Running v18 EAP1:
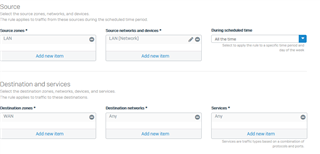
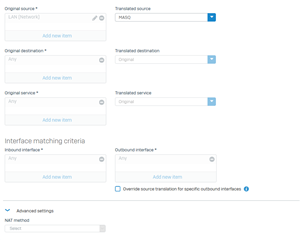
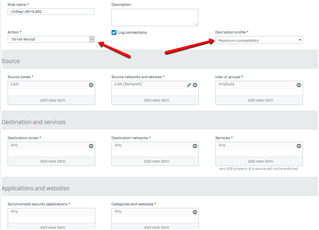
Have simple firewall rule, which allows traffic to the Internet, there are NO security features setup on XG in the rule, only a NAT:
I have a Playstation on the LAN and also a server that sends out to PushOver, now the Playstation cannot connect to the playstation network, and Pushover is being stopped, I get this from ex. Pushover:
"The request was aborted: Could not create SSL/TLS secure channel."
I have disabled SSL inspection also on XG.
Some services work, but others don't on the network.
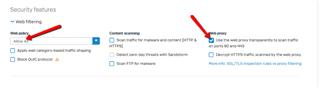
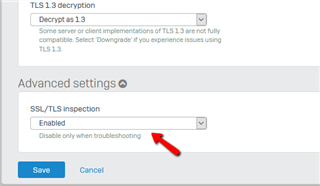
I found out, that if I go and enable this:
Everything works again!
What could be wrong here?
With 17.5.8 I had the same rule, with no security enabled, no issues here.
The sometimes I can disable the proxy again, and it keeps working, just as if it hold the connection.
Would make sense if the SSL inspection on/off was broken, and it was still on, but I cannot understand why SSL/TLS is broken, with it all disabled :-)