to connect but retry repeatedly ending in failure.
Desired behavior (How is it expected to or should behave):
Should work as it did prior to v18 EAP2.
How do we reproduce it (Provide instructions to help us reproduce the behavior):
Obtain an account at screenconnect.com, add some PCs you wish to remote control, attempt to remote control from behind a Sophos XG, observe failure.
Other (Any other detail that we need to know about):
Turning SSL/TLS Inspection off temporarily will allow this to work
Supporting logs, pcaps, etc.:
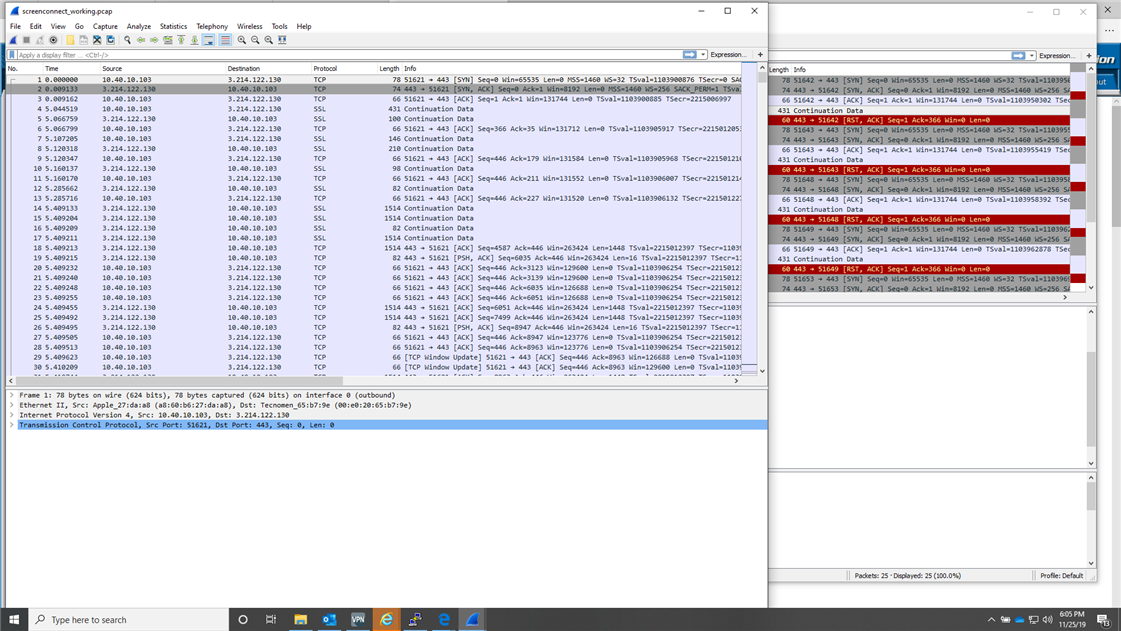
Will do some pcap for you but it won't be easy since you broke the pcap facility in EAP 2.
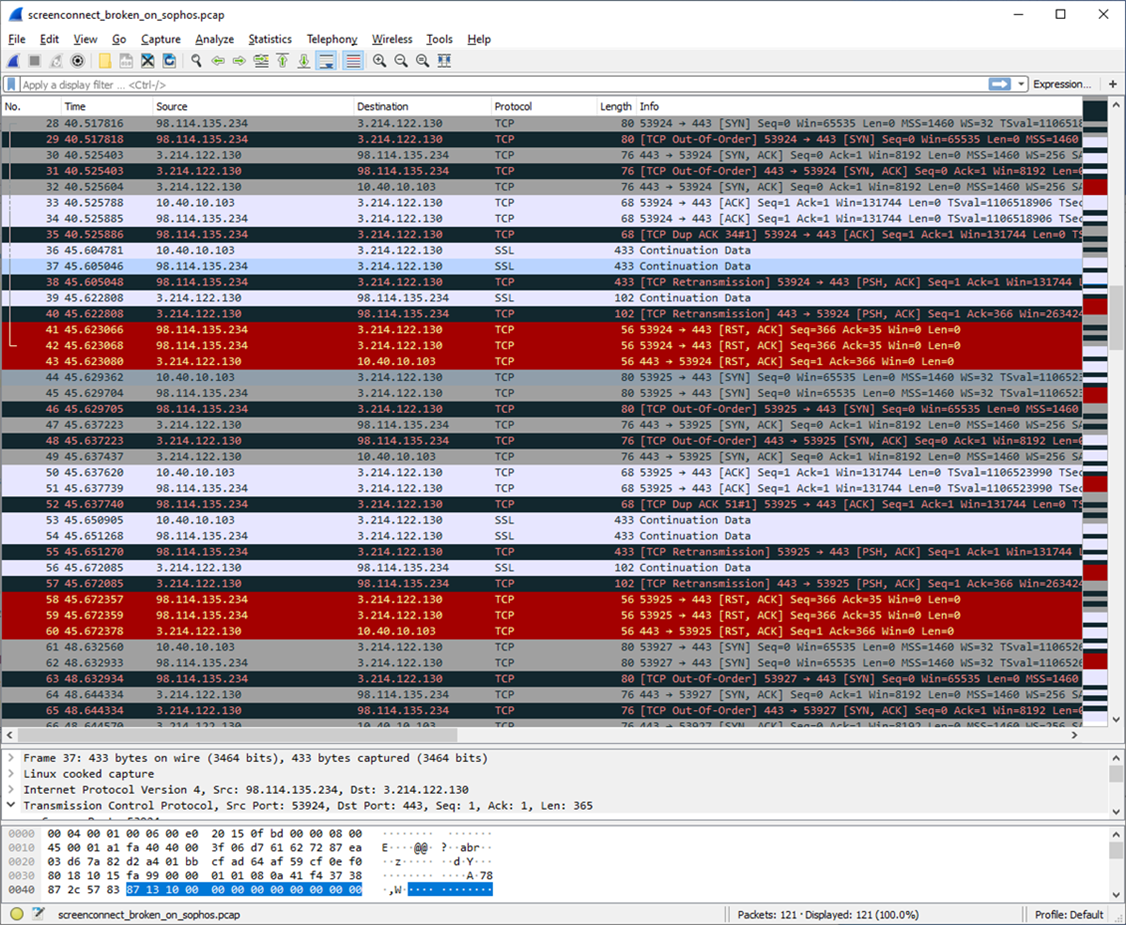
Here are some screen shots of Wireshark, PM with an e-mail address if you would like the actual pcap files...
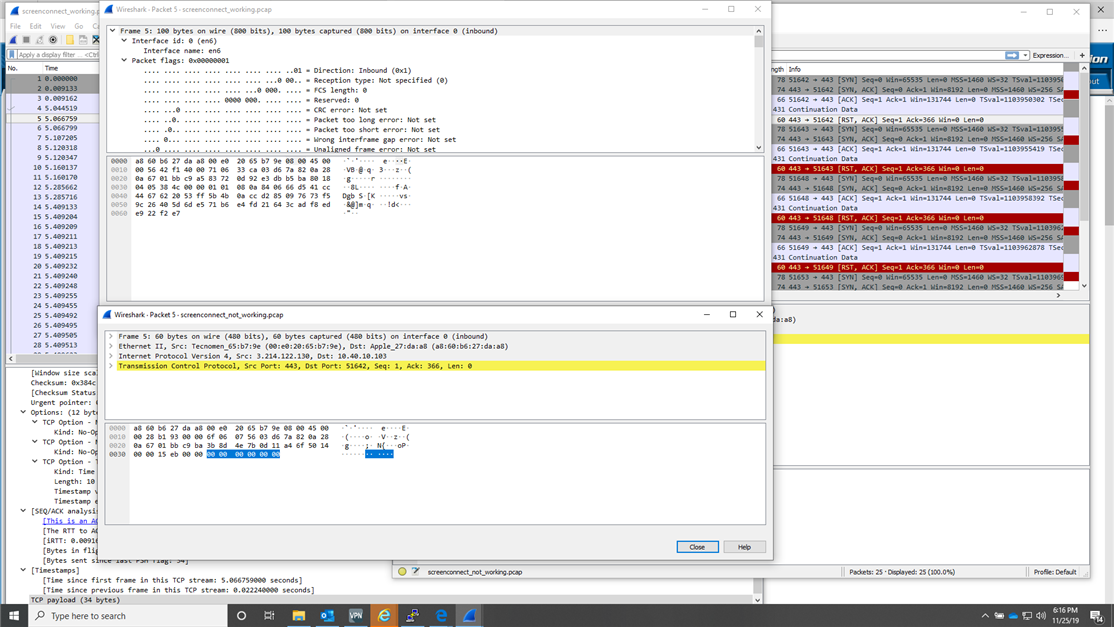
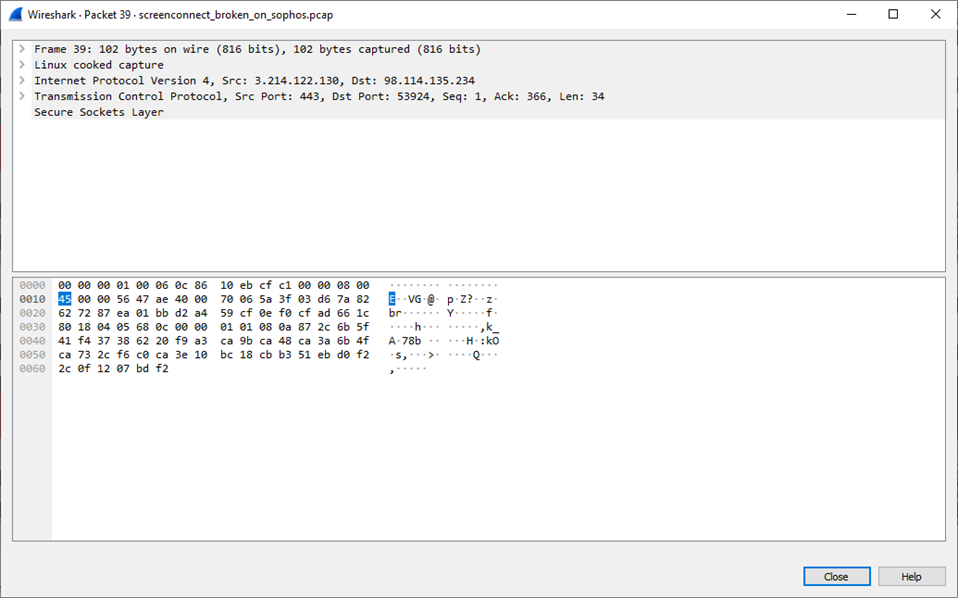
The problem lies in the response we get from ScreenConnect when SSL/TLS is enabled on the firewall. It appears that we lose 40 bytes somewhere in the translation...
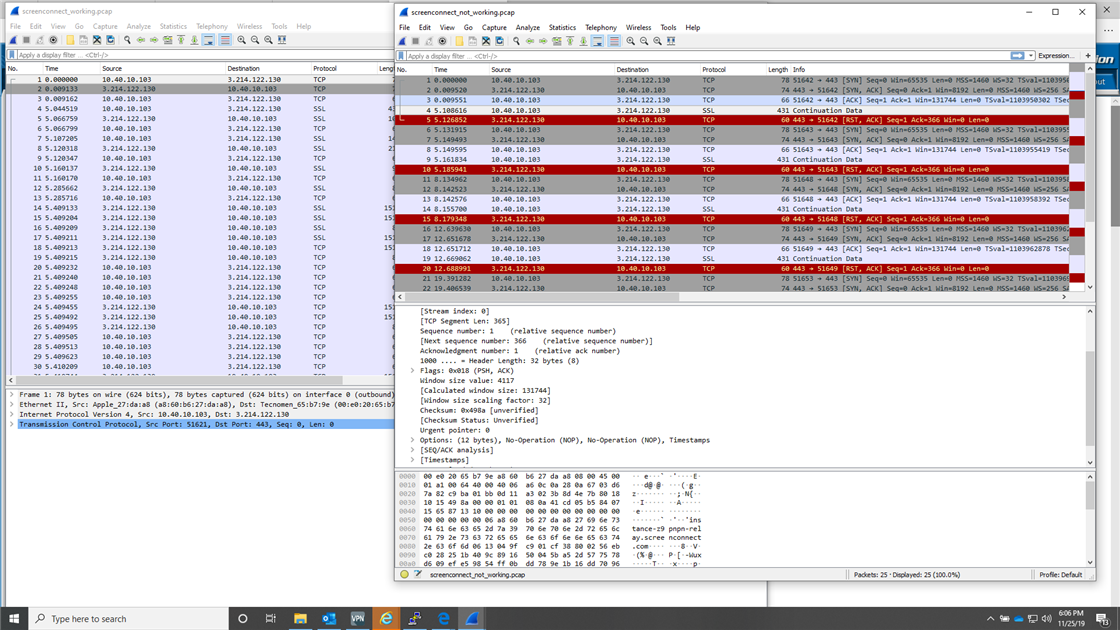
This is interesting, I took a packet capture at the firewall to see what was going on between AWS and it...
Looks like the packets are being sent to the destination twice, once without NAT and once with?!?!?!?
Also interesting is the fact that the response from AWS isn't getting truncated here, only when it gets to the client behind the firewall.
Note that the response packet at the firewall is still the proper size and contains all of the data...