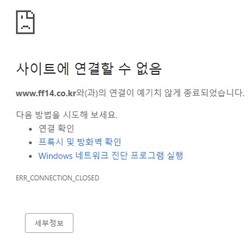
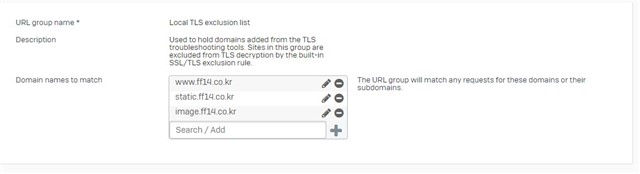
web browser: Chrome or Edge Dev or Firefox
target: https://www.ff14.co.kr/
result: ERR_CONNECTION_CLOSED
When I turn on the DPI engine, I can access the website. But when I turn the web filter off or on, I can't access it.
Packet dump and conntrack is assured for destination site.
SFVH_SO01_SFOS 18.0.0 EAP2# tcpdump -ni any net 183.111.190.0/24tcpdump: verbose output suppressed, use -v or -vv for full protocol decodelistening on any, link-type LINUX_SLL (Linux cooked), capture size 262144 bytes16:54:52.763716 Port1, IN: IP 192.168.144.200.10976 > 183.111.190.21.443: Flags [S], seq 3996659147, win 64240, options [mss 1460,nop,wscale 8,nop,nop,sackOK], length 016:54:52.764225 Port4, OUT: IP 221.154.6.91.10976 > 183.111.190.21.443: Flags [S], seq 3996659147, win 64240, options [mss 1460,nop,wscale 8,nop,nop,sackOK], length 016:54:52.767270 Port4, IN: IP 183.111.190.21.443 > 221.154.6.91.10976: Flags [S.], seq 1255700950, ack 3996659148, win 8192, options [nop,nop,sackOK,nop,wscale 9], length 016:54:52.767512 Port1, OUT: IP 183.111.190.21.443 > 192.168.144.200.10976: Flags [S.], seq 1255700950, ack 3996659148, win 8192, options [nop,nop,sackOK,nop,wscale 9], length 016:54:52.780719 Port1, IN: IP 192.168.144.200.10976 > 183.111.190.21.443: Flags [.], ack 1, win 1025, length 016:54:52.780939 Port4, OUT: IP 221.154.6.91.10976 > 183.111.190.21.443: Flags [.], ack 1, win 1025, length 016:54:52.781275 Port1, IN: IP 192.168.144.200.10976 > 183.111.190.21.443: Flags [P.], seq 1:518, ack 1, win 1025, length 51716:54:52.781377 Port1, OUT: IP 183.111.190.21.443 > 192.168.144.200.10976: Flags [.], ack 518, win 128, length 016:54:52.781990 Port4, OUT: IP 221.154.6.91.10976 > 183.111.190.21.443: Flags [.], seq 1:217, ack 1, win 256, length 21616:54:52.782020 Port4, OUT: IP 221.154.6.91.10976 > 183.111.190.21.443: Flags [.], seq 217:433, ack 1, win 256, length 21616:54:52.782040 Port4, OUT: IP 221.154.6.91.10976 > 183.111.190.21.443: Flags [P.], seq 433:518, ack 1, win 256, length 8516:54:52.785490 Port4, IN: IP 183.111.190.21.443 > 221.154.6.91.10976: Flags [F.], seq 1, ack 518, win 43007, length 016:54:52.785558 Port4, OUT: IP 221.154.6.91.10976 > 183.111.190.21.443: Flags [.], ack 2, win 256, length 016:54:52.785791 Port1, OUT: IP 183.111.190.21.443 > 192.168.144.200.10976: Flags [F.], seq 1, ack 518, win 128, length 016:54:52.786649 Port1, IN: IP 192.168.144.200.10976 > 183.111.190.21.443: Flags [.], ack 2, win 1025, length 016:54:52.786810 Port1, IN: IP 192.168.144.200.10976 > 183.111.190.21.443: Flags [F.], seq 518, ack 2, win 1025, length 016:54:52.786872 Port1, OUT: IP 183.111.190.21.443 > 192.168.144.200.10976: Flags [.], ack 519, win 128, length 016:54:52.786960 Port4, OUT: IP 221.154.6.91.10976 > 183.111.190.21.443: Flags [F.], seq 518, ack 2, win 256, length 016:54:52.787223 Port1, IN: IP 192.168.144.200.10977 > 183.111.190.21.443: Flags [S], seq 2813204329, win 64240, options [mss 1460,nop,wscale 8,nop,nop,sackOK], length 016:54:52.787529 Port4, OUT: IP 221.154.6.91.10977 > 183.111.190.21.443: Flags [S], seq 2813204329, win 64240, options [mss 1460,nop,wscale 8,nop,nop,sackOK], length 016:54:52.789020 Port4, IN: IP 183.111.190.21.443 > 221.154.6.91.10976: Flags [.], ack 518, win 43007, length 016:54:52.789911 Port4, IN: IP 183.111.190.21.443 > 221.154.6.91.10976: Flags [.], ack 519, win 43007, length 016:54:52.790539 Port4, IN: IP 183.111.190.21.443 > 221.154.6.91.10977: Flags [S.], seq 2922211172, ack 2813204330, win 8192, options [nop,nop,sackOK,nop,wscale 9], length 016:54:52.790837 Port1, OUT: IP 183.111.190.21.443 > 192.168.144.200.10977: Flags [S.], seq 2922211172, ack 2813204330, win 8192, options [nop,nop,sackOK,nop,wscale 9], length 016:54:52.795489 Port1, IN: IP 192.168.144.200.10977 > 183.111.190.21.443: Flags [.], ack 1, win 1025, length 016:54:52.795688 Port4, OUT: IP 221.154.6.91.10977 > 183.111.190.21.443: Flags [.], ack 1, win 1025, length 016:54:52.795761 Port1, IN: IP 192.168.144.200.10977 > 183.111.190.21.443: Flags [P.], seq 1:214, ack 1, win 1025, length 21316:54:52.795900 Port1, OUT: IP 183.111.190.21.443 > 192.168.144.200.10977: Flags [.], ack 214, win 128, length 016:54:52.808413 Port4, OUT: IP 221.154.6.91.10977 > 183.111.190.21.443: Flags [P.], seq 1:214, ack 1, win 256, length 21316:54:52.819986 Port4, IN: IP 183.111.190.21.443 > 221.154.6.91.10977: Flags [.], ack 214, win 43008, length 016:54:52.831775 Port4, IN: IP 183.111.190.21.443 > 221.154.6.91.10977: Flags [.], seq 1:1461, ack 214, win 43008, length 146016:54:52.831776 Port4, IN: IP 183.111.190.21.443 > 221.154.6.91.10977: Flags [.], seq 1461:2921, ack 214, win 43008, length 146016:54:52.831777 Port4, IN: IP 183.111.190.21.443 > 221.154.6.91.10977: Flags [P.], seq 2921:4075, ack 214, win 43008, length 115416:54:52.831955 Port1, OUT: IP 183.111.190.21.443 > 192.168.144.200.10977: Flags [P.], seq 1:67, ack 214, win 128, length 6616:54:52.832388 Port4, OUT: IP 221.154.6.91.10977 > 183.111.190.21.443: Flags [.], ack 2921, win 256, length 016:54:52.832853 Port1, OUT: IP 183.111.190.21.443 > 192.168.144.200.10977: Flags [.], seq 67:1527, ack 214, win 128, length 146016:54:52.832942 Port1, OUT: IP 183.111.190.21.443 > 192.168.144.200.10977: Flags [.], seq 1527:2987, ack 214, win 128, length 146016:54:52.833019 Port1, OUT: IP 183.111.190.21.443 > 192.168.144.200.10977: Flags [P.], seq 2987:4075, ack 214, win 128, length 108816:54:52.833181 Port1, IN: IP 192.168.144.200.10977 > 183.111.190.21.443: Flags [.], ack 2987, win 1025, length 016:54:52.833220 Port1, IN: IP 192.168.144.200.10977 > 183.111.190.21.443: Flags [.], ack 4075, win 1025, length 016:54:52.833699 Port4, OUT: IP 221.154.6.91.10977 > 183.111.190.21.443: Flags [.], ack 2987, win 1025, length 016:54:52.833807 Port4, OUT: IP 221.154.6.91.10977 > 183.111.190.21.443: Flags [.], ack 4075, win 1025, length 016:54:52.874368 Port1, IN: IP 192.168.144.200.10977 > 183.111.190.21.443: Flags [P.], seq 214:340, ack 4075, win 1025, length 12616:54:52.874731 Port4, OUT: IP 221.154.6.91.10977 > 183.111.190.21.443: Flags [P.], seq 214:340, ack 4075, win 1025, length 12616:54:52.877280 Port4, IN: IP 183.111.190.21.443 > 221.154.6.91.10977: Flags [P.], seq 4075:4126, ack 340, win 43008, length 5116:54:52.877492 Port1, OUT: IP 183.111.190.21.443 > 192.168.144.200.10977: Flags [P.], seq 4075:4126, ack 340, win 43008, length 5116:54:52.877823 Port1, IN: IP 192.168.144.200.10977 > 183.111.190.21.443: Flags [F.], seq 340, ack 4126, win 1025, length 016:54:52.877923 Port4, OUT: IP 221.154.6.91.10977 > 183.111.190.21.443: Flags [F.], seq 340, ack 4126, win 1025, length 016:54:52.880353 Port4, IN: IP 183.111.190.21.443 > 221.154.6.91.10977: Flags [.], ack 341, win 43008, length 016:54:52.880463 Port1, OUT: IP 183.111.190.21.443 > 192.168.144.200.10977: Flags [.], ack 341, win 43008, length 016:54:52.880896 Port4, IN: IP 183.111.190.21.443 > 221.154.6.91.10977: Flags [R.], seq 4126, ack 341, win 43008, length 016:54:52.881032 Port1, OUT: IP 183.111.190.21.443 > 192.168.144.200.10977: Flags [R.], seq 4126, ack 341, win 43008, length 0^C52 packets captured68 packets received by filter7 packets dropped by kernelSFVH_SO01_SFOS 18.0.0 EAP2#
SFVH_SO01_SFOS 18.0.0 EAP2# conntrack -L -d 183.111.190.21proto=tcp proto-no=6 timeout=7 state=CLOSE orig-src=192.168.144.200 orig-dst=183.111.190.21 orig-sport=11358 orig-dport=443 packets=6 bytes=591 reply-src=183.111.190.21 reply-dst=221.154.6.91 reply-sport=443 reply-dport=11358 packets=8 bytes=4453 [ASSURED] mark=0x4003 use=3 id=1342324224 masterid=0 devin=Port1 devout=Port4 nseid=3910 ips=0 sslvpnid=0 webfltid=0 appfltid=0 icapid=0 policytype=1 fwid=1 natid=4 fw_action=1 bwid=0 appid=100 appcatid=5 hbappid=0 hbappcatid=0 dpioffload=0x21 inzone=1 outzone=2 devinindex=5 devoutindex=8 hb_src=0 hb_dst=0 flags0=0x400a0080200000 flags1=0x1c100890000 flagvalues=21,31,41,43,54,80,83,87,96,102,103,104 catid=22 user=0 luserid=0 usergp=0 hotspotuserid=0 hotspotid=0 dst_mac=00:50:56:ba:0f:2a src_mac=88:d7:f6:41:c6:84 startstamp=1574582312 microflowid[0]=547 microflowrev[0]=34 microflowid[1]=256 microflowrev[1]=33 hostrev[0]=2 hostrev[1]=2 ipspid=0 diffserv=0 loindex=8 tlsruleid=0 ips_nfqueue=1 sess_verdict=0 gwoff=0 cluster_node=0 current_state[0]=1761 current_state[1]=1761 vlan_id=0 inmark=0x0 brinindex=0 sessionid=407 sessionidrev=33901 session_update_rev=7 dnat_done=0 upclass=0:0 dnclass=0:0 pbrid_dir0=3 pbrid_dir1=0 nhop_id[0]=11 nhop_id[1]=22 nhop_rev[0]=0 nhop_rev[1]=0 conn_fp_id=NOT_OFFLOADEDproto=tcp proto-no=6 timeout=7 state=TIME_WAIT orig-src=192.168.144.200 orig-dst=183.111.190.21 orig-sport=11357 orig-dport=443 packets=5 bytes=729 reply-src=183.111.190.21 reply-dst=221.154.6.91 reply-sport=443 reply-dport=11357 packets=4 bytes=168 [ASSURED] mark=0x4003 use=3 id=1342323904 masterid=0 devin=Port1 devout=Port4 nseid=4271 ips=0 sslvpnid=0 webfltid=0 appfltid=0 icapid=0 policytype=1 fwid=1 natid=4 fw_action=1 bwid=0 appid=100 appcatid=5 hbappid=0 hbappcatid=0 dpioffload=0x1 inzone=1 outzone=2 devinindex=5 devoutindex=8 hb_src=0 hb_dst=0 flags0=0x400a0080200000 flags1=0x1c000890000 flagvalues=21,31,41,43,54,80,83,87,102,103,104 catid=22 user=0 luserid=0 usergp=0 hotspotuserid=0 hotspotid=0 dst_mac=00:50:56:ba:0f:2a src_mac=88:d7:f6:41:c6:84 startstamp=1574582312 microflow[0]=INVALID microflow[1]=INVALID hostrev[0]=1 hostrev[1]=1 ipspid=0 diffserv=0 loindex=8 tlsruleid=0 ips_nfqueue=0 sess_verdict=0 gwoff=0 cluster_node=0 current_state[0]=1761 current_state[1]=1761 vlan_id=0 inmark=0x0 brinindex=0 sessionid=409 sessionidrev=33933 session_update_rev=5 dnat_done=0 upclass=0:0 dnclass=0:0 pbrid_dir0=3 pbrid_dir1=0 nhop_id[0]=11 nhop_id[1]=22 nhop_rev[0]=0 nhop_rev[1]=0 conn_fp_id=NOT_OFFLOADEDconntrack v1.4.5 (conntrack-tools): 2 flow entries have been shown.